In our previous blogpost, we told you about the types of attacks that a cybercriminal can undertake while working with a regular user account without local administrator privileges. In particular, we presented an example of how the simplified inheritance of privileges within the context of domain authorization (Single-Sign-On) enables cybercriminals to gain access to various network resources and services while using the limited access allowed by a regular user account. In this blogpost, we will review in detail the possible vectors for an attack launched on a corporate network from an infected computer within it.
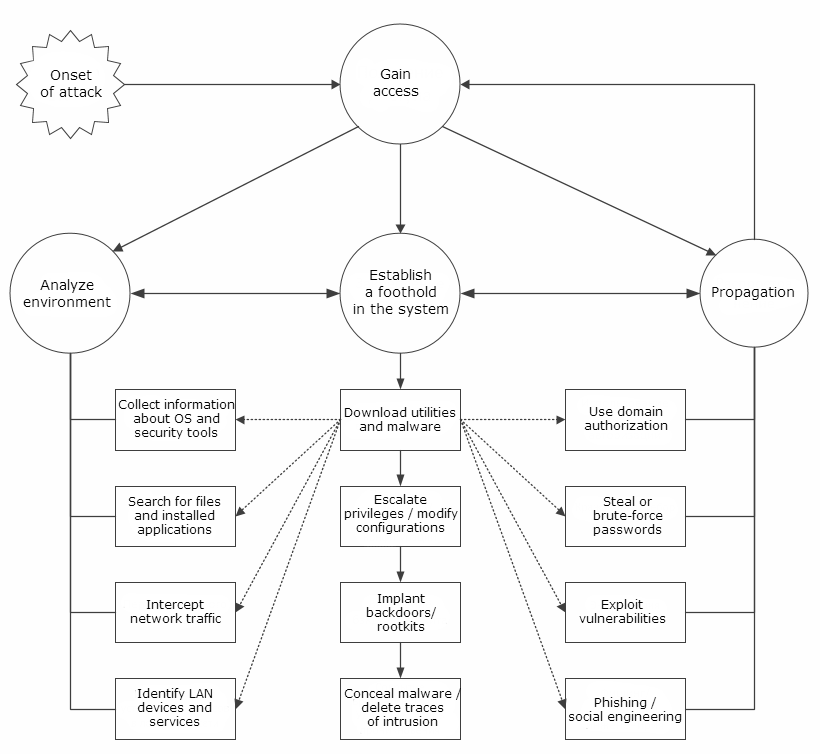
Once a cybercriminal has gained control over a user system in a corporate network, subsequent events form three consecutive stages: establishing a foothold in the system, analyzing the environment, and propagating malware. Each of these stages can be implemented in various ways, distinguished by the technical methods, strategies and tactics employed. The flow chart below shows the cybercriminal’s possible approaches to establishing a foothold in the system, analyzing the environment, and propagating malware across the corporate network.
A flow chart of a cybercriminal’s actions
It is important for information security specialists to recognize the distinctive signs of different types of attack. Using this proposed “action plan”, information security specialists can detect an attack by matching events occurring in the network to various templates of cybercriminal activity.
Gaining a Foothold in the System
After penetrating a corporate network, attackers typically download utilities (including malware) to the victim computer within a few hours or minutes. These utilities are required to collect information about the system and its installed software, search for files and data, establish a connection to the C&C, steal login credentials, brute-force passwords, hack accounts, escalate privileges, infect a system, intercept network traffic, scan network devices etc.
To hide these essential tools from network administrators during the download process and avoid triggering any security system that might be in place, attackers use different maneuvers of varying degrees of complexity:
- Files are transferred via network protocols and general-purpose ports (HTTP, FTP, HTTPS, SFTP) so they get lost in the huge amounts of daily user-generated traffic.
- Files are downloaded from compromised servers, using Fast Flux networks or via Tor.
- Files are transmitted in parts, in obfuscated and/or encrypted form.
- Various types of steganography are sometimes used to transfer data, such as masking data within audio/video files, images or headers of internet protocols, especially when general-purpose ports are closed by a firewall.
When the required tools have been loaded, the cybercriminal attempts to gain access to the local administrator’s or system account. The first attempt normally uses keyloggers, attempts to brute-force passwords and hack accounts, or phishing scams. Further approaches involve exploiting vulnerabilities in system services, typically to gain access to the system account (i.e. to escalate to kernel-level privileges).
Having obtained these privileges, cybercriminals can entrench themselves in the system by implanting a rootkit or bootkit in the operating system. They can also clean the system from traces of penetration, hiding their tools and traces of active infections from security tools. If the attackers failed to gain a foothold in the system in the regular way, they can set up an automatic infection of the system, e.g. by using the regular task scheduler.
Naturally, there are many ways of establishing a foothold, and scenarios may differ dramatically from the above description. However, as we said at the beginning of this article, it is important that an information security specialist understands the principles of how an attack is conducted, and realizes the tasks that cybercriminals face. Thus, at the foothold stage, the attacker’s main task to arrange for reliable, lasting access to the system under attack. In general, the task of arranging remote access has two parts: establishing a data communication channel and implanting a remote control tool (backdoor).
Depending on the network configuration, firewall policies and IDS/IPS settings, attackers might use direct or reverse connection. Direct connection involves the attackers establishing a connection to the victim system, and is possible only if the system has an external IP-address and open network ports that are not blocked from outside connections by a firewall. Otherwise, reverse connection is used, when the attacked system establishes a connection to the remote server. Regardless of the connection type, data is communicated using the same methods that are used to download utilities and malware to the victim computer: data is transferred in encrypted / obfuscated format via general-purpose protocols / ports, using Fast Flux or Tor. In addition, cybercriminals can also use regular user software and services as a data communication channel, such as cloud-based file storages, e-mail, IM clients etc.
