
Two days ago we intercepted a new APT campaign using a new MacOS X backdoor variant targeted at Uyghur activists.
But before we go into details, let’s start with a quiz:
– The Dalai Lama walks into an Apple Store. Why?
A possible answer is, “to buy one of the new MacBook Pro’s with the Retina display!” (speaking of which, I would very much like to buy one of those as well, but it’s kind of difficult to justify the hit to the family budget)
Joke aside, actually Dalai Lama is a well known Mac user. Here’s a photo of him using a Mac during a conf call:

And a better one of him using a 17” MacBook Pro:

Perhaps it is no surprise that we are seeing an increase in the number of APT attacks against such high profile users using Mac’s.
On June 27th, we’ve intercepted a new wave of APT attacks targeting certain Uyghur Mac users.
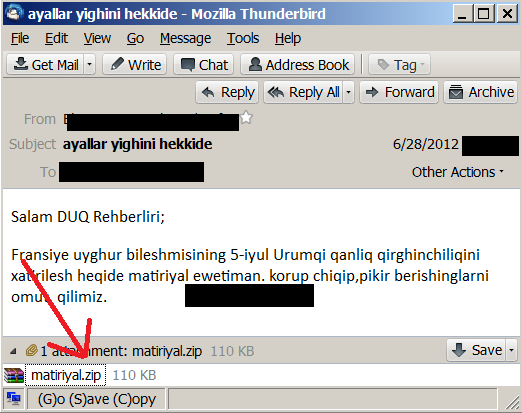
The e-mails have a ZIP file attached. Inside the ZIP file, there’s a JPG photo and a MacOS X app:
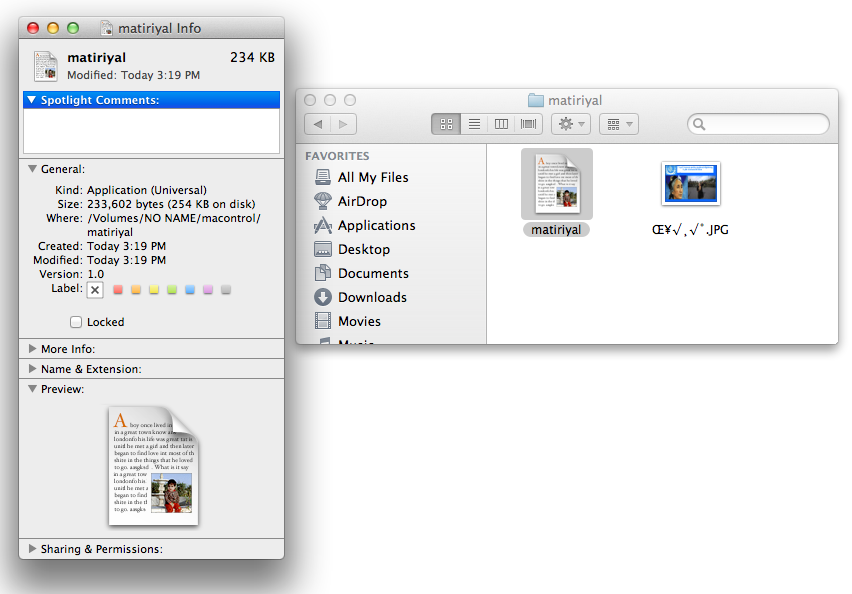
The application is actually a new, mostly undetected version of the MaControl backdoor (Universal Binary), which supports both i386 and PowerPC Macs. We detect it as “Backdoor.OSX.MaControl.b”.
MD5 ( “matiriyal.app/Contents/MacOS/iCnat” ): e88027e4bfc69b9d29caef6bae0238e8
When executed, it installs itself in the system and connects to its Command and Control server to get instructions. The backdoor allows its operator to list files, transfer files and generally, run commands on the infected machine.
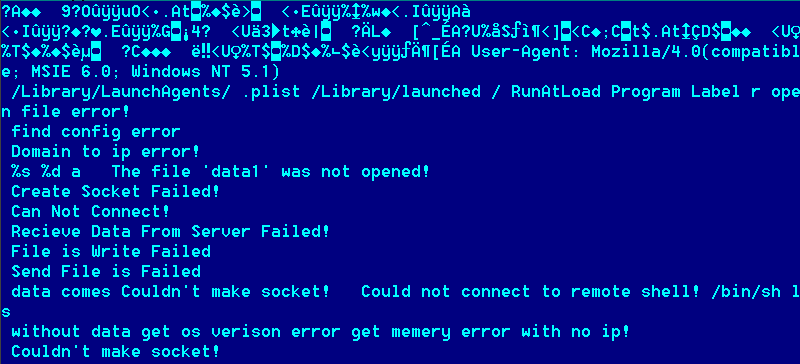
As usual, although some of the comments and debug info are in English, they contain common mistakes:
– “Recieve” instead of “Receive”
– “os verison” instead of “os version”
– “memery” instead of “memory”
– Etc…
The backdoor is quite flexible – its Command and Control servers are stored in a configuration block which has been appended at the end of the file, 0x214 bytes in size. The configuration block is obfuscated with a simple “substract 8” operation.

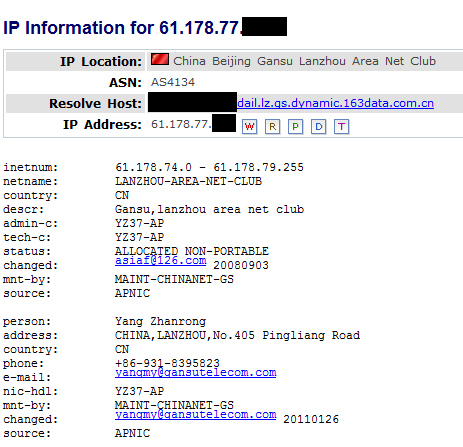
Once decrypted, the command and control server address can be read: 61.178.77.*, located in China:
With Macs growing in popularity and their increased adoption by high profile targets, we expect the number of MacOS X APT attacks will also grow. Previous attacks used MS Office exploits (Exploit.MSWord.CVE-2009-0563.a.); the one described here relies on social engineering to get the user to run the backdoor. Just like with PC malware, a combination of exploits and social engineering tricks are generally the most effective; it won’t be surprising to see a spike in such attacks soon.
Update: AlienVault posted a description of the Windows counterpart of the backdoor used in this attack. You can read their analysis here.



















New MacOS X backdoor variant used in APT attacks