
Kaspersky Lab experts refer to spam as anonymous unsolicited mass mailings. Most of these mailings are adverts, although several categories of spam serve other purposes. “Non-advertising” spam includes one of the most dangerous types of spam – fraudulent messages.
State-of-the-art spam technologies allow spammers to send emails containing fake messages, insert fake sender addresses and use infected machines to send out spam. Unsurprisingly, the use of spam to trick users, as well as the ability to conceal such activity, attracts cybercriminals and fraudsters of all types.
The anonymity of spam, i.e., the inability to easily detect those initiating mass mailings, means that cybercriminals can act with impunity, further contributing to the criminalization of spam. The services offered by spammers are actively used by sellers of counterfeit and fake products, those offering illegal services and virus writers.
This article describes fraudulent spam messages that are sent with the aim of stealing a user’s money or gaining access to personal information which can be used for the same purpose.
Phishing
Phishing is the term used for the most hostile type of fraudulent spam.
Phishing messages are used by spammers to obtain personal data – user logins, passwords, credit card numbers and PINs – with the aim of stealing money. Most often, phishing attacks target clients of online banking and e-pay systems.
Phishing messages imitate the correspondence of legitimate organizations (banks, financial companies, or payment systems). Unlike legitimate messages, however, phishing messages usually encourage recipients to “confirm” their personal data on some pretext or other. These messages contain a link to a fake page where users are asked to enter their personal data, which will then fall into the hands of criminals. The fake page is usually an exact copy of the official site of the organization that supposedly sent the message (the sender’s address is also false) so that users do not suspect anything.
In some cases after the user enters his data the browser redirects to the genuine site, making it even more unlikely that the victim will suspect anything is wrong.
Another variant of phishing entails an imitation web page using vulnerabilities in the software installed on a user’s computer to download a Trojan program, which then collects various data (e.g., passwords for bank accounts) and passes it on to its “owner”. In addition, a machine that is infected in this way may become part of a zombie network and used for cyber attacks or sending spam.
To deceive those users who not only pay attention to the design of the page but to the addresses of the sites they visit, spammers mask the URLs making them look as close to the original as possible. Phishing started with the registration of domain names similar to the domain names of the targeted sites on free web hosting services, but over time more sophisticated methods have emerged.
The message below addressed to PayPal clients is an example of the most common tactic of masking.

Only a very attentive user who places the cursor over the link contained in the message will notice that it in fact leads to a phishing site. The link looks very similar to the address of the legitimate site but the domain is different – client-confirmation.com.

In this particular instance the “wrong” address can be viewed by positioning the cursor over the link contained in the message. More advanced users will be able to recognize the illegitimate link before clicking on it.
As well as contrived tricks of this sort, there are more primitive methods of deceiving users. For instance, when a user receives a message sent on behalf of the site administration or technical support service asking him on some pretext or other to immediately send the password to his account to the address indicated in the message. The user is warned that if he fails to do so, his account will be terminated.
Phishers on the Russian-language Internet use this trick to access users’ email accounts. Control over a user’s email enables cybercriminals to gain access to the victim’s personal data on other Internet services by requesting new passwords for those services.

TRANSLATION:
Due to updates carried out to our databases we request that you repeat the authorization process for our mail server to avoid losing your mail account. We apologize for any inconvenience!
Authorization
Enter your password and click “answer”
The password must be entered exactly as it was at registration, using capital or small letters in the same register that was used during registration (if your keyboard was switched to Russian or CapsLock was turned on, use the same regime or select from the following combinations [Rus], [CapsLock], [CapsLock + Rus] as well as various Russian language codes)
If you have additional Mail. Ru accounts, we recommend that you include data for those accounts to include them in our new "spam blocker" system.
1999-2008, Mail.Ru
Registration User community
Another widespread method of collecting email passwords is to send out messages with offers to take advantage of a “vulnerability in the password backup system” which can be used to find out another user’s password. To access another user’s account the recipient of the spam message has to send the victim’s login and his own password to a specified address and in a certain format. It goes without saying that the would-be “hunter” becomes the victim of cybercriminals when he falls for a dubious offer of this kind.
However, over time users have learnt that respectable organizations never ask them for their passwords, so the effectiveness of these tricks has declined. Spammers have had to become more inventive when masking fake messages, and as a result it has become more difficult for recipients to distinguish them from legitimate messages.
In general, phishing attacks target Western online payment systems and online banks with large numbers of clients. However, phishers are currently targeting online banks on the Russian-language Internet.
A phishing attack that targeted Alfa Bank clients is the most typical illustration of the above. The cybercriminals used the standard scheme: they sent messages that appeared to be from the bank administration containing a link to the fake site, where the user was asked to enter his login and password to access the Internet banking system. The layout of the page looked just like Alfa Bank’s home page. The cybercriminals had another surprise in store for any users careless enough to click on the link – a malicious program that downloaded to the victim’s computer. The same method was used to attack the WebMoney and Yandex.Money systems. Citibank was also targeted by phishing attacks.
