
According to surveys conducted in Europe and the United States, company employees spend up to 30% of their working hours on private affairs. By multiplying the hours spent on non-business-related things by the average cost of the working hour, the analysts estimate the costs to companies amounting to millions of dollars a year. Indirect losses may be even higher. If these employees – inadvertently or otherwise – assist hack attacks or identity theft, cause reputational damage or infringe copyright, the costs could be even greater.
The fact is that employees often use office computers to communicate on social networking sites, share links to online entertainment, or download files from suspicious resources. At the same time cybercriminals are actively using social networking sites for phishing and the distribution of malware. Many personal blogs, entertainment sites, file sharing services, torrent trackers, and files downloaded from them are infected. Passwords to email accounts are regularly hacked or stolen.
This article describes some problems which may arise from the improper use of office computers and demonstrate how to prevent similar incidents in the corporate network.
Targeted attacks
The threats that users face every day usually target mass audiences so the antivirus solution on their computers is enough to prevent most accidents. Targeted attacks are different: they are performed secretly, often using a non-standard approach; they are highly sophisticated and well organized. To achieve their goals the fraudsters use the most effective weapon to exploit any available software or social vulnerability.
Social engineering
In 2009, over 20 major software companies such as Google, Adobe, Juniper and Yahoo fell victim to the Operation Aurora targeted attack. In one version of this attack, company employees were lured to the malicious sites via social networking sites and IM clients. Using social engineering techniques the scammers got acquainted with their potential victims, gained their confidence and did whatever was necessary to make the recipients open a link. Experience shows that to achieve this it was enough to:
- collect widely-available information from social networks about the user, his interests, preferences and contacts
- create an account, focusing on the interests of the victim and his personal data (the year and the place of birth, school, college)
- become “friends” with the people from the victim’s list of contacts
- get in touch with the victim using an established “cover”
When an account has been so thoroughly prepared it has every chance of getting potential victims to click on a suspect link. If this fails, the scammer can try a more sophisticated trick, hacking the account of a user whom the victim fully trusts and sending links from there. This is often not difficult to do, especially if the victim’s trusted contacts include potentially vulnerable categories of user – elderly people, children or teenagers.
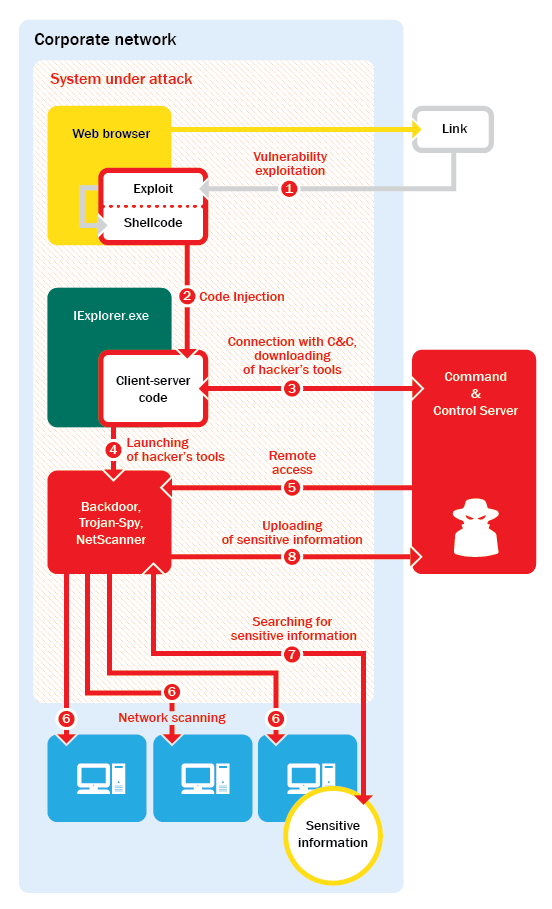
In a targeted attack, the link is likely to lead the victim to a site which contains a set of 0-day exploits that allow criminals to gain access to vulnerable computers. It is clear that by communicating on social networks from the office computer, employees may unwittingly help hackers penetrate the corporate network.
Watering Hole
In addition to targeted attacks via social networks, so-called Watering Hole attacks are no less dangerous. The basic idea of this type of attack is to find and infect the sites that are most often visited the company’s employees. Recently, the site of the U.S. Ministry of Labor was infected but it is assumed that the real target of the attack was the Department of Energy: the criminals were trying to infect the computers of DOE employees who regularly visited the Ministry of Labor’s website.
When a staff member at the company under attack opens the infected site, the code implemented in the body of the page secretly redirects the browser to a malicious site that contains a set of 0-day exploits. Malware posted on infected websites, for example a server script, often acts selectively to implement malicious code in pages sent to the user who is most relevant to the targeted company. Thus the scammers can hide the targeted attack from antivirus companies and IT security experts.
The fraudsters try to infect trusted legitimate sites. In these cases, even when users must carry out additional steps to run the exploit – to turn on JavaScript, to allow execution of the Java applet to confirm the security exception, etc. – they are likely to innocently click “Allow” and “Confirm”.
Protection
It’s clear that users play an important role in targeted attacks – they unwittingly allow scammers to attack the system. Unfortunately, there is currently no technology that can eliminate human error from corporate network security. However, reinforcing security policies with a few relevant technologies provides effective protection against targeted attacks by combating them at every stage – from the first attempt to exploit a vulnerability to attempts to compromise the network.
