
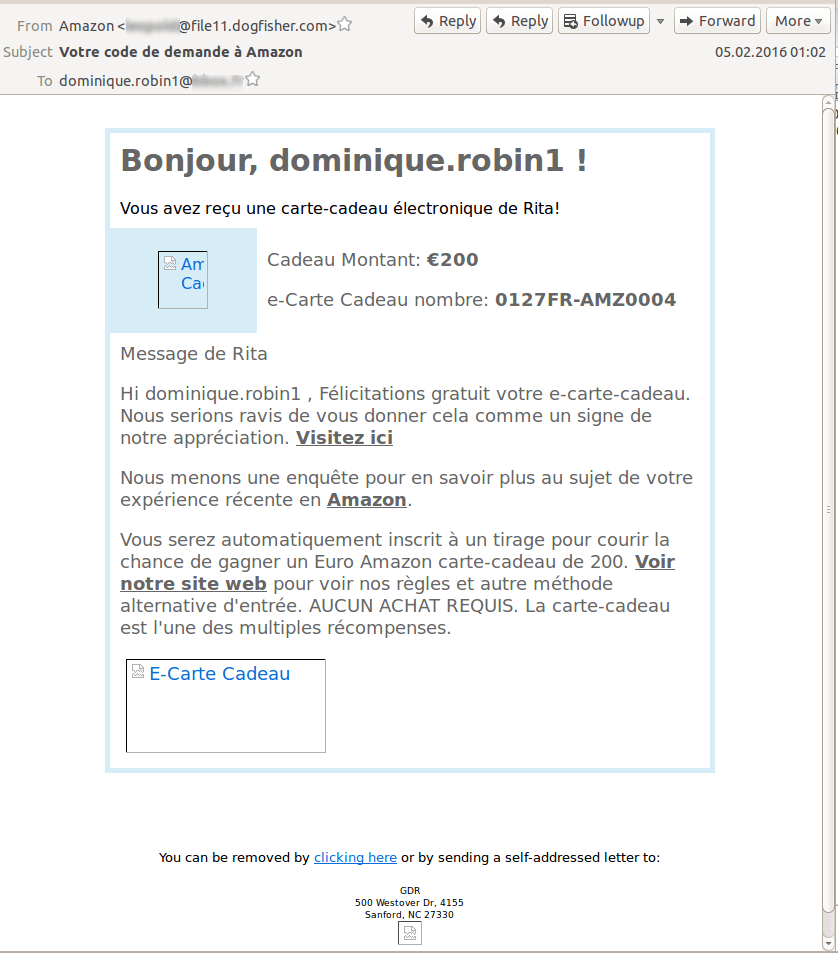
In recent weeks, we have seen several mass-mailings in French, Italian and English, imitating messages from Amazon’s online shops. In all the mailings, the recipients were offered a voucher, a gift certificate or some other prize.
The enticing offers were mostly sent from Italy or France. However, the email addresses from which they were sent immediately raised suspicions: the culprits didn’t even try to imitate Amazon’s official email addresses, and merely used Amazon in the sender’s name.
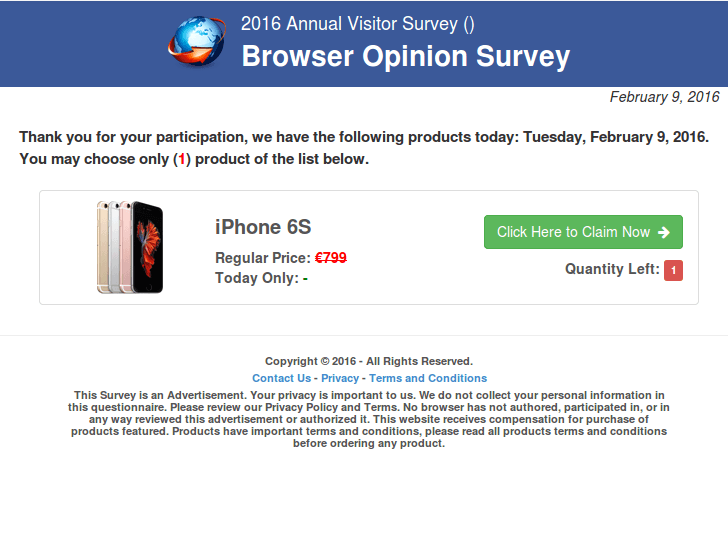
Each message contains links that supposedly lead to the Amazon website. The recipients have to click the links to claim their “prize”. Analysis of the links shows that users from different countries are redirected to different web pages. For instance, users with a European IP address are asked to fill in a form in English, and are offered the chance to enter a draw for an iPhone 6S as a reward.
