
There’s a lot of talk these days about how important it is to act locally: use local services, and you’ll need your car less, buy local produce, and you’ll support small businesses. All of which is good for the environment.
Even though the AV world might not seem to be connected to the physical world, it’s just important for us in the industry to act locally. For instance, in a case last week, we noticed that Brazilian virus writers are moving on up. Until recently, they’ve been sending the same piece of spam containing links to the same malicious file regardless of which country the victim was in. But now they’ve started to differentiate, and they’re now targeting their mailings (and consequently their malware) on a country-by-country basis.
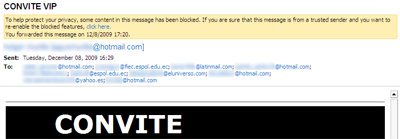
This screenshot comes from one such mailing:
Look at the addresses, and you can guess that this mailing is targeting victims based in Ecuador. As for ‘international’ addresses like hotmail.com, the bad guys can easily work out which country the owner of the address. They just send a simple “POST” request to a remote web server running a PHP script which uses GeoIP functions, e.g. server.com POST/ln.php.
The way in which the bad guys steal these email addresses is pretty simple: by launching code on victim machines which reads addresses from the email client database. For example, if the victim is using Outlook Express, then the .wab file gets read.
This latest move demonstrates that Brazilian virus writers and cybercriminals are looking to break new boundaries by sending out malware tailored to specific countries. In doing this, they reduce the chances of their malware falling into the hands of antivirus vendors who don’t have a local presence. In the case of the message above, 2 days after we intercepted it only 9 out of 41 vendors (or 21.96%) were flagged by Virustotal as detecting it.
Just goes to show that thinking globally and acting locally isn’t just about keeping our physical environment clean and secure, but our digital one as well.

















AV thinks globally, acts locally