
It’s one of these days where I just had one of these “Oh no…” moments when I logged into my Twitter account and suddenly a message box with my cookie popped up.
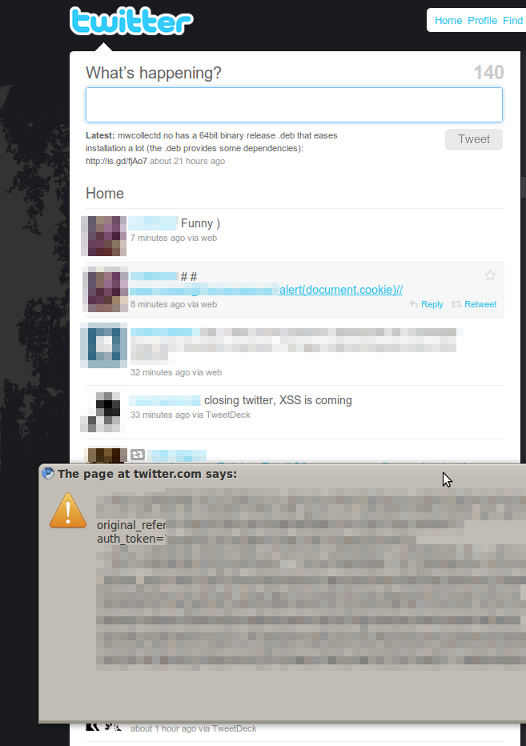
Apparently, there is an actively exploited XSS vulnerability on Twitter. From my first preliminary analysis, you’ll have to hover over a link to activate it and so far I have just seen some proof of concepts from people I follow. However, this vulnerability looks at least semi-wormable, so better turn JavaScript off on Twitter for now!
Update (14:05 CEST): This vulnerability is confirmed to be exploitable with no user interaction automatically. Turn off JavaScript for Twitter!
Update 2 (14:13 CEST): It is possible to load secondary JavaScript from an external URL with no user interaction, which makes this definitely wormable and dangerous.
Update 3 (14:24 CEST): Worm code for this vulnerability has been posted on IRC, making the rounds.
Update 4 (14:36 CEST): Worm is live already…
Update 5 (14:59 CEST): It appears Twitter now properly escapes links, that specific vulnerability seems closed.
Update on Infection Rates (posted by Costin): During the peak of the infection, we noticed roughly 100 posts per second which seemed to be related to the exploit. Thanks to Paul Roberts who pointed out a simple way of looking at the outbreak using Twitscoop:
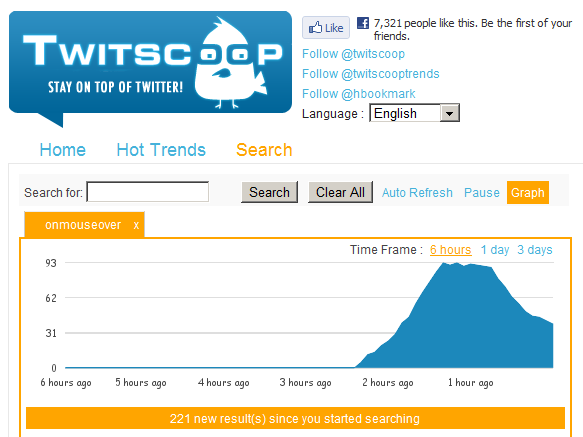
The graph suggests 93 posts per second, which is not far from the peak we observed.
Although accurate numbers are hard to extrapolate from the existing data, the total number of malicious posts could have easily exceeded half a million.

















Live Twitter XSS