
It’s quite common to see attackers use hot topics on social networks to force users to click on malicious links. So what would be more interesting these days than using the term “Wikileaks”?
The following message arrived this weekend on one of my spam mail accounts. The subject “Wikileaks on Twitter!” caught my attention as I didn’t expect to see a spam mail with that keyword.
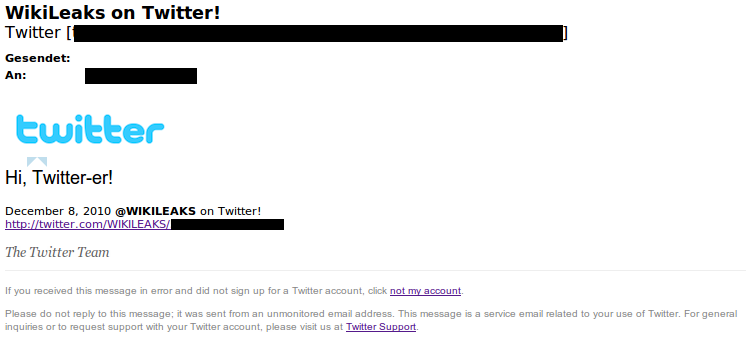
The design was cleverly done to trick users into thinking the mail was sent from Twitter. The Twitter logo is integrated and the text promises to be a service e-mail. All three links lead to the same “Canadian Health & Care” Website which is already known for Phishing/Web Forgery.

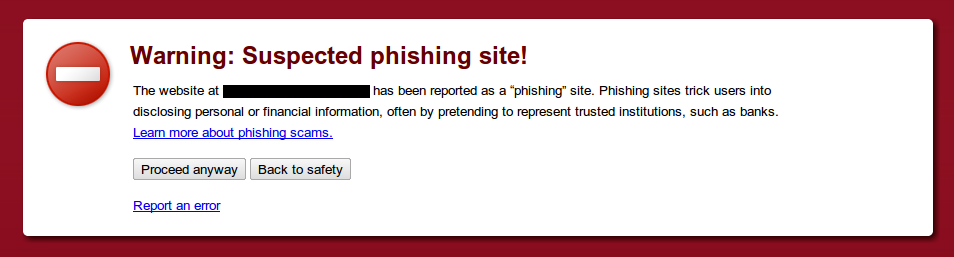
The takeaway: Be very careful when clicking on any link in e-mails. A simple checks shows that none of the links here belongs or leads to Twitter at all.

















Twitter, Leaks and Spam