
This month’s patch Tuesday is a sizable one by any standards, following the quiet Tuesday that my colleague Roel Schouwenberg described last month. Microsoft is patching a total of 34 vulnerabilities in 16 bulletins, MS11-038 through MS11-051. At least eight different Microsoft product lines are updated, and Adobe is coordinating release of Reader, Acrobat, Shockwave and Flash updates as well today.
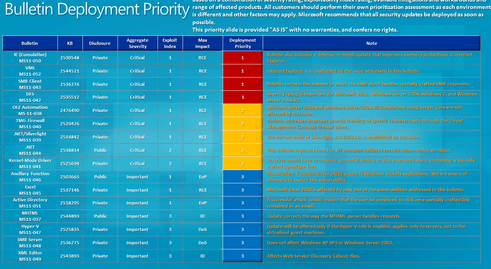
So we are looking at patching the following programs:
Microsoft Windows, Microsoft Office, Internet Explorer, .NET, SQL, Visual Studio, Silverlight, ISA and Adobe Reader, Acrobat, Shockwave and Flash player. More than half of the vulnerabilities being patched exist in the Internet Explorer and Microsoft Excel software components, frequent targets of drive-by and spear phishing attacks.
Most interesting is MS11-050, a single patch that knocks out 11 separate Internet Explorer vulnerabilities, some enabling information disclosure (cookiejacking), memory corruption and remote code execution: CVE-2011-1250, CVE-2011-1251, CVE-2011-1252, CVE-2011-1254, CVE-2011-1255, CVE-2011-1256, CVE-2011-1260, CVE-2011-1261, CVE-2011-1262. The additional VML patch MS11-052 knocks out another Internet Explorer vulnerability, CVE-2011-1266.
Microsoft already pointed out that the Internet Explorer patch addressing “cookiejacking” is not a particularly high risk issue because it is relatively unknown to them as an attack vector, and because there are more substantial social engineering techniques. While those points may be true, now that the techniques are more widely discussed, the risk of them being abused by more attackers goes up as well.
Eight different privately reported vulnerabilities are being patched in Microsoft Excel alone by MS11-045, each of which allow for remote code execution. We are still reviewing why the patch is rated “important” and not critical for the various Excel versions.
The patches that stand out result in remote code execution within Internet Explorer, Office and Silverlight. The recent history of attacks on consumer and corporate users, including the many successful spear phishing and APT attacks should help increase the urgency of these patches.
On the server side in the cloud, Microsoft is patching a vulnerability that could be abused in a DoS attack that could only be staged from within the cloud. MS11-047 is rated an “Important” patch for Windows 2008 versions, correcting a flaw in Hyper-V where a guest could send a malformed packet to the VMBus and result in denial of service on the server. MS11-039 is the Silverlight patch that could not only be used in a remote code execution attack on the client side, but also can be used to remotely run arbitrary code on vulnerable IIS web servers.
At least eight of the nine patches rated “Critical” requires a restart, be prepared for this interruption. We recommend applying all of this month’s released patches asap.






















Patch Tuesday June 2011