
TV Series such as “The Simpsons” are hugely popular and have hundreds of thousands of fans around the world. Unlike “Southpark” – another hugely popular series – not all of them are freely available on the web though. As such, there is a high demand on the web for such episodes and as usually happens, scam tactics appear around them.
Here’s one such example that we have seen recently on the popular website Dailymotion:
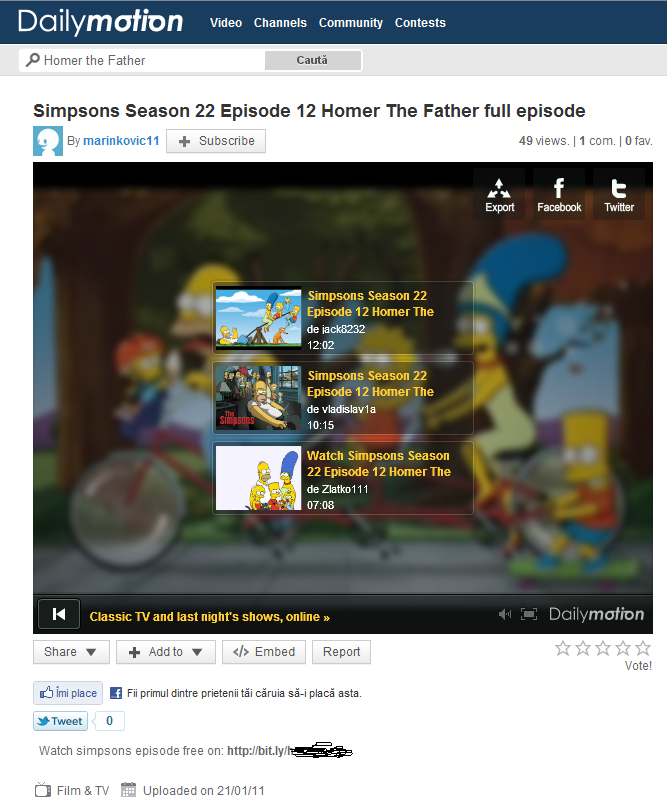
When trying to watch the pirate episode, a message will appear on screen claiming that the content has been removed due to copyright issues, but luckily you can still watch it at a special URL posted in the description field.
These URLs are always shortened (or masked) with services such as bit.ly, and clicking on them leads us to:
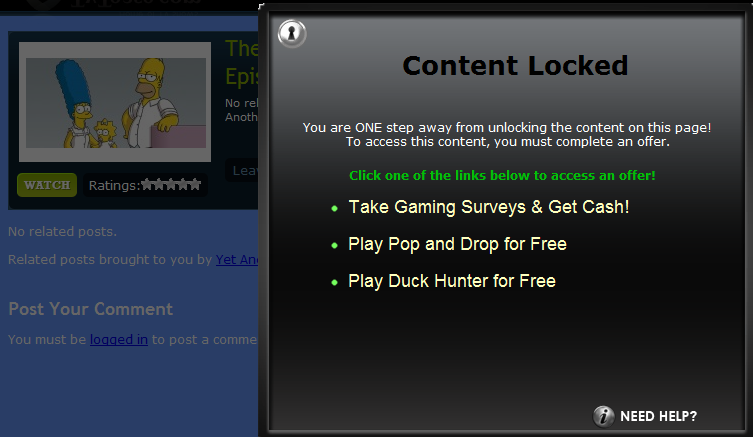
Once again, the content is not available immediately and to watch it one needs to access a special “offer”. Clicking on any of the offer links leads further to another page:
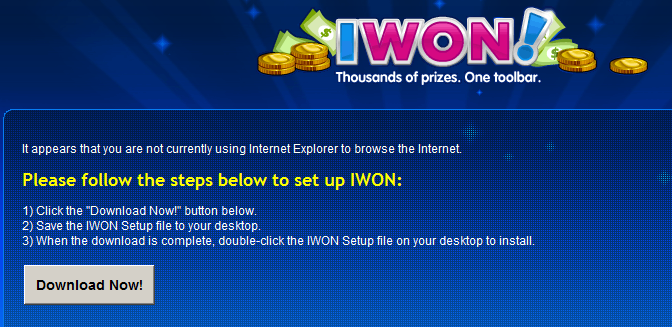
“IWON” (example file name: IWONSetup2.3.76.6.ZLman000.exe) is actually the infamous MyWebSearch Adware type of application, detected by most AV products, though not all. (KAV detects it as not-a-virus:WebToolbar.Win32.MyWebSearch.fr)
Though this application is not directly malicious, you may want to stay away from it, since installing the app won’t bring Homer to your screen and in addition, as recently shown by my colleague Roel, online ads can indirectly infect your computer even when shown by brand programs.
Be safe!



















Pirate episodes scam