
Targeted attack attribution is always a tricky thing, and in general, we believe that attribution is best left to law enforcement agencies. The reason is that, while in 90% of cases it is possible to understand a few things about the attackers, such as their native language or even location, the remaining 10% can lead to embarrassing attribution errors or worse. High-profile actors make every effort to stay undetected inside the victim’s infrastructure and to leave as few traces as they can. They implement a variety of techniques to make investigation of their campaigns more difficult. Using LOLBINS, common legitimate pentesting tools, and fileless malware; misleading security researchers by placing false flags—these and other anti-forensic tricks often make threat attribution a matter of luck. That is why there is always a percentage of targeted attacks that remain unattributed for years. Recently, I shared my TOP 10 list of the most mysterious APT campaigns/tools on Twitter. In this article, I provide a bit more detail on each case.
1. Project TajMahal
In late 2018, we discovered a sophisticated espionage framework, which we dubbed “TajMahal“. It consists of two different packages, self-named “Tokyo” and “Yokohama”, and is capable of stealing a variety of data, including data from CDs burnt on the victim’s machine and documents sent to the printer queue. Each package includes a number of malicious tools: backdoors, keyloggers, downloaders, orchestrators, screen and webcam grabbers, audio recorders, and more. In total, up to 80 malicious modules were discovered.
Project TajMahal had been active for at least five years before we first detected it. What makes it even more mysterious is that its only known victim is a high-profile diplomatic entity. Who was behind the attack, if there were any other victims, or whether the whole toolset was developed to penetrate just one organization—these questions remain unanswered.
2. DarkUniverse
DarkUniverse is another APT framework we discovered and reported on in 2018. It was active in the wild for at least for eight years—from 2009 to 2017—and targeted at least 20 civilian and military entities in Syria, Iran, Afghanistan, Tanzania, Ethiopia, Sudan, Russia, Belarus, and the United Arab Emirates. The malware spreads through spear-phishing emails with a malicious Microsoft Office document as attachment. It consists of several modules responsible for different espionage activities such as keylogging, mail traffic interception, making screenshots, collecting of a wide variety of system information, and more.
The only prominent case of DarkUniverse being spotted in the wild was when their sophisticated ItaDuke malware was dropped with a zero-day PDF exploit conspicuously named “Visaform Turkey.pdf”. DarkUniverse remains unattributed, and it is unclear what happened to the actor after 2017.
3. PuzzleMaker
In April 2021, we detected several targeted attacks using a complex chain of zero-day exploits. To penetrate the system, the actor used a Google Chrome RCE vulnerability. We were not able to obtain the exploit, but suspected the flaw in question was CVE-2021-21224, which enabled an attacker to execute arbitrary code inside the browser sandbox. Once inside, the actor exploited CVE-2021-31955, an information disclosure vulnerability in the Windows kernel, to obtain the kernel address of the EPROCESS structure, and elevated privileges using one more Windows kernel flaw, CVE-2021-31956.
After successful exploitation of these vulnerabilities, custom malware consisting of four modules is delivered to the infected system. The modules are a stager, dropper, service, and remote shell, with the last one being the final payload. We dubbed the APT “PuzzleMaker”.
The only weak link to known APT campaigns is a post-exploitation technique that is used both by PuzzleMaker and the CHAINSHOT malware, and by at least two state-sponsored threat actors. However, the technique is publicly known and can be used by various groups independently.
4. ProjectSauron (aka Strider)
ProjectSauron was first discovered in September 2015, when Kaspersky Anti-Targeted Attack Platform detected anomalous network traffic in a customer organization. The traffic originated from a suspicious library loaded into the memory of a domain controller server and registered as a Windows password filter, which has access to plain-text passwords to administrative accounts. It proved to be a part of a complex APT platform targeting government, telecommunication, scientific, military, and financial organizations in Russia, Iran, Rwanda, and possibly, Italian-speaking countries.
