
While passwords are still an essential topic in IT-Security, the recovery and cracking of those is as well. There are several tools focusing on password recovery while two of them stand out of the crowd: Hashcat/oclHashcat and John-the-Ripper (JtR).
- We already mentioned Hashcat in our blog on account password security here.
- Jens Steube – the mind behind Hashcat -also supported our research on the Gauss malware by creating the GaussCrack.
- Beginning of this year we also asked for help on the Equation Group MD5 “e6d290a03b70cfa5d4451da444bdea39”. Jens Steube and Philipp Schmidt solved it as arabic word for “unregistered”.

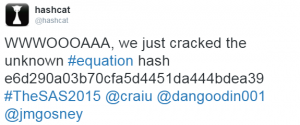
Last Friday, a “cryptic” message was posted on Twitter by @hashcat
The MD5 revealed a major step for Hashcat: “hashcat open source” – Jens ‘atom’ Steube decided to go OpenSource with his well-known Password recovering/cracking tool Hashcat/oclHashcat. Over this weekend, the github repository of Hashcat was among the top trending and collected already more than 1,000 “stars“.
Repository Official Announcement
Hashcat and oclHashcat
This project implements a rich set of features of attacks against a long list of algorithms. Hashcat is for CPU-based hash cracking while oclHashcat uses GPUs.
Why Password cracking tools and OpenSource?
There are many reasons why such tools are needed. One of the main user-groups are penetration-testers. Their job is to evaluate the security in given areas including evaluation of password security. Also forensic-examiners use these tools in order to gain access to required evidence. These cases and tasks are often highly sensitive and apply to strict rules. OpenSource offers the possibility of developing customized extensions without leaking any potential sensitive information to external developers of such tools. This applies if different hash-algorithms are required to be audited while pentesting or specific requirements are set in forensic cases e.g. criminal evidence collection for an upcoming lawsuit.
The implemented functionalities also try to push for stronger security by revealing unsecure hash-algorithms or vulnerabilities and weak passwords. This is must not be underestimated, as driving the evolution and development of new secure algorithms is an important and necessary step. [see Collision Vulnerabilities in MD5, SHA1 and SHA2.
Hashcat as OpenSource under the MIT License will now open possibilities of integrating other libraries and porting the software to other platforms. Hashcat may now also be integrated into Linux distributions and thereby opening up for a broader audience, since it’s even easier to use.
It’s difficult to foresee the future, but for sure we’ll see more development in this area – for a good reason.
























Stepping out of the dark: Hashcat went OpenSource