
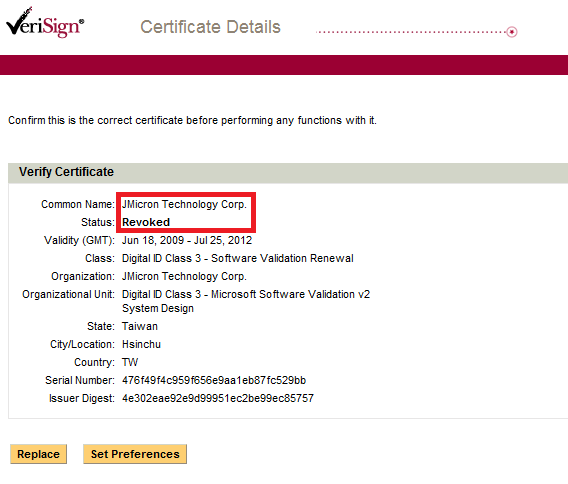
Last night, Verisign acted promptly and revoked the second stolen certificate used to sign a version of the Stuxnet rootkit driver. As previously mentioned, this certificate belonged to JMicron Technology Corp, a popular Taiwanese hardware company.
We have prepared a short FAQ about Stuxnet and the revoked stolen certificates:
-
I heard Microsoft and Verisign revoked the stolen Realtek certificate, does it mean I’m safe now?
Due to the way certificates work, a revoked certificate doesn’t mean the malware will not run anymore. You will still get infected by Stuxnet and the driver will still load without any warning. The only effect of the revoke process is that the bad guys will not be able to sign any further malware with it.
-
How many stolen certificates are we talking about?
So far, we’ve seen Stuxnet drivers signed with certificates from JMicron Technology Corp and Realtek Semiconductor Corp. Both companies seem to have offices in the Hsinchu Science and Industrial Park, which could indicate an insider job. It is also possible that the certificates were stolen using a dedicate Trojan, such as Zeus, meaning, there could be more.
-
I have a Realtek/JMicron motherboard/network card in my computer. Does it mean that I am at risk?
So far, we haven’t found anything suspicious in the Realtek/JMicron hardware drivers.
-
Now that Microsoft and Verisign revoked the Realtek/JMicron certificates, does it mean that my Realtek/JMicron drivers will stop working?
No. Due to the way certificates and signatures work, the revoking doesn’t have any effect on already signed drivers. Both companies were issued new certificates, which they can use to sign upcoming drivers.
-
Are we going to see more signed malware in the future?
Most likely, yes. There are currently tens of thousands malicious programs that have been signed – that’s a fact. For more information, I encourage everyone to view Jarno Niemel’s excellent presentation “It’s Signed, therefore it’s Clean, right?“, presented earlier this year at the CARO Workshop.


















Stuxnet signed certificates frequently asked questions