ProjectSauron got its name from the “Sauron” mentioned in its configuration
The ProjectSauron platform has a modular structure. Its core implants are unique to each victim, with different file names and sizes, and timestamps tailored to the target environment. This way, the artifacts discovered in one organization are of low value to other victims. These core implants act as backdoors that download additional modules and run commands inside the memory. The modules perform specific espionage functions, such as keylogging, stealing documents, or hijacking encryption keys from infected computers and attached USB devices. A special module is responsible for accessing air-gapped systems through infected USB drives.
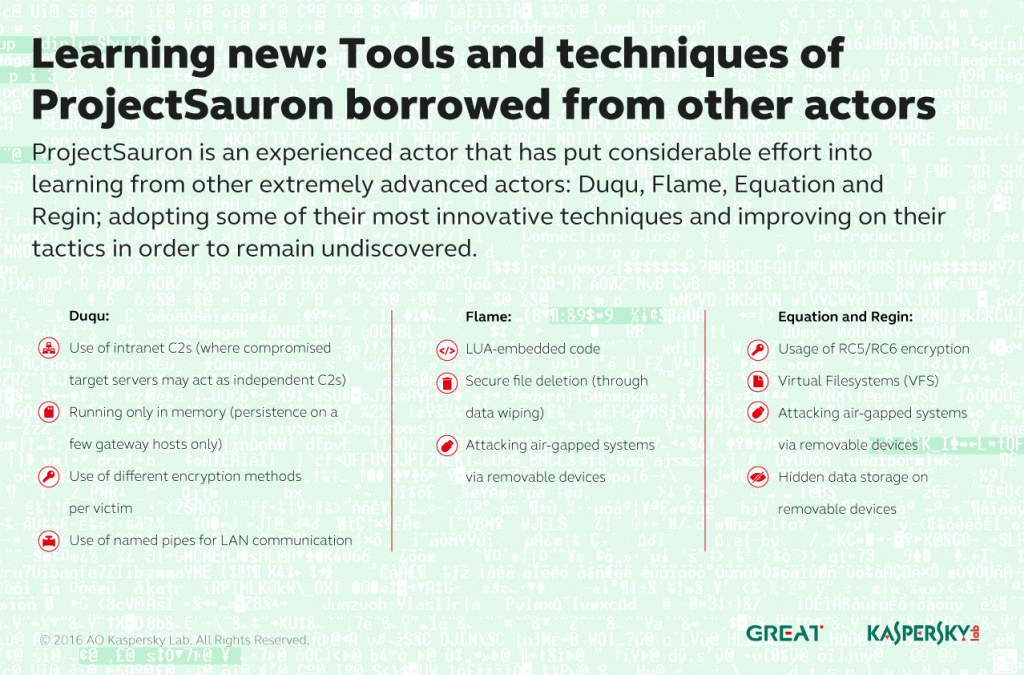
The threat actor behind ProjectSauron uses a complex command-and-control infrastructure involving a wide range of different ISPs and a number of IP-addresses across US and Europe. The actor made every possible effort not to create recognizable patterns in its operations. The only thing that can be said with confidence is that this level of sophistication is hardly achievable without a nation-state sponsor. It is also worth noting that the actor probably learned from other high-profile APTs, such as Duqu, Flame, Equation, and Regin.