Environment analysis
At the same time as establishing a foothold – or sometimes even before – cybercriminals need to collect information about the operating system and its configuration, updates installed for software, and security tools. That information is needed to evaluate the situation on the victim computer and plan further attack activities. It is also very useful when accurately selecting the most effective utilities and exploits.
The following readily available tools are usually sufficient to collect information about the system:
- cmd, regedit, vbs, powershell in Windows,
- bash, grep, python, perl in Unix/Linux and Mac OS.
From the attacker’s viewpoint, there are many advantages to using the above tools: they are available in any system, they are useable even with restricted user rights, and their operation is not controlled by most security tools. To tackle more complicated tasks cybercriminals use both popular and customized tools to intercept network traffic, scan network devices, connect to various network services using domain authentication etc. If the hacker’s tools are written, say, in Python, the cybercriminals will certainly install the required software on the infected computer. In this case, Python (or other required software) probably will not be concealed in the system using a rootkit, as that may prevent the interpreter from working properly.
To search for and analyze other devices in the corporate network, cybercriminals apply passive and active scanning methods. In particular, using a sniffer to listen to traffic from a local network interface, anyone can easily detect various devices thanks to ARP packets or active connections, determine the URLS of servers hosting corporate applications such as Active Directory, Outlook, databases, corporate websites etc. To obtain detailed information about a specific network node, cybercriminals use network scanners (e.g. nmap) to determine available network services, guess names and versions of installed software, and detect the presence of a firewall and IDS/IPS.
Distribution
Now the attackers have a foothold in the system, have a reliable remote access channel and have sufficient information about the network. The next actions usually pursue the primary objective. That may be stealing confidential information, attacks on corporate infrastructure, gaining control over critical systems for blackmail purposes, or other personal purposes. Unless the initially attacked system is the ultimate target (that can be e.g. a CEO’s laptop, a central server or a website), the attacker needs to gain control over other systems within the corporate network. Depending on the nature of the target, infection may be pinpointed or broad scale.
For example, if the attackers plan to launch an infrastructure attack, they will probably need massive infections of the servers running various business processes and the workstations of operators and administrators. On the other hand, a cybercriminal aiming to steal confidential information or conduct espionage will have to act very carefully and attack only the top priority systems.
There are a number of ways of propagating malware within a corporate network. Cybercriminals normally go for the simplest approach, such as using existing accounts. For example, by launching malicious code from under a domain account belonging to a user of an infected system, the cybercriminal can freely connect to various network services (to which the user has access) using domain authorization (Single Sign-On), i.e. without entering the login credentials. On the other hand, the cybercriminal can use a keylogger and easily get hold of the login credentials to the domain account as well as other services that do not maintain domain authorization. I addition, the cybercriminal may attempt to take advantage of vulnerabilities in the mechanisms for storing and checking credentials, or simply brute-force the password.
The most effective propagation path within corporate networks is to exploit vulnerabilities, since most corporate network security focuses on preventing attacks from outside the perimeter. Consequently, there are a multitude of varied vulnerabilities within the network, including unsecured corporate servers, test servers, management/virtualization systems etc. Practice shows that even if information security specialists and IT engineers are aware of all the vulnerabilities existing in their corporate network(s), it takes them years to fix them because it requires a lot of manpower. Nevertheless, experienced hackers are cautious about using exploits to known vulnerabilities and prefer to attack unsecured corporate services. If a local or network-based IDS/IPS is still used in the network, using exploits to known vulnerabilities may unmask the cybercriminals.
Detecting an Attack
At each stage of the attack, cybercriminals often use the environment and the available tools for their own purposes, remaining inconspicuous against the backdrop of regular users’ activities. To address this problem, it is important wherever possible to reduce redundancy in the environment and the business processes; in all other cases, it is vital to monitor what’s happening, identify anomalies and react to them.
A vivid example of the problem of redundancy in business processes is the free access to business assets (confidential documents, critical applications, hardware etc.), local administrator privileges, and the capability of remote connection to the corporate network for staff who do not need this level of access and privilege. This applies to the control of access rights at the domain level as well as at the level of application software: browsers do not typically need access to other processes’ memory, while Microsoft Office does not need to install drivers.
For an example of environment redundancy, we can think of a regular corporate employee (not a developer, tester, administrator or information security specialist) whose desktop has software designed for network traffic interception, scanning the network, remote access, creation of local HTTP/FTP servers, use of third-party network hardware (Wi-Fi and/or 3G modems), software development tools etc.
Any effective strategy to prevent attacks from within the corporate network must prevent cybercriminals from acting secretly, and force them to take complicated and risky steps that betray their plans to information security specialists who can neutralize the threat. For that, two things must be present in the corporate network: smart security and an information security management system.
If you marry these two technologies you create a fundamentally different animal from the established information security model. It can see everything that takes place in the system and immediately reacts to threats.
Smart security tools include some antiviruses, firewalls, IDS/IPS/HIPS, Application Control, Device Control – however they must be capable of interacting with the information security management system. These security tools should not only collect all types of information and send it to the information security management system, but also execute commands that block attempts to gain access, establish connections, transfer data via the network, launch applications, read and write files etc. Naturally, for all of this to work, an information security specialist must be able to differentiate between legitimate and malicious activity.
Security holes in corporate networks: network vulnerabilities






















Marivic Arevalo
Good day,
Have encountered this and had my phones/(IPhone/IPad, Note 5) and 2 laptops affected, including the desktops in the office. And now, I believe they are using the Kaspersky Lab.
Thanks,
Marivic