
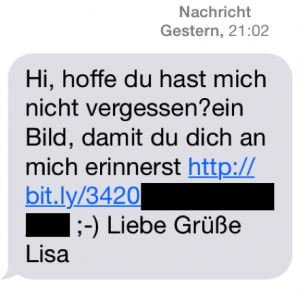
Last night I got a unexpected SMS in German language on one of my phones. A message from “Lisa”, pretending to know me, including an url luring the reader to a picture of her.
The short-url points to the domain “m.bensbumsblog.com”, which is already known for being used in SMS-spam for dating-websites, redirecting to a dating website. As there was no preregistration or request for this SMS, this clearly belongs into the category unsolicited bulk message.
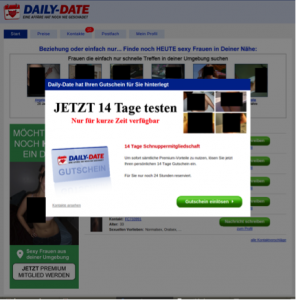
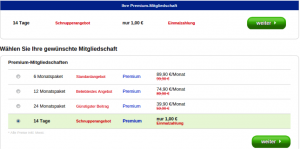
The final target of the link is “daily-date.de”. This website requires registration (username, password, mail-address and several personal questions). Finally it offers premium access to the system, which means searching, meeting and texting people as well as watching pictures, not for free though. This campaign offers a 14-day trail for 1€.
The domain “bensbumsblog.com” is protected by an anonymizing service to avoid identifying the owner. Although the IP-address is owned by a cloud service (according to RIPE lookup) and rented by some marketing company (IP reverse lookup).
The final website “daily-date.de” belongs to a German company, located in Berlin.
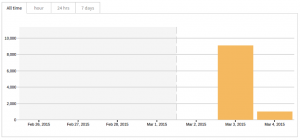
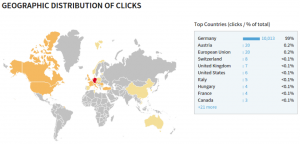
A look at the click-statistics from “bit.ly” shows that this campaign started on 03.03.2015 and got more than 10,000 clicks within 18 hours, most of them from Germany. Most clicks appeared in the first 3 hours of the campaign (started around 18:00 CET).
The “bit.ly”-user “benbu”, who setup this Link, already created 15 Bitlinks/Short-URLs (active since 2nd of march 2015).
| Amount of Bitlinks | Target/Campaign |
| 6 | DailyDates (this campaign) |
| 1 | Easy money/credit cards |
| 8 | Coupons |
Spam is a common problem, not only via email. Although SMS-Spam is more common in Asia but less common in Europe.
Having a look at other campaigns by this user, not all were successful. Besides this campaign, 6 others got some clicks. All mostly targeting Germany.
| Created | Target/Campaign | Clicks |
| 02.03.2015 | Coupons | 2630 |
| 02.03.2015 | Coupons | 1764 |
| 02.03.2015 | Coupons | 250 |
| 02.03.2015 | DailyDates | 993 |
| 03.03.2015 | Coupons | 1878 |
| 03.03.2015 | Coupons | 1004 |
In general make sure that you don’t just click on any link you get as there might also be malicious content behind. To improve protection of your mobile (smartphone/tablet) always ensure you install updates. Further you should have security software installed to be protected against mobile malware.
























Dating Lisa for 1 Euro