
At the moment, there are more than 100 million Mac OS X users around the world. The number has grown switfly during the past years we expect this growth to continue. Until recently, Mac OS X malware was a somehow limited category and included trojans such as the Mac OS X version of DNSChanger and more recently, fake anti-virus/scareware attacks for Mac OS X which boomed in 2011. In September 2011, the first versions of the Mac OS X trojan Flashback have appeared, however, they didn’t really become widespread until March 2012. According to data collected by Kaspersky Lab, almost 700,000 infected users have been counted at the beginning of April and the number could be higher. Although Mac OS X can be a very secure operating systems, there are certain steps which you can take to avoid becoming a victim to this growing number of attacks.
Here’s our recommendation on 10 simple tips to boost the security of your Mac:
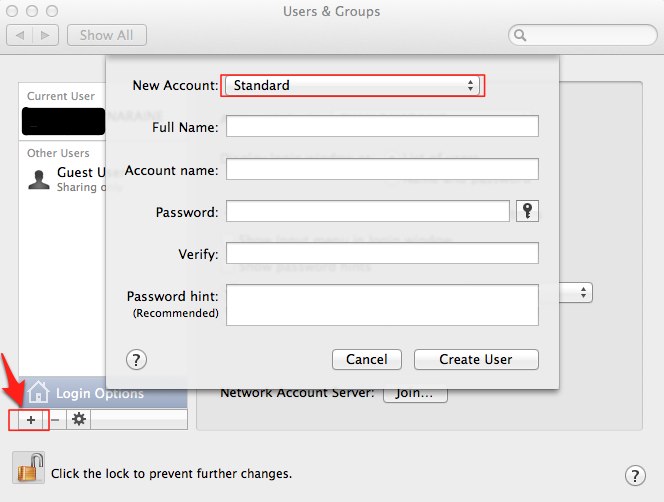
1. Create a non-admin account for everyday activities
Your default account on Mac OS X is an administrator user, and malware writers can take advantage of that to infect your computer.
For everyday activities, we recommend you create a non-admin user and you only log in as administrator when you need to perform administrative tasks. To do that, go to the “Accounts” pane of “System Preferences, then create a non-administrator user. Use the new account for everyday tasks like e-mail and web browsing. This greatly helps to limit the damage from zero-day threats and drive-by malware attacks.
2. Use a web browser that contains a sandbox and has a solid track record of fixing security issues in a prompt manner.
We recommend Google Chrome, for many reasons, one of them being that it’s updated a lot of more often than Apple’s built-in Safari browser. In addition to its own sandbox, Chrome ships with a sandboxed version of Flash Player that puts up a significant roadblock for malicious exploits. Google Chrome also has a silent, automatic update mechanism that removes the burden of patching security vulnerabilities. Make sure the new browser is also set as your default web browser.
3. Uninstall the standalone Flash Player.
Unfortunately, Adobe’s Flash Player has been common target for hackers looking to take control complete over your computer. An old version of Flash Player will most certainly put you at risk when browsing the internet. To uninstall Flash, you can use the two utilities provided by Adobe, for versions 10.4-10.5 and 10.6 and later. See this link for details.
4. Solve the Java problem.
Like Flash Player, Java is a preferred target for exploit writers looking to plant malware on your machine.
We recommend you completely uninstall it from your machine. Unfortunately, Apple doesn’t allow Oracle to update Java for Mac directly. They do it themselves, usually several months later! This means the window of exposure for Mac users is much longer than PC users.
The Java Preferences utility is in /Applications/Utilities; uncheck the boxes next to the versions listed in the General tab.
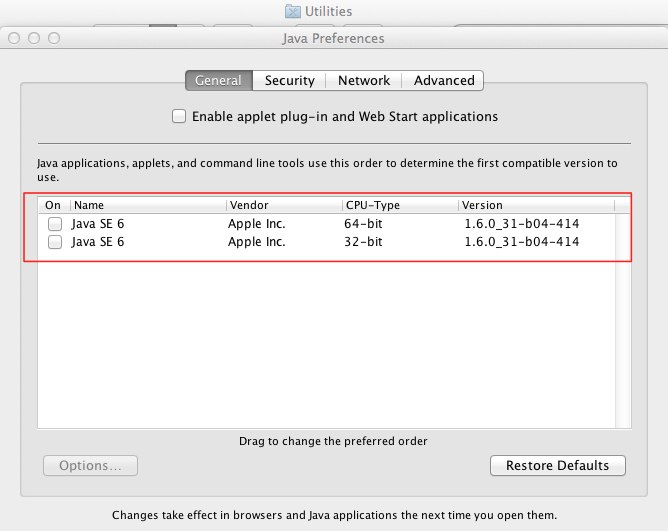
If you must use Java for some specific applications, it’s very important that you at least disable Java in Safari and other Web browsers. In Safari, go to Preferences -> Security -> Web Content and uncheck “Enable Java”.
