
Interesting news on Trojan SMS Blockers (Winlock etc). These programs block Windows and demand a ransom in the form of a text message which is sent to short number for a fee. It’s a very popular type of racket at the moment, both in Russia and a few other countries.
The whole affair has now reached the General Prosecutor’s office of Russia – the criminals have been identified and detained (or so it seems) and will be prosecuted in Moscow soon.
Altogether the criminals have earned an estimated 790,000 roubles, or $25K. Moreover, they have caused other damages by blocking or crashing a yet to be determined number of personal and company PCs. Very often people have needed to re-install the OS and all software and then restore data from backups – even after paying the ransom.
But I wanted to focus on the outcome – or the possible outcome of this incident, not on the investigation, arrests and so forth.
This isn’t the first computer related court case in Russia by a long way. Yes, money is being stolen, yes, sometimes the perpetrators are caught, and yes…sometimes they are even tried. And tried not only for breaking Statute 273 (creation, use and spreading malicious software for computers), but also for other, more serious, Statutes, such as Statute 159: Fraud. The latter could earn the perpetrator up to 10 years behind bars – if it’s a group and if the amounts are ‘exceptionally large’ (by Russian standards).
So if we’re talking about hundreds of thousands of roubles (which equates to tens of thousands of dollars) and crimes committed in the real world, not the ‘virtual world’ – the criminals will definitely get time behind bars. But in the case of computer-related crimes, we see the exact opposite – usually the criminals get off practically scot free.
I have no idea what the judges are thinking – but in most cases in Russia, and throughout the world, for that matter, cybercriminals receive very mild sentences and no jail time (they just get probation or a criminal record – see the ATM case). This is in spite of the fact that large sums of money can be involved, which are often far great than those in ‘real life’ fraud cases.
Are the judges sorry for these script kiddies? Or do they think money transferred over the Internet is not real money, or that cybercrime isn’t a “real” criime?
I don’t know…but I suspect that in this current case, we’ll just see the same old, same old – the criminals will get a slap on the wrist, the detectives and the prosecutors will curse and go drink vodka and my researchers will come to me once again and say ‘It seems as if we’re in the wrong business’. Because every single time my team takes part in a cybercrime investigation which ends in no real penalties – they’re demotivated. And wouldn’t you be?
I’m thinking of starting a pool about the results of the Winlock court case:
- Nothing – no criminal record, no jail time
- 2 years probation
- 3 years of probation
- 1 year in jail
- 2 or more years in jail
Dibs on 3.
PS The story continues…A major Russian content provider is now being investigated in relation to this crime.
PPS More updates – and the story is growing. 10 people have been arrested in Moscow. The gang has been in operation for about a year, and the police are saying that they potentially earned over 500 million rubles (about $16 million.)

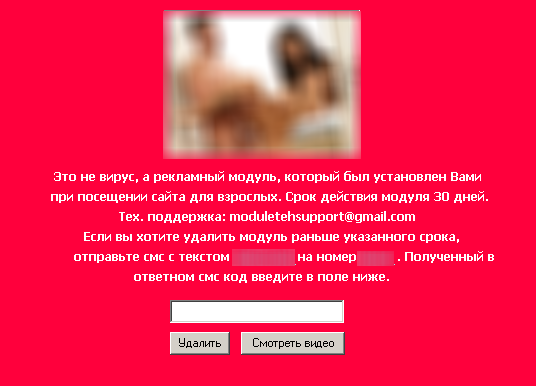
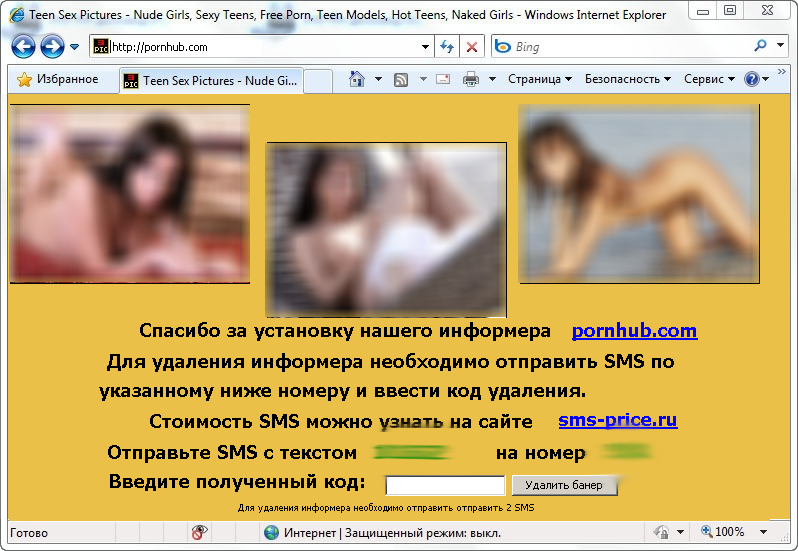




















The Winlock case – I’m taking bets!