
Over the last few days, we received numerous reports of computers infected with fake anti-virus (scareware). The name of this particular culprit is Antivirus 8.
The interesting thing about these cases is that the users were getting fake anti-virus browser pop ups while not actively using the computer. During our research we noticed that these pop-ups would appear right when ICQ was fetching/displaying new ads.
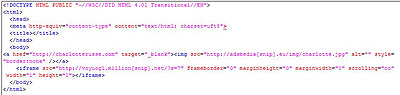
I installed ICQ and noticed the following after letting it run for a couple of minutes to fetch ads:
This page is hosted on [snip]charlotterusse.eu.
Going by the added iframe, it looks like this store’s ad server was hacked, right? Not quite. I did some digging around and found that none of these servers – other than charlotterusse.com – are actually related to this brand of clothing.
This means that somebody went through the trouble of pretending to be this store. This is done to make sure the ad distributor will actually run the campaign, as these distributors frequently get approached by fraudsters.
However, what makes this case particularly interesting is that the bad guys make it seem like their server got hacked.
By making it look like their server got compromised, the criminals can claim it isn’t them who’s responsible for distributing the malware. But rather someone else who hacked their server to spread malware.
The ad distributor is very likely to simply give them a warning, which gives these criminals at least one more shot at infecting more machines.
This is another example of how trusted programs can be a used to attack computers. It goes to show that anti-malware protection is needed no matter what the circumstance.
We’ve sent a notification to yieldmanager, who is the ad distributor in this case. We’ve not heard back from them at the time of writing.

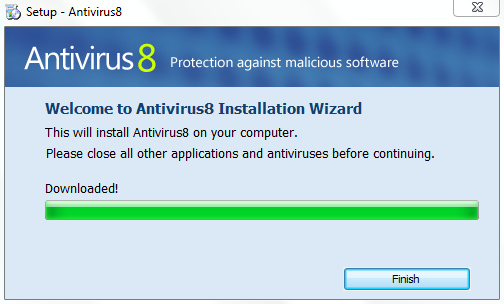



















Malicious ads through ICQ