
The credit crunch means we’re all increasingly aware of bank charges, interest rates, and how we can save a few extra pennies. Financial advisors have written pages on how transferring an existing credit card balance to another card issuer could save you money, and most people are shopping around for the best offers.
Of course, the APR and other rates don’t worry cybercriminals. All they want to do is get their hands on credit card numbers and then use them or sell them on. Who cares if the card owner gets stung with additional charges?
What is interesting, though, is the fluctuating price of card data. I was analysing a bit of malware which led me through a number of redirects to a site offering stolen credit card numbers.
A sliding scale of prices according to country, and varying availability. And not only are they offering cards from lots of different sources, but the guys behind this are providing a full service, with technical support available from 0900 – 2200 in English and German, and their own type of guarantee:
That the German credit card data costs more, but is guaranteed for a much shorter period seems to contradict free market principles. It seems as though there’s demand for numbers from particular countries. This is probably because it’s easier to use stolen card numbers from certain countries – this might be because bureaucracy means it takes longer to get the card blocked, because the card issuer returns funds to the victim without too many questions, because there are fewer checks when the card is used on the Internet, or because there’s less likely to be a criminal investigation due to local restrictions on law enforcement – the list is pretty long. But even with such a short product life span, these guys aren’t doing this for fun – the site is clearly set up as a business, and links to other sites offering cybercriminal services and information.

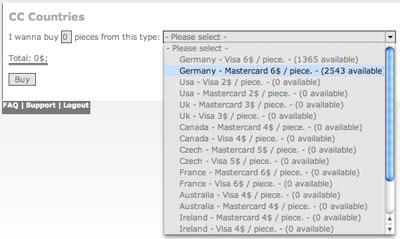
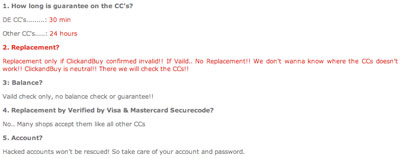




















How much does a credit card cost?