Cybercriminals have also tried on a number of occasions to gain access to email accounts by pretending to be from the Russian email system administration and asking users for their logins and passwords.
Extorting money via spam
In addition to phishing, cybercriminals make use of lots of other tricks to catch out hapless users. More often than not spammers play upon the victim’s naivety, greed and love for freebies, though this is typical of all conmen. To achieve their goals cybercriminals have come up with various techniques. We will look at the most popular methods in more detail.
Nigerian email fraud
As the name suggests, this technique was developed by Nigerian cybercriminals, although it is now being used by others all over the world.
The classical Nigerian scam usually follows the same scenario: spammers send messages on behalf of a representative of a wealthy family (usually African) deposed after either a civil war, coup d’etat, economic crisis or political repressions. These messages are usually written in bad English asking a recipient to assist in retrieving a large sum of money by making a money transfer from one bank account to another. In return the sender offers a share of the money, usually a percentage of the transferred sum. In the course of the “rescue mission” a voluntary (but by no means disinterested) assistant is needed to pay certain fees (to cover the costs of the money transfer or legal fees, etc.). The sum is relatively small compared to the supposed payoff, but after the transaction all contact with the “widow of the deposed dictator” or the “son of the late deposed prime minister” is lost. Sometimes the victim is kept waiting for the promised money transfer, with further requests for more money to overcome unforeseen problems.
In some cases the sender introduces himself as a high-ranking corrupt government official, who has embezzled funds and is now on remand so cannot take his money out of the country. In order to make a wire transfer he needs access to a bank account. The recipient is offered a percentage for his assistance, but when the cybercriminal gets control of the account he steals all the money from it.
The stories used by Nigerian scammers are so creative that they were even awarded the 2005 Anti-Nobel prize in Literature! Russia too has been affected by these types of scams. In 2005, typical Nigerian scam messages were sent in English on behalf of the relatives and friends of the deposed oligarch Mikhail Khodorkovsy. That was the only distinctly Russian aspect to the scam; the rest did not differ from the usual tactics.
I am Lagutin Yuriy and I represent Mr. Mikhail Khordokovsky the former C.E.O of Yukos Oil Company in Russia. I have a very sensitive and confidential brief from this top (Oligarch) to ask for your partnership in re-profiling funds over US$450 million. I will give the details, but in summary, the funds are coming via Bank Menatep. This is a legitimate transaction. You will be paid 4% for your “Management Fees”.
If you are interested, please write back by email and provide me with your confidential telephone number, fax number and email address and I will provide further details and instructions. Please keep this confidential; we can’t afford more political problems. Finally, please note that this must be concluded within two weeks. Please write back promptly.
Write me back. I look forward to it.
Regards,
Lagutin Yuriy
There is also a romantic variant of the Nigerian scam involving messages from brides in exotic countries with a photo of a pretty African lady attached. Generally, scammers target users registered on online dating sites. If a potential victim gets involved in correspondence, he is offered a touching story worthy of a soap opera: my relatives were killed; I am not allowed to leave the country; I am in fact a rich heiress… In the third message the girl is already swearing her undying love, asking the “hero” to help her leave the country with her millions and get a generous reward. However, this romantic story is a mask for the standard Nigerian fraud technique. Needless to say, the “assistant” has to pay some preliminary costs that can amount to thousands and even tens of thousand dollars. To make it more convincing, “a pastor” or “an attorney” participates in the deal. The final stage of the affair includes forged papers.
Fake lottery wins
This type of scam is similar to the Nigerian email fraud. Recipients get fake notifications stating that they have won a lottery that draws winners at random from email addresses or telephone numbers, and are offered “free” presents as a prize. To make the message look more convincing the scammers may add a photo of the prize, a lottery ticket number, a certificate of registration/license and other fake information. As in the previous case, to receive the prize the recipient has to make a money transfer to the account indicated in the message.
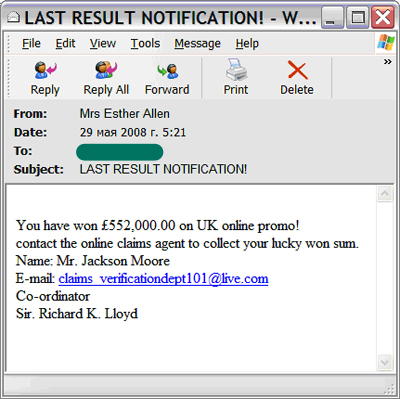
There were also Russian-language versions of such messages. The text in these messages was translated from the English-language originals using an online translator.
Recipients of such notifications must clearly understand that participation in any lottery is impossible without the user’s consent. If you have not given your consent (and more often than not, you know nothing about the lottery you have supposedly won), you are most likely being targeted by conmen who are trying to extort money from you and other Internet users.