Protection against exploits
Since targeted attacks use unique malware, signature-based detection is not enough to identify the malicious code that is used. However, antivirus programs have long had more weapons at their disposal than mere signature-based detection. The AEP technology (automatic protection against exploits) which uses DEP and ASLR mechanisms, methods of heuristic analysis and control over executable code are able to block the execution of malicious code when it exploits a 0-day vulnerability.
If the fraudsters have managed to attack the system – via an exploit or a malicious program launched by the user – network traffic control and application control will help to prevent further penetration into the corporate network.
Network traffic control
Once malicious code (a Trojan or exploit shell code) gets in the system, it usually attempts the following (one or more):
- Establish connection with a command center (outbound connection)
- Open ports for incoming connections
- Download additional modules
- Implement malicious code in other processes to maintain the connection with the command center
- Gather information about the network, its systems and users
- Send the harvested information (IP addresses, computer names and accounts, logins, passwords, etc.) to the fraudsters’ server.
Generally, having connected to the system, the scammers try to collect information about it and about the corporate network on which the computer is located. In order to collect local information the fraudsters do not need extra privileges – the list of the running processes, installed software and patches, connected users, etc. can be found quite easily. Information about the corporate network – searches for other vulnerable systems, protection systems, shared folders, network services, servers, etc. – is collected using special scripts and utilities capable of masking their activity and bypassing security systems. All this information is sent to the cybercriminals via the Internet for analysis before they prepare the next stage of the attack.
Using network traffic control technology (Firewall, IPS / IDS) system administrators and IT security specialists can not only block dangerous network activity but also detect any penetration into the corporate network. Firewall and IPS / IDS can:
- Block incoming/outgoing connections
- by port
- by domain name and IP address
- by protocol
- Generate statistical analysis of traffic (Net flow) for anomalies
- Collect suspicious network traffic for further analysis
- Detect / Block:
- outgoing commands or similar output sent via the Internet
- downloads of suspicious files from the Internet (additional malware modules)
- transmissions of confidential information (IP addresses, logins, computer names, corporate documents, credit cards numbers, etc.)
Firewall and IPS / IDS can detect anomalies in the way network nodes interact as soon as the malicious code tries to contact the command center or actively scans the corporate network for other systems, open ports, shared folders, etc. This anomaly detection allows IT security experts to promptly respond to the threat, preventing further intrusion which might compromise the corporate network.
Application control
Having accessed the target system, the criminals aim to consolidate their success: additional modules and utilities are downloaded onto the system and malicious code providing connection with the command center is often incorporated into trusted processes like explorer.exe, csrss.exe, smss.exe, etc.
Application Control can block the launch and download of untrusted programs and modules from the scammer’s hacker set and the HIPS policies should be used to block non-standard – and potentially dangerous – behavior from legitimate software. For example, browsers should not open the ports for incoming connections, the system processes (explorer.exe, csrss.exe, smss.exe, etc.) and other applications (calc.exe, notepad.exe, etc.) should not be connected to external servers and deploy malicious code to other trusted processes – this behavior should be prohibited.
To prevent criminals from gaining control of the system, IT security specialists should:
- Prevent trusted or potentially vulnerable programs from implementing code in other processes
- Restrict applications’ access to critical system resources and files only
- Block potentially dangerous functions that are not a default feature of the applications (network access, installation of drivers, creation of screenshots, access to a webcam or microphone, etc.)
Systems which require the highest protection level should be safeguarded by the Default Deny mode which can block any program from starting up if it is not included in the white list stored locally or in the cloud.
File encryption
If the scammers seize control of the system and penetrate the corporate network, they may try to find and upload files which contain information that is potentially important for them:
- Corporate documents, including security policies
- Files containing credentials
- Configuration files
- Source codes
- Private keys
This information can be found on the main victim machine as well as in open network folders on other systems. To prevent a confidential data leak, IT security specialists should use file/disk encryption which can restrict local access to the confidential (protected) information. Data is also transferred in an encrypted form. Even if the criminals manage to download something, they will not be able to read the content of the encrypted files.
Security policies
In isolation none of the above technologies can effectively prevent a targeted attack. In order to protect the corporate network all these technologies must be well integrated and carefully tuned.
However, system administrators and IT security specialists should also use administrative protection measures:
- User education. All users must:
- Know and observe company security policies
- Understand the possible consequences of the Internet threats, such as phishing, social engineering or malware sites
- Inform the security service about all incidents.
- Control over user access rights and privileges:
- Any rights and privileges should be granted only when necessary
- All rights and privileges (access) granted to the users should be recorded
- Scan the systems for vulnerabilities and unused network services:
- Detect and analyze vulnerable network services and applications
- Update vulnerable components and applications. If there is no update, vulnerable software should be restricted or banned.
Many of these measures can be automated. For example if security policies are violated, special software shows the user a warning message. Systems Management technology can be used to search for network services and unauthorized devices, vulnerabilities and automatic updates of vulnerable applications.
Conclusion
Misuse of company resources can lead to both direct financial losses and a serious IT security incident. While communicating on social networking sites or viewing websites on the office computer, employees can become unwitting victims and involuntary allies of criminals who plan targeted attacks.
In the second part of the article we will describe an incident involving the use of personal email, software and unlicensed content on the corporate network and advise on protection measures to prevent such incidents.























Security policies: misuse of resources