
The revolutions spreading across the Arab world have grabbed the attention of people across the globe, including cybercriminals: so-called ‘Nigerian’ spam emails have recently appeared claiming to be from a variety of “relatives” of Gaddafi and Mubarak. There’s absolutely nothing new about the messages they send: the ‘Nigerians’ don’t always introduce themselves as the solicitor of some anonymous oil tycoon or a dying widow of an innocent civil servant who was murdered; increasingly, they are legally-appointed executors or relatives of well-known people who have suffered in one way or other at the hands of political opponents.
For instance, some time ago we received an email from an Olga Patarkatsiashvili who wrote in poor English asking to help her transfer the millions of the late Badri Patarkatsiashvili (a Georgian businessman and presidential candidate who died in 2008), emphasizing that she herself has been denied access to his funds. Following the wave of protests affecting Arab countries there has been a steady stream of Egyptian- and Libyan-themed ‘Nigerian’ spam.
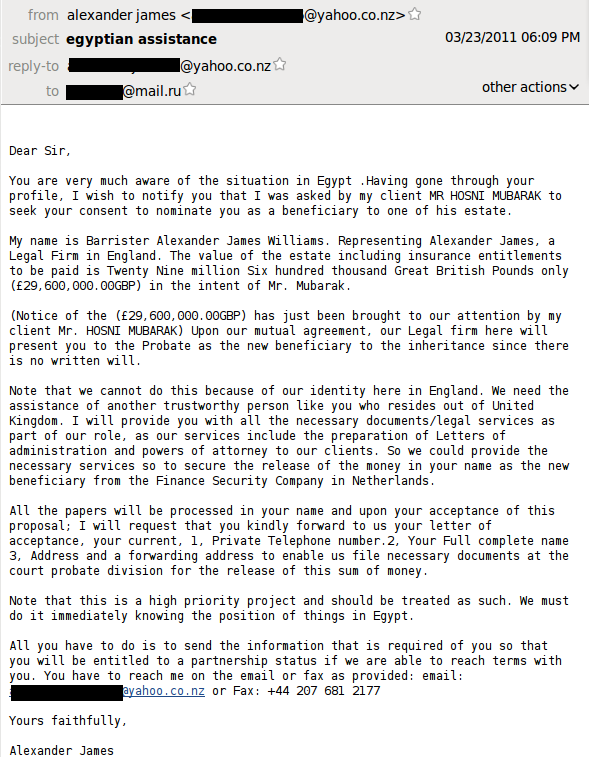
A certain Barrister Alexander James Williams, who claims to be a representative of Hosni Mubarak, asks for help in transferring 29 million pounds. He claims that a UK resident is required to process the transaction, but the email was sent to a Russian resident who has an account with the Russian email service mail.ru.
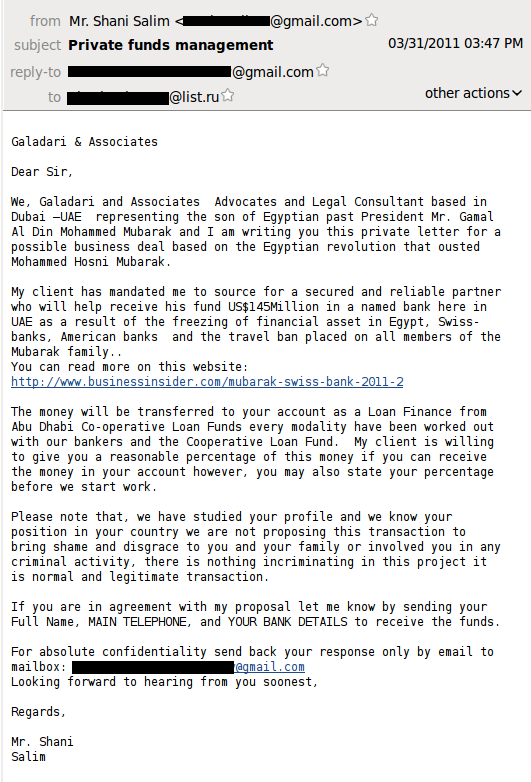
The legal firm Galadari and Associates based in Dubai and supposedly representing Hosni Mubarak’s son asks for help in transferring US$145 million (suggesting the son is considerably richer than his father). Notably, Galadari and Associates “have studied your profile and know your position”, and are therefore quite sure that the transaction will be a success.
