
Introduction
Social Networking is the one area of the Internet that nearly every computer-literate person indulges in these days. It doesn’t matter whether it’s your company boss, your neighbor, your boyfriend or your girlfriend, everybody’s contactable via at least one of the Social Networking portals. However, since these platforms attract so many people – most of whom are blissfully unaware of the need for online security – they also draw in the cybercriminals who are out to make a fast buck from the unwary users.
The threats out there can range from just the basic spam advertisement that we all find in our inboxes, to the more sophisticated scams designed to steal your Social Network account credentials, or ultimately, to infect your computer with a Backdoor. This can result in the loss of your private data and your money, not to mention endangering the people around you also. It is important to understand that by falling victim to these criminals, you are not only endangering yourself, but also the people around you, notably your friends on these Social Networks. To keep yourself safe, you need not only to follow some basic rules yourself, but also raise the awareness of your friends too!
Attacking your Friends: Account Phishing
One of the less technically dangerous security threats emanating from the world of Social Networking is the traditional attempt to Phish for a users login credentials. As previously seen from Online Banking scams or faked IRS notifications , the attacker sets up a website that is identical to the login page of the targeted Social Network site and then spams a link to it via email or messages purportedly from the Social Network itself.

Figure 1: Facebook Phishing Site
Of course this page has no functionality except to redirect the unwary user to the original Social Networking site after the user has entered their login data. The attacker can then abuse the login credentials that they have gained in numerous ways:
- Sell the credentials on the black market
- Gather more information about the attacked individual from their profile
- Send more spam via the Social Network platform from the compromised account
Having gained access to your account, an attacker can now exploit your network of trust. The attacker can impersonate you, sending your friends messages that appear to originate from you, and can also use your friends’ trust in you to convince them to follow a link, install a malicious program, or to login to a Phishing site themselves.
Luckily these attacks are relatively easy to spot as these fake login sites do not usually have a valid SSL certificate and the domain name is normally corrupted in some way. However, the non-security-conscious users tend to ignore such indicators – as they are too busy thinking about what ‘funny picture’ to send to their friends. However, Social Networking sites such as Facebook do their best to make their users aware of these easily detectable attacks. Generally, sites like Facebook tend to inform their users about known threats on their respective security pages.
Losing your Login without Being Phished
Another type of threat that has graduated from simply targeting Online Banking to now attacking Social Networking users are password stealers. These programs inject sections of their code into your browser (mainly Internet Explorer and sometimes Firefox are targeted) in order to steal your account information before it is sent over the network.
Since the data is stolen completely inside the browser, the SSL encryption between your computer and the website cannot protect you. However, a valid SSL certificate is presented by the Social Networking site and your browser shows the correct indicators for that. Hence, these attacks are much harder to spot than simple Phishing attacks. Because a password stealer is malware that is installed locally on your computer, a current antivirus solution is the best defense against these attempts to steal your account credentials.
Once an attacker has successfully Phished your credentials, it is very likely that they will go on to send links that will install the password stealer onto your friends’ machines as well, resulting in exponential propagation characteristics:
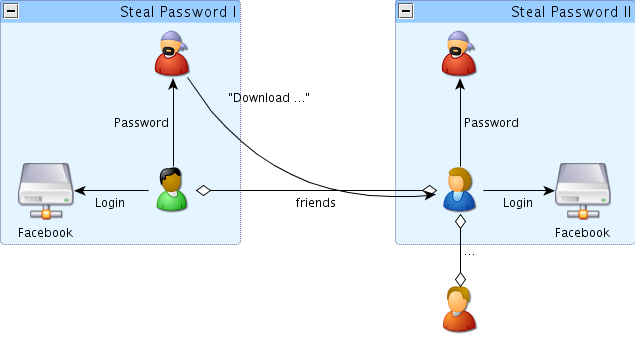
Figure 2: Social Network Password Stealer [PWS] Propagation
Most of the messages sent using the impersonation technique contain a social engineering component that tries to lure the victim (the recipient of the message) into visiting a certain website or downloading a program to their machine. Even if you cannot convince your friends to install a good antivirus solution, you can tell them that they cannot trust links sent by their friends. As these attacks are machine-generated, asking your friends if they really did send you a link is a wise precaution.
One prominent and widespread family of malware that exploits this approach is the Koobface family (an anagram of Facebook), which targets not one, but several Social Networking sites:
- MySpace
- Hi5 Networks
- Bebo
- … and many more according to variant
Getting Hit in a Drive-By
Sometimes visiting a malicious website is enough to see malware unknowingly installed on a user’s computer, as sometimes vulnerabilities in your Browser allow for the arbitrary execution of code — even when Java(Script) and Flash are turned off! Once these pages are visited by someone with a vulnerable Browser, infection is inevitable if no current antivirus solution is present. However, the attacker first needs to attract visitors to such a page. One way is the aforementioned abuse of your network of trust by sending messages purportedly from you, pointing to the attacker’s page.
Figure 3: Internet Explorer Code Execution
Another route recently adopted by attackers is spamming Twitter and posting comments on Blogger sites containing links to malicious targets. On Twitter especially, the attackers choose the most popular topics of the day and add links to their malicious sites along with their comments (on Twitter there is a concept similar to channels where certain topics are tagged with a hash-sign).
On services like Twitter, where message space is very limited, URL shortening services are very common. Most of these services do not provide a preview function of the URL they’re eventually pointing to and therefore an attacker can easily hide behind a semi-trusted name like the URL shortening service’s one. This further increases the breadth of the attack.
Who to entrust your data to?
Sites such as Facebook often allow third-party developers to add their own ‘Applications’ to the Social Networking Site and eventually to a users profile also. These applications often have full access to your personal data and profile information. The user is asked to consent to sharing their personal data and often can even choose which specific elements of their data they wish to share. But an application that makes use of clever social engineering techniques, just like a Trojan, can get a user to divulge virtually all of their personal data.
Thankfully, companies like Facebook are now aware of these issues and therefore manually check any applications before they allow them to be rolled out across their network. However of course, like all companies their resources are limited, and with almost 50.000 custom applications available on Facebook these days, not everything can receive the scrutiny it deserves. Thus you could very well end up enabling a ‘Daily Picture’ application that displays a different cute kitty every day — whilst behind the scenes it is accessing all of your personal data. The sad truth is that these days anyone authoring such an application could embed a backdoor that loads JavaScript from a third-party server and eventually leaks all your personal data. If the attacker is skilled enough, the application may very well just slip past the Facebook analyst’s watchful eyes unnoticed!
These attacks are very difficult to detect for the average user as the third-party application can integrate itself almost entirely into the trusted Social Networking site in terms of appearance and functionality. Often, an antivirus solution cannot help here either as the third-party application is running server-side on the Facebook network. It really is down to whichever Social Networking site to eliminate these threats.




















The Dangers of Social Networking