“Mistakes” in payment systems, “magic purses”, code generators
This type of spam informs the recipient about a vulnerability discovered in a payment system, which makes it possible to derive a profit. The spammers describe the vulnerability and offer a method for obtaining money, which generally includes sending a certain sum to the “magic purse”. A user is offered a payment of more than double the transferred sum. Needless to say, the “magic purse” belongs to cybercriminals and the user will never see either his money or the promised payment. Moreover, the victims are hardly likely to report the scam to law enforcement agencies.
Yet another freebie type of fraud is the offer of credit card generators – systems for skimming money from other people’s accounts. The key point here is to make those users that can’t resist a freebie to enter their credit card/epay number and password to activate the program. Such programs usually have to be paid for, but the user is informed that 1-3 accounts can be skimmed for free. While the user is trying to steal from someone else’s account, the data he has entered is passed to cybercriminals, who use it to access his account.
The scheme which cybercriminals use when offering card generators to pay for mobile or Internet services is the same as the previous one, but in this case the code of a non-activated card has to be entered into a “card generator”. This code will become a sort of model for “multiplication”. As in the case with credit cards, the entered data becomes the property of the cybercriminals and the program imitates the calculating process. While a victim is waiting for the results, the cybercriminals are paying their bills using the victim’s “master” card.
Casinos with holes
Another type of scam sees users receiving a message with the following content: “After long hours of playing we have discovered a hole in the script, which makes it possible to win in an online casino. Surprisingly, the administrators have not noticed it yet!” There then comes a detailed description of the “winning” strategy and the link to the casino site. The reason for these messages has nothing to do with altruism, and the “hole in the script” does not exist. The fraudulent scheme works as follows: the user follows the link in the message and enters the casino site and the spammer gets a share of whatever the victim loses. Other messages contain an offer to download (sometimes to buy) and install a program, which makes it possible to use the vulnerability. The program turns out to be spyware, however.
Tempting quick profits
These scam messages usually begin by stating: “This is not spam. This is a profitable proposition, which is difficult to decline. This message is sent to you only once and if you ignore it you will regret the lost opportunity for the rest of your life”. The scheme described further in the text is nothing more than a financial pyramid: the user has to pay the author of the message (the curator) a certain sum of money and then forward this message to someone else, receiving the same sum from each addressee plus part of the profit from the “subordinates” on a lower level. This scheme promises each participant a fabulous income, but he only ends up losing money.
Job offers are a more effective way of extorting money. The scammers pretend to be employers and promise “potential employees” a high income for doing nothing in particular. Qualifications are not required, and after establishing contact with a potential victim, the scammers ask him to pay some startup costs for more detailed information and postal expenses. A user is encouraged to do this as quickly as possible because the vacancy may be occupied by someone else.
Sometimes scammers carry out targeted attacks, sending out “attractive offers” to the addresses of users registered on job search sites. Applicants are offered jobs in a real international company engaged in gold or diamond mining, manufacturing of medical equipment, the production of chemicals and vaccines, investment banking or the construction business, with options on a contract. The job that is offered is usually related to the applicant’s sphere of activity and requires his professionalism and experience. But inevitably there are “administrative expenses” and the victim’s money ends up in the scammer’s pocket.
Subject: Prospective Employee
Spiralnergy Exploration, UK is an oil and gas exploration and production company based in United Kingdom.
The Company’s producing properties and Exploration activities are focused on the UK Central North Sea.
The goal of Spiralnergy Exploration in the near term is to achieve oil production from its interests in the North Sea while carrying out an active exploration /development program on both its own properties and in various joint venture opportunities currently being considered by the Company.
Spiralnergy Exploration, UK hereby inform that, you have been shortlisted as one of the personnel/expatriate for our upcoming project schedule to commence March, 2008.
The project involves the construction of a new LPG(Liquefied Petroleum Gas ) Plant and Oil Wells at UK Central North Sea, UK.
You are hereby require to send your detailed resume and application via fax or email attachment to us in not later than 5(five) days of receiving this email.
All resumes/application should be in MS Word format.
Thanks for your interest.
William Peters
{Address}, UK
This email and any attachments to it contain information that is confidential and may be privileged. It is for the exclusive use of the intended recipient(s). If you are not the intended recipient(s) please note that any form of distribution, copying or use of this communication or the information contained in it is strictly prohibited and may be unlawful. If you have received this email in error, please return it to the sender (Spiralnergy Exploration) and delete the email from your records.
Blackmail
To extort money spammers not only use attractive offers but threats as well. Most often the threats are along the lines of: we will only stop sending spam if you pay us. But there are also more frightening variants like messages from a “killer” who wants money in exchange for the victim’s life.
Subject: BE WARNED!!!