In the third email from “the personal account officer of Hosni Mubarak”, the amount of money is not stated, though the message is the same: please help to transfer funds – we cannot do it ourselves because of the revolution.

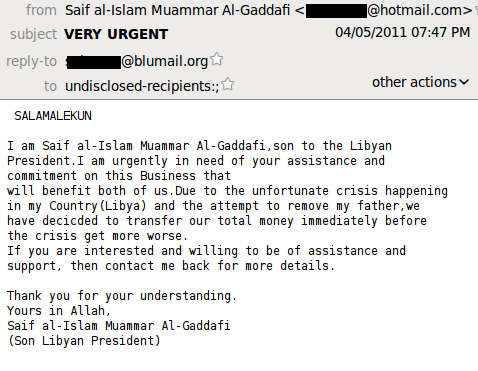
Emails from the family members of alleged victims have also come from Libya. Here is an email supposedly written by the “son” of Muammar Gaddafi who says his name is Saif al-Islam Al-Gaddafi. Together with his father they have decided to transfer their funds abroad “before the crisis get more worse”. So, you are welcome to help the president’s son “if you are interested and willing”!
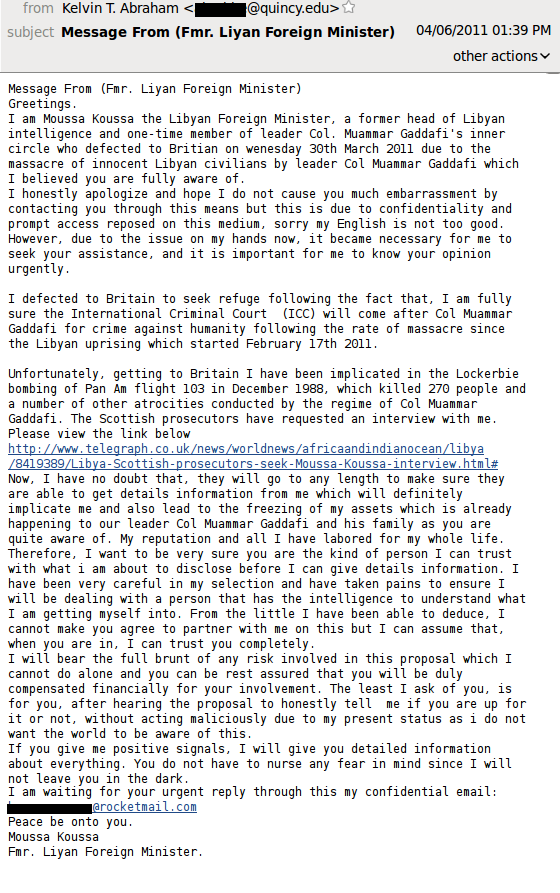
Moussa Koussa, Libya’s ex-minister of foreign affairs, does not state his purpose directly. He simply asks the recipient for help, obviously hoping to get someone’s attention and enter into correspondence and will most likely inform the interested partner the amount of money later. However, the address in the “From” field is a bit strange and looks as if the sender has forgotten to change it after a previous spam mailing.
Of course, the Internet is awash with such messages, with the number of references to the senders’ biographies as well as the number of mistakes varying from message to message. If nothing else, the criminals have once again demonstrated how quickly and flexibly they can react to the latest news – they simply modify their templates to suit the latest events, increasing the chances of someone falling for their scams.
So, while pseudo-benefactors collect funds for earthquake victims in Japan, those behind the ‘Nigerians’ letters are transferring millions of dollars from Hosni Mubarak and Muammar Gaddafi’s bank accounts.



















‘Nigerian’ spam from Egypt and Libya