
It’s december. While it’s getting colder and people prepare and shop for christmas, here in Bergen, a city in Norway, experts from several countries come together talking about Passwords – something you’re using while buying christmas presents online for example – at the PasswordsCon. This one held at the University of Bergen in the Auditorium Pi.

On the first day Katja Malvoni from Openwall talked about their research on “Energy-efficient bcrypt cracking” focusing on implementing cracking of bcrypt with FPGAs and RISC-platforms. Manoé Zwahlen and Nicoals Oberli focussed on securing passwords by creating a cheap DIY hardware password storage called “Pa$$ware”. Based on Teensy (a USB-Development board), together with an LCD and a SD-card reader for password storage.

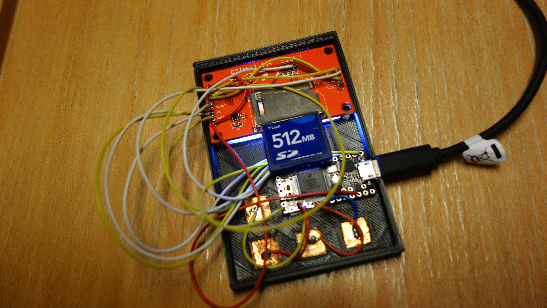
The idea behind is to store password on the device which are encrypted, plug this device into a PC and release a password when needed. The SourceCode and Plans will be opensource, for everyone to use. It’s still in development and the roadmap lists a lot of interesting features. Andrey Belenko dug into iCloud and iOS Protection in his talk “The iCloud Keychain and iOS7 Data Protection”.
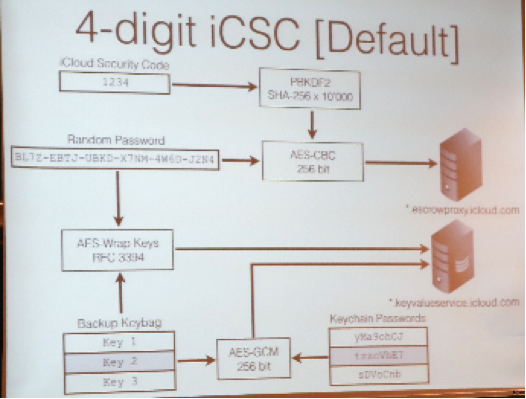
Andrey very well described the mechanisms behind and came to several conclusions as “Trust your vendor but verify his claims” and “Never use simple iCloud Security Code”. The final talk was given by Asbjørn Reglund Thorsen from Awareness Security about bypassing Passwords by using Cookies as attack method with a call to Owners of webresources with Login to turn on SSL, setting the secure flag in Cookies and use strict transport security.
What do attendees to PasswordsCon do during the Lunch break? Playing “Adobe Crossword” – which nicely educates on not using bad passwords.






















PasswordsCon in Bergen