
Spammers have brought another instrument into their orchestra of tricks – MP3 audio files. This new type of spam is circulating in European mail traffic: a blank message, a classic social engineering message header, and an attached MP3 file. There’s been speculation that this might happen for a while, and although this new development is interesting, we don’t think that MP3 spam is going to have much of a future.
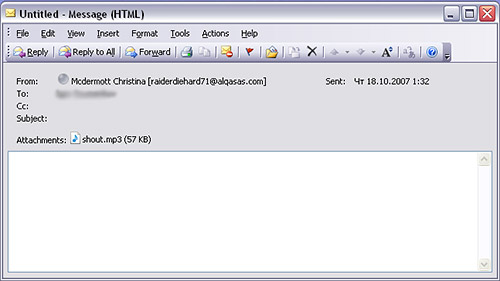
The actual audio file contains a ‘stock spam’ message designed to inflate the price of shares in a certain company. But the spammers have had to make a trade off between making the message as small as possible, and making a comprehensible recording. They’ve misjudged – the quality of the sound file isn’t easy to listen to. Even if a user does bother to listen to the almost 30 seconds of advertising, it’s unlikely that they’ll be persuaded to buy, as listening to a recording, noting the details and then going online is a far longer process than simply clicking on a link in an email.
However, this latest mass mailing demonstrates once again that spammers are still trying new tricks in their continued quest to slip advertising past spam filters and trick unwary users.





















Spammers change their tune