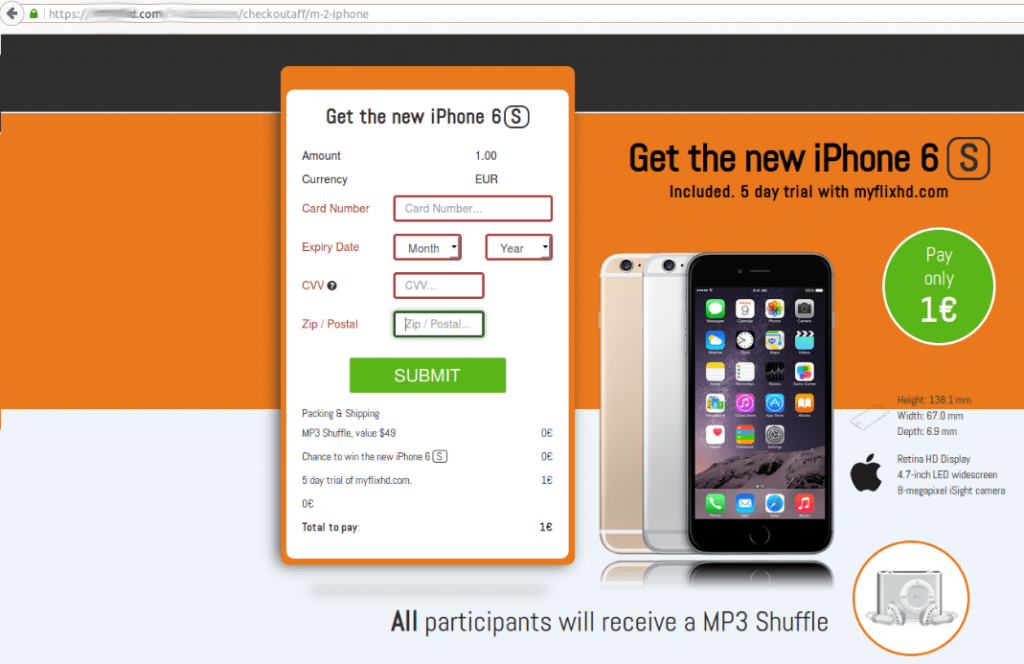
The winner is promised a new smartphone for just 1 euro, but first has to enter their bank card details on the video streaming site myflixhd[.]com.
The website offers a 5-day trial period, but requires the user’s bank card details, and then deducts a subscription fee of 50 euros per month if the user fails to cancel the subscription on time.
Naturally, Amazon has nothing to do with this “draw” or any other similar scams, and the chances of winning an iPhone 6S are very slim, to say the least. There is a good chance, however, that the bank card details entered on this advertising web page will be used by third parties for their own ends.
Amazon used as bait



















Timothy Sanford
I don’t know if anyone will agree with me, but, can Kaspersky find a person that’s willing to pay then follow the trail to where the money actually ends up, get a physical address then call police to arrest the scammers? Then person gets his/her money back.
I know some of you will say I watch too much tv, BUT it made me wonder if it’s actually possible??
Rick L.
What you describe is entirely possible until the step after the user pays. The perpetrator is almost certainly in a different country, and often in a location where the government is unwilling or unable to assist external law enforcement agencies in capturing its own citizens.
samuel
and what about interpol?