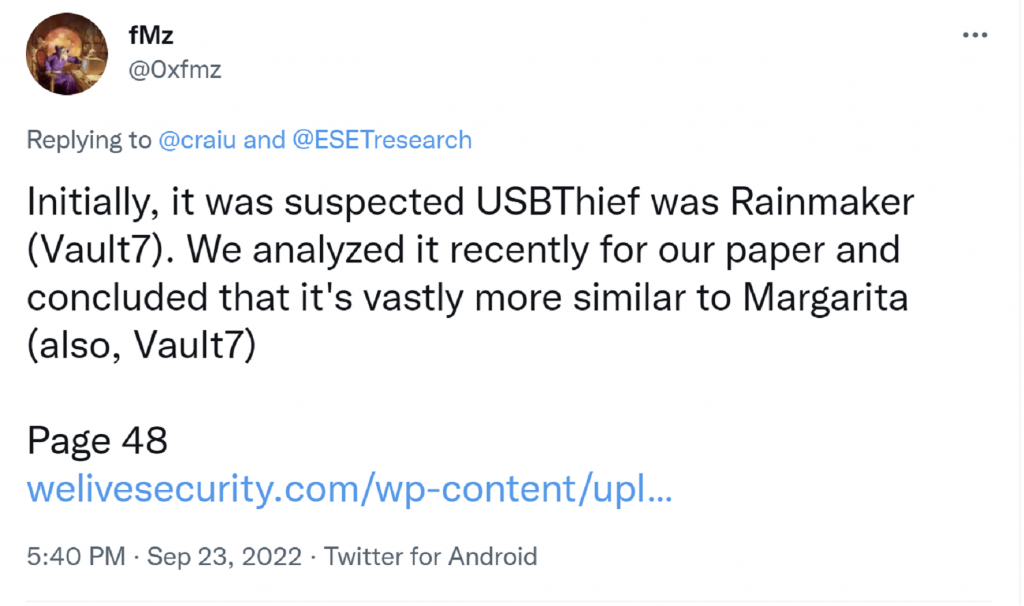
5. USB Thief
In 2016, our colleagues at ESET discovered a type of USB malware that featured a tricky self-protection mechanism. Dubbed “USB Thief”, it consisted of six files, two of which were configuration files, while the other four were executables. The files were designed to be executed in a pre-defined order, and some of them were AES128-encrypted. The encryption key was generated using a unique USB device ID and certain disk properties. This made it hard to decrypt and run the files anywhere but on the infected USB drive.
Three of the executable files are loaders that load the next-stage file. To ensure that the files are loaded in the correct order, they use hashes of the previously loaded files as their names. Additionally, some of the files check the name of the parent process and terminate if it is wrong. The final payload is a data stealer that looks to the configuration file for information about what data to exfiltrate, how to encrypt it, and where to store. The data is always exfiltrated to a location on the infected USB device.
Another interesting technique implemented in USB Thief is using portable versions of certain applications, such as Notepad, Firefox, and TrueCrypt, to trick the user into running the first malware loader. To achieve this goal, it injects itself into the command chain of these applications as a plugin or a dynamic linked library. When the user runs the infected app, the malware launches, too. The malware is not widespread and is most likely used in highly targeted attacks involving a human asset.
Since my post on Twitter, our colleagues at ESET shared further information on this toolset, which includes their suspicion that it might be associated with the Lamberts APT group:
6. TENSHO (aka White Tur)
In early 2021, while searching for phishing pages that spoofed governmental websites, researchers at the PwC company stumbled across a page used to phish for Serbian Ministry of Defense credentials. This page led them to a previously unknown threat actor dubbed “TENSHO” or “White Tur”. This actor has been active since at least 2017 and uses a variety of unique techniques and tools, which include weaponized documents, HTA and PowerShell scripts, Windows executables, and phishing pages that mimic governmental websites.
Among other tools, TENSHO uses the OpenHardwareMonitor open-source project, whose legitimate purpose is to monitor device temperature, fan speed, and other hardware health data. The threat actor spreads a malicious OpenHardwareMonitor package designed to deliver TENSHO’s malware in the form of a PowerShell script or Windows binary.
To date, no ties have been discovered between this threat actor and any known APT group. TENSHO targets organizations inside Serbia and Republika Srpska (an entity in Bosnia and Herzegovina) indicating a very specific regional interest. Because many parties might be interested in targeting these regions, it is not easy to attribute the threat.
7. PlexingEagle
During the HITBSec 2017 conference in Amsterdam, Emmanuel Gadaix presented the discovery of a highly interesting GSM cyberespionage toolset, likely deployed by a very advanced threat actor, found during a routine security sweep in a client’s systems.
A Surprise Encounter With a Telco APT, by courtesy of Emmanuel Gadaix
The compromise was originally discovered by Gadaix’ team on a Solaris 10 machine that was used by the actors as an operating base. From there, the attackers leveraged advanced knowledge of the GSM infrastructure and network to patch the functionality normally used by law enforcement for eavesdropping on phone calls in order to implement their own mechanisms for intercepting calls of interest. The malware used in the intrusion was written using LUA, a language we saw used by other advanced threat actors, such as the ones behind Flame and Project Sauron. In his presentation, Gadaix hints at a number of similarities between this case and the so-called “Athens Affair”, the two being the only known cases of this threat actor actually being caught in the wild.
