
Vulnerabilities continue to be detected and successfully exploited in Adobe’s most popular products – Acrobat and Reader.
Some days ago we received an interesting PDF file (detected as Exploit.JS.Pdfka.bui) which contained an exploit for the CVE-2010-0188 vulnerability, which was originally discovered back in February in Acrobat/Reader version 9.3 and earlier.
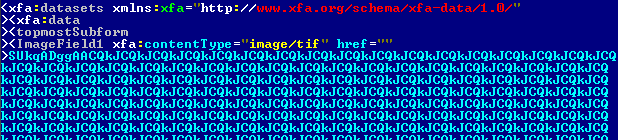
The first thing that catches the eye is the intentionally malformed TIFF image inside the PDF file.
The vulnerability – a buffer overflow – manifests itself when the field containing the image is accessed. The attack is carried out using ‘heap spraying’, a technique popularly used by many exploits on products capable of running JavaScript code, the recent Aurora attack being a good example of this technique in action.If the vulnerability mentioned above is exploited successfully, the return address is overwritten with the predefined address 0xC0C0C0C0. This being where the code controlled by cybercriminals is located.
After this it jumps to an address containing a shellcode, which initially decrypts its body and then the executable file, which is also embedded into the original PDF file.
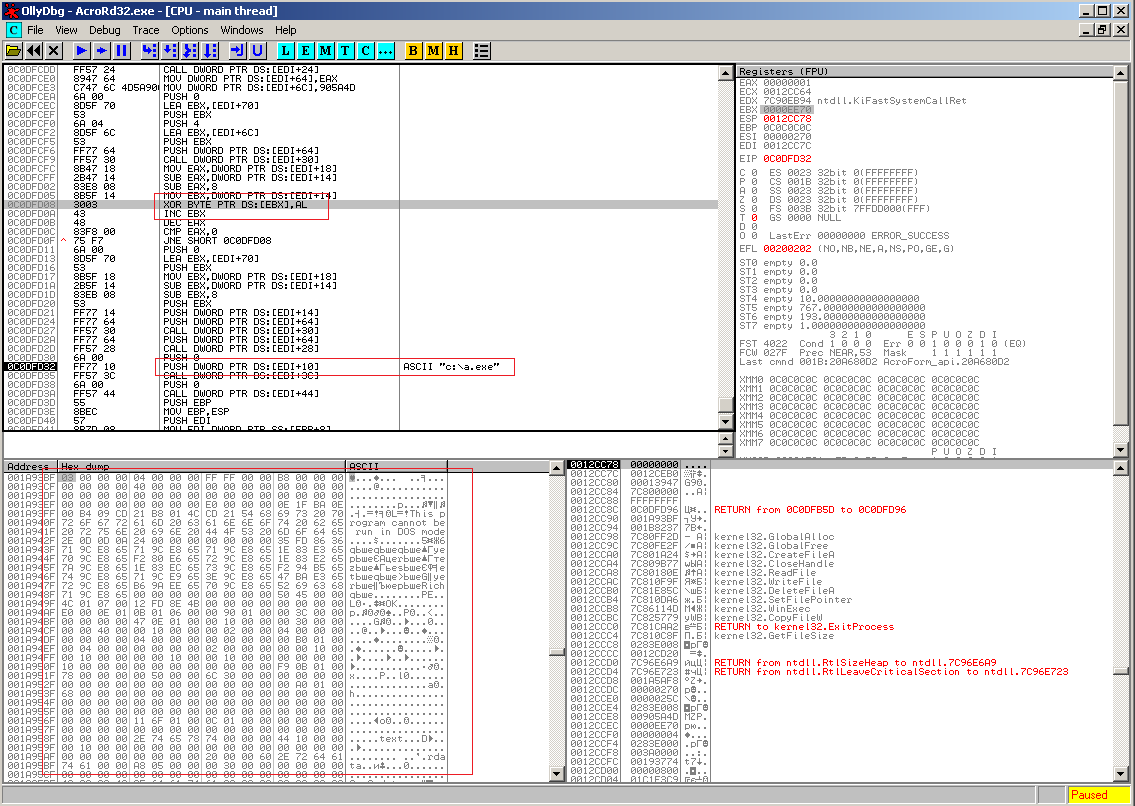
The decrypted executable file (detected as Backdoor.Win32.Agent.aqoj) is written into the root folder of the C: drive and launched. Its purpose is to send data about the victim’s computer to a remote server and download other malicious files to the infected machine.
Adobe was quick to release an update for the affected products. However, this won’t deter the cyber criminals because, as past experience shows, users are slow to update their machines and the bad guys won’t hesitate to exploit the vulnerability in the meantime. In order to avoid this infection and others like it, we strongly recommend installing the latest updates for Acrobat and Reader.


















Adobe yet again