
Malicious programs detected on users’ computers
The first Top Twenty lists malicious programs, adware and potentially unwanted programs that were detected and neutralized when accessed for the first time, i.e. by the on-access scanner.
| Position | Change in position | Name | Number of infected computers |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir | 330305 |
| 2 |  New New |
Net-Worm.Win32.Kido.iq | 174351 |
| 3 |  -1 -1 |
Net-Worm.Win32.Kido.ih | 145332 |
| 4 |  0 0 |
Virus.Win32.Sality.aa | 128737 |
| 5 |  0 0 |
Worm.Win32.FlyStudio.cu | 93848 |
| 6 |  -3 -3 |
not-a-virus:AdWare.Win32.Boran.z | 84825 |
| 7 |  -1 -1 |
Trojan-Downloader.Win32.VB.eql | 63287 |
| 8 |  9 9 |
Trojan-Downloader.WMA.GetCodec.s | 48426 |
| 9 |  1 1 |
Virus.Win32.Virut.ce | 47812 |
| 10 |  -3 -3 |
Virus.Win32.Induc.a | 46252 |
| 11 |  -2 -2 |
Worm.Win32.AutoRun.awkp | 36453 |
| 12 |  -4 -4 |
Packed.Win32.Black.d | 36422 |
| 13 |  -2 -2 |
Packed.Win32.Black.a | 35094 |
| 14 |  -1 -1 |
Trojan-Dropper.Win32.Flystud.yo | 34638 |
| 15 |  -3 -3 |
Worm.Win32.AutoRun.dui | 32493 |
| 16 |  -1 -1 |
Packed.Win32.Klone.bj | 31963 |
| 17 |  1 1 |
Worm.Win32.Mabezat.b | 29804 |
| 18 |  New New |
Packed.Win32.Krap.ag | 26041 |
| 19 |  New New |
Trojan-GameThief.Win32.Magania.ckqi | 25529 |
| 20 |  New New |
Trojan.Win32.Genome.bjgu | 24730 |
Overall, there was little change to the first rating, although there are a few points worth highlighting.
First of all, there is the new entry of Kido.iq that came straight in at 2nd place. This malicious program has very similar functionality to the leader, Kido.ir, which entered the ratings back in September.
Secondly, GetCodec.s rose 9 places overall, with the number of computers on which GetCodec was detected more than doubling in November. To recap, GetCodec.s spreads together with P2P-Worm.Win32.Nugg, just like GetCodec.r which we wrote about last December. It looks as though cybercriminals are making another attempt to spread P2P-Worm.Win32.Nugg via the Gnutella file sharing network Gnutella (and in this case, using the popular LimeWire application). This worm downloads other malicious programs, which act as an additional threat to users’ computers.
Another newcomer of note is Packed.Win32.Krap.ag. Just as other representatives of the Packed family do, Krap.ag detects a special packing program used to pack malicious programs. In this particular case, the malicious programs, which are concealed by a standard, but modified, packing program, are fake antivirus programs such as those we wrote about recently. In other words, 18th place in the rankings is effectively occupied by a rogue antivirus solution.
After returning to the ratings the Magania family of gaming Trojans has held on to 19th place, albeit with the new version Magania.ckqi replacing last month’s entry Magania.cbrt.
Malicious programs on the Internet
The second Top Twenty presents data generated by the web antivirus component, and reflects the online threat landscape. This ranking includes malicious programs detected on web pages and malware downloaded to victim machines from web pages.