8. SinSono
In May 2021, Syniverse, a telecom company that provides text message routing services to such carriers as At&T, Verizon, T-Mobile, and others, detected unauthorized access to its IT systems. An internal investigation revealed that an unknown adversary first penetrated Syniverse’s infrastructure in 2016. For five years they had acted undetected, accessed internal databases, and managed to compromise about 235 customers’ login credentials for the company’s Electronic Data Transfer (EDT) environment. Through these accounts, the threat actor could access highly sensitive consumer data, e.g., call records and the contents of text messages.
While the company reset or inactivated credentials for all EDT customers, and contacted affected organizations, many questions remain: for instance, if the actor had actually stolen sensitive data or not. Although the company itself and some of the carriers relying on its services see no indicators of a major breach and no attempt to disrupt their processes, we know neither who the actor was nor what their goals were. Our analysis of the data related to the attack indicates a high degree of attention and care regarding operational security and ensuring that attribution is difficult.
9. MagicScroll (aka AcidBox)
MagicScroll is a sophisticated malicious framework that was first detected by Palo Alto’s Unit 42 in 2019. It is a type of multistage malware with only a few known samples and one known victim, located in Russia and attacked in 2017. The initial infection stage of MagicScroll is missing. The first known stage is a loader that was created as a security support provider, a DLL that usually provides certain security features, such as application authentication. MagicScroll abuses this functionality to achieve injection into the lsass.exe process and probably persistence as well.
The loader’s main purpose is to decrypt and load the next-stage module, which is stored in the registry. This module exploits a VirtualBox driver vulnerability to load an unsigned malicious driver in kernel mode. According to Unit 42, the exploitation of this vulnerability was previously observed in Turla operations, however there is no indication that the new actor has any links to that group. Unit 42 also found some loose similarities with ProjectSauron, but they stated that these are too weak for considering the two campaigns linked. Neither have we found any ties between MagicScroll and any other known APTs.
10. Metador
The Metador threat actor was first publicly described by SentinelLabs in September 2022. It mainly targets ISPs, telecommunication companies, and universities in several countries in the Middle East and Africa; at least one of its victims has been attacked by nearly ten different APT groups.
Metador operates two malware platforms dubbed “metaMain” and “Mafalda”, which are deployed purely in memory. The metaMain platform is a feature-rich backdoor, which provides the threat actor with long-term access to the infected system. It can log keyboard and mouse events, make screenshots, download and upload files, and execute arbitrary shellcode.
Mafalda is a backdoor that is being actively developed. Its latest version was compiled with a timestamp of December 2021. It features a number of anti-analysis techniques and supports 67 commands, which is 13 more than in the previous version of the malware.
Apart from typical backdoor functionality, metaMain and Mafalda are capable of establishing connections to other (yet unknown) implants and exchange data with these. One of those implants is called “Cryshell” and acts as intermediate server between metaMain or Mafalda, and the C2. There are reasons to believe that unknown Linux implants exist that can send data collected from Linux machines to Mafalda.
It is yet to be established who the actor behind Metador is and what their goals are. The sophisticated malware designed to stay undetected for a long time suggests that this is a cyberespionage campaign by a high-end threat actor. At least some of the C2 responses are in Spanish, which may indicate that the actor or some of its developers speak Spanish. Also, some cultural references were found in Metador’s malware, including British pop punk lyrics and Argentinian political cartoons. The diversity of traces makes it difficult to determine in which state’s interests it operates—if at all. One of the hypotheses is that the group is a high-end contractor.
Conclusion
Advanced threat actors use every possible means to stay undetected, and—if caught—unattributed. Every now and then, security researchers will reveal a mysterious campaign that has remained uncovered for years and that is nearly impossible to trace back to its benefactors with certitude. The ten stories described in this post are just some of the many unattributed mysteries we have seen through the years. That is why it is important to discuss them and share data on them within the cybersecurity community.






















TOP 10 unattributed APT mysteries