I am very sorry for you Xxxxxx, is a pity that this is how your life is going to end as soon as you don’t comply. As you can see there is no need of introducing myself to you because I don’t have any business with you, my duty as I am mailing you now is just to KILL you and I have to do it as I have already been paid for that.
Someone you call a friend wants you Dead by all means, and the person have spent a lot of money on this, the person also came to us and told me that he wanted you dead and he provided us with your name ,picture and other necessary information’s we needed about you. So I sent my boys to track you down and they have carried out the necessary investigation needed for the operation on you, and they have done that but I told them not to kill you that I will like to contact you and see if your life is Important to you or not since their findings shows that you are innocent.
I called my client back and ask him of your email address which I didn’t tell him what I wanted to do with it and he gave it to me and I am using it to contact you now. As I am writing to you now my men are monitoring you and they are telling me everything about you.
Now do you want to LIVE OR DIE? As someone has paid us to kill you. Get back to me now if you are ready to pay some fees to spare your life, $4,000 is all you need to spend You will first of all pay $2,000 then I will send a tape to you which i recorded every discusion in
made with the person who wanted you dead and as soon as you get the tape, you will pay the remaining $2,000. If you are not ready for my help, then I will carry on with my job straight-up.
WARNING: DO NOT THINK OF CONTACTING THE POLICE OR EVEN TELLING ANYONE
BECAUSE I WILL KNOW.REMEMBER, SOMEONE WHO KNOWS YOU VERY WELL WANT YOU DEAD!
I WILL EXTEND IT TO YOUR FAMILY, INCASE I NOTICE SOMETHING FUNNY.
DO NOT COME OUT ONCE IT IS 7:PM UNTILL I MAKE OUT TIME TO SEE YOU AND GIVE
YOU THE TAPE OF MY DISCUSSION WITH THE PERSON WHO WANT YOU DEADTHEN YOU CAN
USE IT TO TAKE ANY LEGAL ACTION. GOOD LUCK AS I AWAIT YOUR REPLY EMAIL:donwilliam1@gmail.com
Sending text messages to short codes
The Russian Internet has recently been the site of more than just classic ploys from the Western segment of the Internet. Malicious users have successfully developed new means of swindling money out of Russian-speaking users. For example, fraud in which text messages are sent to short codes is currently very common on the Russian Internet. Short codes are leased out by cellular operators and people are charged money when they send a message to these numbers. Most of the money taken from mobile accounts in payment for texts sent to short codes is passed to the party leasing the code.
To achieve their goals scammers try different tricks, from offering free Internet access and all types of prizes, to direct threats of blocking a user’s mail box if he does not send an SMS message.

TRANSLATION:
We are notifying you that this morning, 6 April 2008, a spam mailing was sent from your email account.
Your email will be blocked for 24 hours in order to investigate the circumstances.
If you did not send the spam mailing and you do not want your email to be blocked, send an SMS to the number 1171 with the code =vips 1
The mail.ru robot will record your telephone number, whereupon you will be sent further instructions in an SMS message.
Otherwise, your account will be blocked by the anti-spam system.
We suggest you make your password more secure by changing it.v
Note! A fee of 2.9 rubles, including tax, is charged for the SMS.
There is no need to reply to any replies because they are sent by the robot!
Best regards,
Mail.ru Support Service
In one such mass mailing the recipients were even offered the option of unsubscribing from future mailings. The spammer assured them that he wanted to be a “law-abiding citizen” and, referring to the Russian Law on Advertising which came into force on July 1, 2007, he asked users to withdraw their addresses from spammer databases by sending a “free” SMS message. The spammer stated that after sending the SMS message users would get a link to the web page where they could find the spammer databases and delete their email details from them. Needless to say, the actual goal had nothing to do with abiding by the law.
More complex combinations may only involve a link to a special website, where a user (who is already involved in the process of receiving a prize, for example) is asked to send an SMS message to a short code. Such a long and sophisticated scheme is aimed at catching out even the most vigilant users.
Conclusion
Kaspersky Lab’s classification system assigns spam messages to the “Computer fraud” category, whose share amounted to 7% of the total quantity of spam in 2007. In the first quarter of 2008 this figure plummeted to 2.5%.
Though the share of fraudulent messages in the total amount of spam has declined, fraudulent spam is getting more and more hostile: spammers are honing their skills and carrying out targeted attacks. So as not to fall victim to “well-wishers” offering fast and easy ways of enrichment, email users simply have to be careful, though it can be difficult to detect more sophisticated spammer tricks. As for phishing, this type of fraud requires software protection methods.
To be on the safe side, users should not believe the “good intentions” of spammers and install software which provides reliable protection from spam, phishing and malicious programs. Though these recommendations may seem trivial, adhering to them will save both the data on your computer and your money.




















Fraudulent spam