
Malicious programs detected on users’ computers
The first Top Twenty lists malicious programs, adware and potentially unwanted programs that were detected and neutralized when accessed for the first time, i.e. by the on-access scanner.
| Position | Change in position | Name | Number of infected computers |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir | 332833 |
| 2 |  0 0 |
Virus.Win32.Sality.aa | 211229 |
| 3 |  0 0 |
Net-Worm.Win32.Kido.ih | 186685 |
| 4 |  0 0 |
Net-Worm.Win32.Kido.iq | 181825 |
| 5 |  0 0 |
Worm.Win32.FlyStudio.cu | 121027 |
| 6 |  0 0 |
Trojan-Downloader.Win32.VB.eql | 68580 |
| 7 |  New New |
Trojan.Win32.AutoRun.abj | 66331 |
| 8 |  1 1 |
Virus.Win32.Virut.ce | 61003 |
| 9 |  1 1 |
Packed.Win32.Krap.l | 55823 |
| 10 |  -2 -2 |
Worm.Win32.AutoIt.tc | 55065 |
| 11 |  4 4 |
Worm.Win32.Mabezat.b | 49521 |
| 12 |  -5 -5 |
Exploit.JS.Aurora.a | 43776 |
| 13 |  New New |
Packed.Win32.Krap.as | 40912 |
| 14 |  New New |
Trojan.Win32.AutoRun.aay | 40754 |
| 15 |  3 3 |
Trojan-Dropper.Win32.Flystud.yo | 40190 |
| 16 |  -4 -4 |
Virus.Win32.Induc.a | 38683 |
| 17 |  -4 -4 |
not-a-virus:AdWare.Win32.RK.aw | 38547 |
| 18 |  New New |
Trojan.Win32.AutoRun.abd | 37037 |
| 19 |  -5 -5 |
not-a-virus:AdWare.Win32.Boran.z | 36996 |
| 20 |  0 0 |
not-a-virus:AdWare.Win32.FunWeb.q | 34177 |
There was no major change in the first Top Twenty leader board in March.
Three variants to the Autorun Trojan are worthy of mention. As was the case a couple of months back, they are autorun.inf files that use removable devices to spread the notorious P2P-Worm, Win32.Palevo and Trojan-GameThief.Win32.Magania.
This month’s rating once again has an entry displaying ‘packed’ characteristics, and this time it’s called Packed.Win32.Krap.as and conceals a rogue antivirus program. Currently this is in thirteenth place. In recent months the cybercriminals have demonstrated a penchant for specially designed packers of executable files. New methods of packing and concealing the true function of popular malware are being developed all the time, which explains why new variants of families such as Krap appear in our Top Twenty virtually every month.
Malicious programs on the Internet
The second Top Twenty presents data generated by the web antivirus component, and reflects the online threat landscape. This ranking includes malicious programs detected on web pages and malware downloaded to victim machines from web pages.
| Position | Change in position | Name | Number of attempted downloads |
| 1 |  0 0 |
Trojan-Downloader.JS.Gumblar.x | 178965 |
| 2 |  New New |
Exploit.JS.CVE-2010-0806.i | 148721 |
| 3 |  -1 -1 |
Trojan.JS.Redirector.l | 126277 |
| 4 |  2 2 |
Trojan-Clicker.JS.Iframe.ea | 102226 |
| 5 |  4 4 |
Exploit.JS.Aurora.a | 88196 |
| 6 |  4 4 |
Trojan.JS.Agent.aui | 80654 |
| 7 |  -3 -3 |
not-a-virus:AdWare.Win32.Boran.z | 75911 |
| 8 |  New New |
Trojan.HTML.Fraud.aj | 68809 |
| 9 |  New New |
Packed.Win32.Krap.as | 64329 |
| 10 |  New New |
Exploit.JS.CVE-2010-0806.b | 50763 |
| 11 |  New New |
Trojan.JS.FakeUpdate.ab | 49412 |
| 12 |  New New |
Trojan.HTML.Fraud.aq | 48927 |
| 13 |  3 3 |
Packed.Win32.Krap.ai | 47601 |
| 14 |  Return Return |
Trojan-Downloader.JS.Twetti.a | 46858 |
| 15 |  New New |
Exploit.JS.Pdfka.bub | 45762 |
| 16 |  New New |
Trojan-Downloader.JS.Iframe.byo | 44848 |
| 17 |  New New |
Trojan.JS.FakeUpdate.aa | 42352 |
| 18 |  Return Return |
not-a-virus:AdWare.Win32.Shopper.l | 41888 |
| 19 |  New New |
Trojan-Clicker.HTML.IFrame.fh | 38266 |
| 20 |  New New |
Packed.Win32.Krap.ao | 36123 |
As usual, when it comes to rating malicious programs on the Internet, there was plenty to discuss.
Let’s start with the latest Internet Explorer vulnerability CVE-2010-0806. A rather detailed description of the problem led to the exploit for it becoming extremely widespread. Now only the laziest of cybercriminals haven’t hopped on the bandwagon and two variants are already in our second Top Twenty – Exploit.JS.CVE-2010-0806.i (in second place) and Exploit.JS.CVE-2010-0806.b (in tenth place).
The latest Gumblar epidemic is still in full swing. As well as the older version of this script Trojan-Downloader, which shows up as Gumblar.x and occupies first place, a new updated version has appeared which is detected as HEUR:Trojan-Downloader.Script.Generic.
The Aurora.a exploit, which we wrote about last month, is still being used extensively by cybercriminals and has risen from ninth to fifth place in our rating.
The rather curious Twetti.a downloader, which we wrote about back in December, reared its none-too-pleasant head again in March, coming in at fourteenth place after a two-month hiatus. As was the case with Gumblar, it appears the black hats took some time-out and then started using this piece of malware to infect large numbers of websites again.
It’s also no coincidence that Exploit.JS.Pdfka.bub finds itself in fifteenth place – this malicious PDF file is a component in drive-by attacks that use Twetti.a to get a foot in the door.
Our second rating also includes four new entries – Trojan.HTML.Fraud.aj, Trojan.JS.FakeUpdate.ab, Trojan.HTML.Fraud.aq and Trojan.JS.FakeUpdate.aa – that distribute fake antivirus solutions and ransomware.
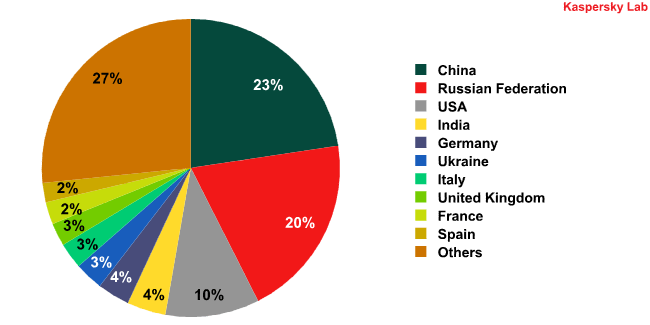
Countries launching the most web-borne infections:
The overall picture remains pretty much unchanged: attacks on users are predominantly Internet-borne and make use of the vulnerabilities that regularly appear in some of the most popular software products. Fortunately, these vulnerabilities are quickly patched by the vendors, but still, too many users fail to install these patches in time. Malware is also increasingly taking advantage of user gullibility and naivety. The most common malware of this kind used by the cybercriminals in March included rogue antivirus solutions and ransomware.



















Monthly Malware Statistics: March 2010