
We’ve just detected a wave of mp3 spam. There aren’t any links in the message: all the information is in the audio file attached to the message.
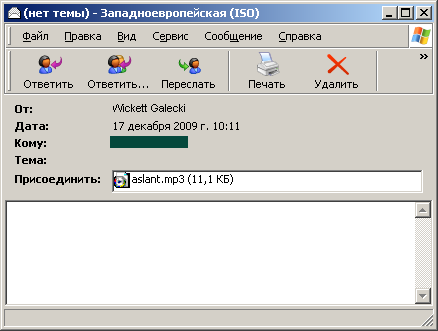
Play the file, and you get 4 seconds of a female voice giving a web address for Viagra and similar medications. In the background there are passionate sighs and groans (presumably to persuade you that by purchasing Viagra, you’ll reach unparalleled heights of bliss!)
Just in case you can’t make out what the woman’s saying, the key words ‘CHEAP VIAGRA’ and the site address are included in the name of the track.
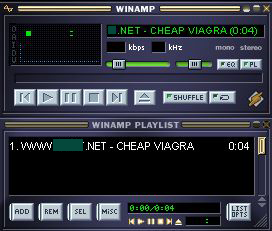
Spam in mp3 format first appeared in autumn 2007, pushing pump and dump shares. Audio spam never took off because of a whole range of limitations such as the large file size, and the poor quality of the recordings. Today’s mailing, though, shows that spammers are having another go at using this technique to push their goods and services.




















The return of mp3 spam