
In their attempts to bypass e-mail filtering systems and deliver their information to users, spammers often resort to all sorts of tricks. Although really new tricks (such as distributing mp3 files with voice-generated messages) are relatively uncommon, sometimes they do come up.
Kaspersky Lab analysts have recently come across a few curious samples. While masking text with noise is nothing out of the ordinary, the links were arranged in a rather unusual way.
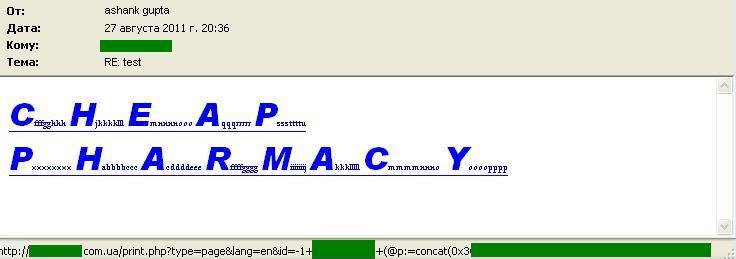
The trick itself turned out to be rather simple and has been relatively harmless so far: a URL in the message is a request to a website that is vulnerable to SQL injection. The code yields one string, which is a spam link (in this case, a typical pharmacy ad). This is where the browser is redirected – naturally, if the original site allows such code to be executed.
Some instances we encountered during a week of observations demonstrate that following a large-scale SQL-attack LizaMoon many website owners took relevant security measures and finding suitable “donors” on a mass scale was not at all that simple.




















SQL for dummies