5. Run “Software Update” and patch the machine promptly when updates are available.
Many of the recent attacks against Mac OS X take advantage of old or outdated software. Commonly exploited sxploited suites include Microsoft Office, Adobe Reader/Acrobat, and Oracle’s Java, but there are other applications that can be abused as well. Office for Mac 2011 is much better from a security point of view than Office for Mac 2008. If you are still using 2008, we recommend you update to 2011 as soon as possible. Whenever you see the Apple’s “Software Update” prompt, be sure to apply the fixes and reboot the machine when necessary.
6. Use a password manager to help cope with phishing attacks.
The good news is that unlike Windows, Mac comes with a built-in password manager, the “Keychain”.

Whenever possible, try to generate unique, strong passphrases for your resources and keep them in the keychain instead of remembering easier passwords. Whenever the cyber-criminals manage to compromise one of your accounts, they will immediately try the same password everywhere – GMail, Facebook, eBay, PayPal and so on. Hence, having an unique strong password on each resources is a huge boost to your online security.
Another, though more complicated advice is to have a separate keychain, with a 3-5 minutes password cache timeout, for important passwords only. What are important passwords? Well, things such as resources which when compromised can cause direct financial loss: eBay, PayPal, online banking and so on. If somehow your “Keychain” gets compromised, you don’t loose all the passwords.
7. Disable IPv6, AirPort and Bluetooth when not needed.
Turn off connectivity services when not in use, or when not required. These include IPv6, AirPort and Bluetooth, three services that can be used as entry points for hacker attacks.
IPv6 is a relatively new communication protocol which your Mac can use. This is rarely used in practice , although in my years of travelling, I’ve seen only one hotel which supported IPv6 in parallel to IPv4. Hence, it’s probably safe and even a good advice to disable IPv6 proactively.
To disable IPv6 on your computer
Choose Apple menu > System Preferences, and then click Network.
If the Network Preference is locked, click on the lock icon and enter your Admin password to make further changes.
Choose the network service you want to use with IPv6, such as Ethernet or AirPort.
Click Advanced, and then click TCP/IP.
Click on the Configure IPv6 pop-up menu (typically set to Automatically) and select Off.
(More details here.)
8. Enable full disk encryption (MacOS X 10.7+) or FileVault.
In MacOS X Lion, Apple updated their encryption solution (FileVault) and added full disk encryption. It is now known as “FileVault 2”. This has the advantage of security the entire disk instead of just your home folder and can be very useful if your laptop gets stolen.
(More details here.)
9. Upgrade Adobe Reader to version “10” or later.
Adobe Reader has been one of the preferred targets of cybercriminals on the Windows platform and it still ranks high among the most exploited software in the world. Version 10 includes numerous security enhancements which make it a lot safer than any previous versions. Please make sure you get the latest version from the download page at Adobe – unfortunately, many of the older versions are still available for download and it can easily become confusing.
10. Install a good security solution.
“Mac’s do not get viruses” has been a common theme ever since the famous 2006 commercial with the sick PC and the healthy Mac. Six years have passed and the situation has changed dramatically. In 2011, cybercriminals began pushing DNSChangers and fake anti-virus lures to Mac users in a very aggressive way. The Flashback trojan which appeared in September 2011 caused a huge outbreak in March 2012, which amounted for over half a million infected users worldwide. (see this article on the methodology used to calculate the number)
Nowadays, a security solution is absolutely mandatory for any Mac user. You can download and install a trial of Kaspersky Anti-Virus for Mac.
For Mac OS X power users, a utility like Little Snitch can be used to determine when a program attempts to establish an outgoing Internet connection and give you the option to allow or deny this connection.
In conclusion…
At the beginning of 2012, we predicted that an increase in the number of attacks on Mac OS X which take advantage of zero-day or unpatched vulnerabilities.
This is a normal development which happens on any other platform with enough market share to guarantee a return-on-investment for virus writers so Mac OS X fans shouldn’t be disappointed because of this. During the next few months, we are probably going to see more attacks of this kind which focus on exploiting two main things: outdated software and the user’s lack of awareness. If you follow the above steps, keep everything updated and be aware of these attacks, your chances of becoming yet another random victim will be greatly diminished.
Thanks to Ryan Naraine (@ryanaraine) for contributing to these tips.
10 Simple Tips for Boosting The Security Of Your Mac





















Paul corcoran
hi Ryan i have a security question for you. Recently i have noticed sum strange activity on my macbook terminal . I have taken all security precautions but i am unsure of how to get rid of the rat , i dont want to erase my mac to factory settings just yet, i have a print out of the terminal but not sure how deep his is into my system. All help would be greatly accepted. Thank you.