| Position | Change in position | Name | Number of attempted downloads |
| 1 |  0 0 |
Trojan-Downloader.JS.Gumblar.x | 1714509 |
| 2 |  1 1 |
Trojan-Downloader.HTML.IFrame.sz | 189881 |
| 3 |  New New |
Trojan-Clicker.JS.Iframe.be | 170319 |
| 4 |  0 0 |
not-a-virus:AdWare.Win32.Boran.z | 136748 |
| 5 |  0 0 |
Trojan.JS.Redirector.l | 130271 |
| 6 |  New New |
Trojan.JS.Ramif.a | 115163 |
| 7 |  1 1 |
Trojan.JS.Agent.aat | 55291 |
| 8 |  -2 -2 |
Trojan-Clicker.HTML.Agent.aq | 47873 |
| 9 |  New New |
Trojan.HTML.Fraud.r | 47473 |
| 10 |  -8 -8 |
Trojan-Downloader.JS.Gumblar.w | 41977 |
| 11 |  New New |
Trojan.JS.Iframe.dy | 35152 |
| 12 |  -5 -5 |
Trojan-Downloader.JS.Zapchast.m | 31161 |
| 13 |  New New |
Trojan-Downloader.JS.IstBar.cy | 30806 |
| 14 |  New New |
Trojan-Clicker.JS.Iframe.u | 30553 |
| 15 |  Return Return |
Trojan-Downloader.JS.Psyme.gh | 30078 |
| 16 |  New New |
Trojan-Downloader.HTML.FraudLoad.b | 29466 |
| 17 |  New New |
Trojan-Clicker.HTML.IFrame.ajn | 29455 |
| 18 |  New New |
Trojan.JS.PrygSkok.a | 27804 |
| 19 |  New New |
Packed.Win32.Krap.ag | 26770 |
| 20 |  -5 -5 |
Trojan-Downloader.JS.LuckySploit.q | 26175 |
Gumblar continues to dominate this rating with a huge gap separating it from the program in 2nd place. The number of unique attempts to download this malicious program increased nearly four times in November.
The latest Gumblar attack, which we described last month, continued unabated in November. Unlike the attack six months earlier this time all the components – the downloader, the exploits and the main executable file – were replaced or modified with alarming regularity.
Rogue antivirus programs also made it into the second rating. One method of spreading these programs is by downloading them to users’ machines from websites that are created using the same template and which are part of cybercriminal affiliate, or partner, programs. The web pages most commonly used to download fake antivirus solutions in November are detected by us as Trojan.HTML.Fraud.r and Trojan-Downloader.HTML.FraudLoad.b. Packed.Win32.Krap.ag, mentioned above, was also downloaded from these pages and this explains why it makes an appearance in the second Top 20 as well.
The other new entries (script downloaders which vary in sophistication and the degree of obfuscation used) follow recent trends.
November trends
The overall picture remained unchanged in November. At the moment, the most common strategy for spreading malware is to use a malicious script + exploit + executable file. More often than not, this is how malware designed to steal confidential data or extort money from users is spread. Such malware includes programs such as Trojan-PSW.Win32.Kates (the Gumblar attacks are primarily designed to download this malware); Trojan-Spy.Win32.Zbot, an extremely widespread Trojan that actively spreads using script downloaders and varied spam mass mailings; and numerous fake antivirus programs.
Another marked trend of recent months that continued in November was the use of websites created using standardized templates to spread rogue antivirus solutions.
Cybercriminals are also aggressively using packers (usually polymorphic) in the hope that this will help the packed malicious programs avoid detection, so they won’t have to make significant modifications to the malicious programs themselves.
This month malware was also distributed via P2P networks using multimedia downloader programs, a method that the cybercriminals made use of last December.
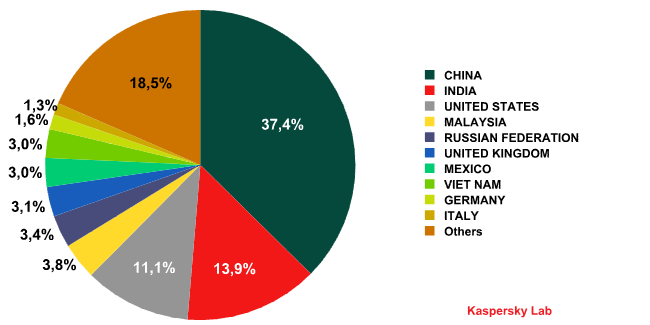
Countries where most attempts to infect via the web originated.

















Monthly Malware Statistics: November 2009