
Main facts
- Kaspersky ICS CERT has uncovered a number of spyware campaigns targeting industrial enterprises. Operators of these campaigns hunt for corporate credentials, aiming to commit financial fraud or to sell them to other malicious actors.
- Spearphishing emails with malicious attachments sent from compromised corporate mailboxes to their contacts.
- The attackers use off-the-shelf spyware, but limit the scope and lifetime of each sample to the bare minimum
- SMTP services of industrial enterprises are abused not only to send spearphishing emails but also to collect data stolen by spyware as a one-way C2.
- Up to 45 % of all computers attacked appear to be ICS-related (and having access to the corporate email service).
- Overall, we have identified over 2,000 corporate email accounts belonging to industrial companies stolen and abused as next-attack C2.
- Many more (over 7K in our estimation) have been stolen and sold on the web or abused in other ways.
“Anomalous” spyware attacks
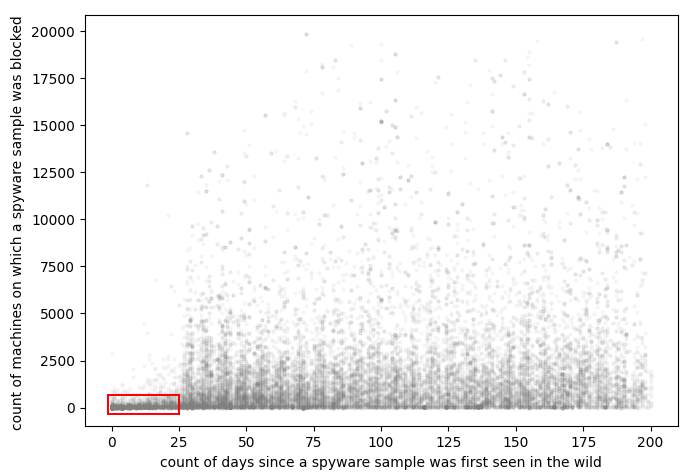
In 2021, Kaspersky ICS CERT experts noticed a curious anomaly in statistics on spyware threats blocked on ICS computers. Although the malware used in these attacks belongs to well-known commodity spyware families (such as AgentTesla/Origin Logger, HawkEye, Noon/Formbook, Masslogger, Snake Keylogger, Azorult, Lokibot, etc), these attacks stand out from the mainstream due to a very limited number of targets in each attack and a very short lifetime of each malicious sample, as shown in the red rectangle on the chart below.
Spyware samples blocked on ICS computers in H1 2021, by number of machines (targets) and number of days passed since first seen
The lifespan of the “anomalous” attacks is limited to about 25 days. And at the same time, the number of attacked computers is less than 100, of which 40-45% are ICS machines, while the rest are part of the same organizations’ IT infrastructure.
This has become a trend: around 21.2% of all spyware samples blocked on ICS computers worldwide in H1 2021 were part of this new limited-scope short-lifetime attack series and, depending on the region, up to one-sixth of all computers attacked with spyware were hit using this tactic.
C2 infrastructure
Unlike generic spyware, the majority of “anomalous” samples were configured to use SMTP-based (rather than FTP or HTTP(s)) C2s as a one-way communication channel, which means that was planned solely for theft.

Distribution of spyware samples by C2 type, “anomalous” vs. generic (download)
Tactics, techniques, and procedures
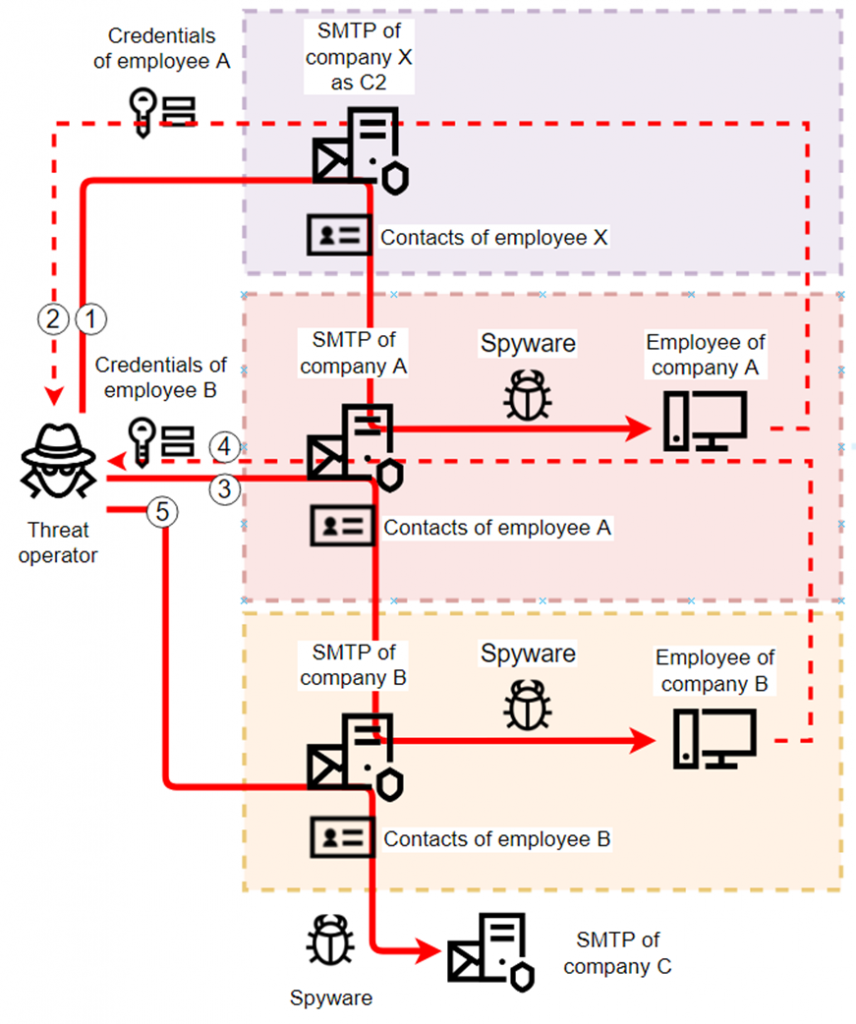
We believe that initially stolen data is used by threat operators primarily to spread the attack inside the local network of the attacked organization (via phishing emails) and to attack other organizations in order to collect more credentials.
The attackers use corporate mailboxes compromised in earlier attacks as the C2 servers for new attacks.
Amongst attacks of this kind, we’ve noticed a large set of campaigns that spread from one industrial enterprise to another via hard-to-detect phishing emails disguised as the victim organizations’ correspondence and abusing their corporate email systems to attack through the contact lists of compromised mailboxes.
Credential collection and abuse by threat actors
Curiously, corporate antispam technologies help the attackers stay unnoticed while exfiltrating stolen credentials from infected machines by making them ‘invisible’ among all the garbage emails in spam folders.
Overall, we have identified over 2,000 corporate email accounts belonging to industrial companies abused as next-attack C2 servers as a result of malicious operations of this type. Many more (over 7K in our estimation) have been stolen and sold on the web or abused in other ways.
Malware operators
Most of the attacks are operated independently by low-skilled individuals and small groups. The majority are aimed at directly committing financial crimes. But some hunt for credentials used to access corporate network services (SMTP, SSH, RDP, VPN, etc.), to sell them in web marketplaces.
Marketplaces
In this research, we identified over 25 different marketplaces where data stolen in the credential gathering campaigns targeting industrial companies that we investigated was being sold. At these markets, various sellers offer thousands of RDP, SMTP, SSH, cPanel, and email accounts, as well as malware, fraud schemes, and samples of emails and webpages for social engineering.
A statistical analysis of metadata for over 50,000 compromised RDP accounts sold in marketplaces shows that 1,954 accounts (3.9%) belong to industrial companies.

Compromised RDP accounts sold in marketplaces by types (download)
More information is available on the Kaspersky ICS CERT website.
Recommendations
We recommend taking the following measures to ensure adequate protection of an industrial enterprise, its partner network operations, and business:
- Consider implementing two-factor authentication for corporate email access and other internet-facing services (including RDP, VPN-SSL gateways, etc.) that could be used by an attacker to gain access to your company’s internal infrastructure and business-critical data.
- Make sure that all the endpoints, both on IT and OT networks, are protected with a modern endpoint security solution that is properly configured and is kept up-to-date.
- Regularly train your personnel to handle their incoming emails securely and to protect their systems from malware that email attachments may contain
- Regularly check spam folders instead of just emptying them
- Monitor the exposure of your organization’s accounts to the web
- Consider using sandbox solutions designed to automatically test attachments in inbound email traffic; make sure your sandbox solution is configured not to skip emails from “trusted” sources, including partner and contact organizations. No one is 100% protected from a compromise.
- Test attachments in outbound emails, as well. This could give you a chance to realize you’re compromised.
Campaigns abusing corporate trusted infrastructure hunt for corporate credentials on ICS networks




















Anjana
what about O365 users?