
What wonderful times we live in! Thanks to the development of the Internet, we can purchase things and pay for services quickly and easily. Things have become incredibly convenient. You don’t even have to get out of bed to go grocery shopping, or buy a yacht or a new home in a faraway country — and the selection is huge! It is now commonplace for people to play the stock markets and companies to undertake their business transactions online.
Naturally, in order to take advantage of these opportunities, we first have to log into the proper system and determine the account from which money will be sent.
Money! Money! Money!… Wherever there’s money, there are sure to be people nearby trying to get their hands on it. Even worse, some will surely try to pocket it even if it isn’t theirs. That’s how it goes in the world of e-money. Swindlers and scammers will try anything they can to get their hands on other people’s money, and the most surefire way to do it is to trick an online e-payment system into believing that the scammer is a legitimate account holder. Then they can do whatever they like with the funds in the victim’s account.
The most common method to make a system believe that you are authorized to access and manage an e-money account is to provide the owner’s name (or the credit card number, or a registered pseudonym, etc.) and the correct password (or PIN code, codeword, etc.). This is usually sufficient for the system to ‘recognize’ the user. But how do scammers get hold of the users’ personal information in the first place? Malicious users have a powerful tool in their arsenals: Trojans. Cybercriminals use Trojans almost like a crowbar, to pull aside barriers and get their hands on just about any of the users’ information that they want, without the users even suspecting that their data has been stolen.
They’re out to get you…
It is fairly easy to pick up a malicious program when surfing the vast expanses of the Internet, if you don’t take any precautions, that is. Because software programs and operating systems are so complex, they often have a few weak spots that aren’t obvious to the untrained eye. However, these weak spots can and do lead to critical errors in unusual situations, such as when a user is working with data that may not have been factored in by the developers. These errors can be manipulated and used to launch a malicious program on the user’s system. Malicious programs come in all different shapes and sizes, but Trojans are the most common of all.
Users who click on links in emails or their IM client without thinking twice about it, or who visit an unknown (or sometimes a well-known, but hacked) website are in danger of downloading malware onto their computer. The malware will then reside on the user’s computer and do its dirty work without the user noticing a thing. In order to get the user to accept the malware’s actions as those of a normal, legitimate program, the Trojan will either penetrate system services and inject its code, or it will disguise itself as an important system service.
Once it has begun its evil work on your system, a Trojan will stay resident indefinitely provided that no antivirus protection is installed. Its functions may even include ‘spying’ on the user’s actions, the performance of the software that the user launches, and the data that the user enters or receives.
One of the most prolific threats to be found on the computers of unwary users is a specific type of Trojan spy known as ZBot. This name is a combination of the first letter of the Trojan author’s handle, ZeuS, and the word ‘bot’, which means a network robot: a program that automatically performs an assigned task. In this case, the task is to steal users’ personal data.
Dangerously adept
Trojans in the ZBot (ZeuS) family first appeared in 2007. Since their configuration is simple and they are easy to use to steal online data, ZeuS became one of the most widespread and best-selling of all the spyware programs available on the Internet’s black market.
Let us take a closer look at exactly why this Trojan poses such a major threat. Below is a quick overview of what this program can do once it infiltrates a victim’s system:
- Everything that you ‘remember’ on a computer (i.e., when you check the ‘remember my password’ box) becomes accessible to the Trojan, whether it’s your login name, your password, or any other kind of data entered into an automated field on a website.
- Even if you don’t mark anything to be automatically ‘remembered’, the Trojan will log any keystrokes you enter on your keyboard and the sequence of characters used to gain access to your online accounts will be ‘monitored’ and sent to the bot’s controllers.
- In order to prevent keystrokes and other data from being monitored, many websites use a special virtual keyboard. Users click the left mouse button on the keys of the virtual keyboard, which is visible on their monitors, to enter their password. In this case, ZeuS exploits a different mechanism to intercept user data: as soon as you push the left mouse button, ZeuS takes a screenshot, making it easy to identify the keys that you selected on the virtual keyboard.
- ZeuS controls all of the data that is transferred via your web browser. If you attempt to open a website that has already been logged by ZeuS’ configuration file, the Trojan may modify the website’s code before you even see it in the browser window. As a rule, the modifications will include the addition of new fields where users are asked to enter personal and private information. Let’s say your bank’s website suddenly asks you to enter information other than your username and password, like your PIN code, for example — and you are positive that you are viewing your bank’s official website. That’s the trick! The request for a PIN code was added by ZeuS, the actual code of the bank’s page does not include this request and never would. If the PIN code is entered, the Trojan will intercept it and send it to the malicious user controlling the Trojan.
- Some websites create a special digital signature for you when you register, and this is verified at each subsequent visit. If your browser does not submit the proper certificate to the site, then the website will not give you full access. If a computer is infected by ZeuS, the Trojan will find these security certificates, steal them and send them to the malicious user.
- If a malicious user needs your computer to take any unlawful actions (such as the sending of spam) then ZeuS will grant the malicious user the ability to install all of the software they need to accomplish this.
If your computer is infected by ZeuS, and if you have anything worth taking, then the cybercriminal will take it. However, if you have nothing worth taking, it doesn’t mean you’re in the clear either — it’s still pretty likely that your computer will be used for criminal purposes.
Infected computers that are under the control of a malicious user are used to form a botnet, also known as a zombie network. A malicious user controls the infected computers which make up their network just like a puppeteer manipulates their dolls. Users do not usually have the slightest suspicion that their computers are sending out spam or that a cyber criminal has hijacked their Internet connection in order to access the World Wide Web covertly. Victims may go for months blissfully unaware that their computers are being used as pawns in the criminals’ machinations.
Volatile and widespread
ZeuS is a very effective means of collecting data and setting up botnets, which can be used in a variety of ways to further the cybercriminals’ purposes. Its many uses make it the preferred choice of the discerning cybercriminal.
These days, nearly everyone who is maliciously inclined can get their hands on a copy of the ZeuS Trojan. It isn’t very difficult to customize the configuration file to suit one’s own ends and then use a special method to encrypt it, thus hiding its algorithm from antivirus programs. When purchasing the program, malicious users can even order a copy with add-on options that aren’t included in the basic code. ZeuS now has a solid foothold in the malware market.
Let’s take a look at how this Trojan became so widespread. The chart below shows the number of newly detected variants (samples) each month.
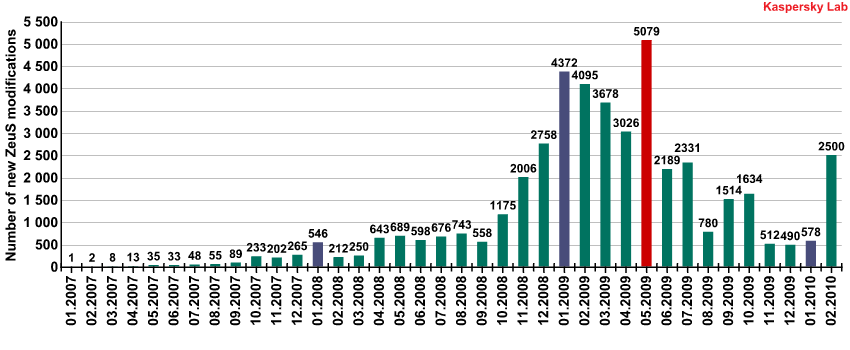
The number of new ZeuS variants each month (2007 – 2009)
Prior to autumn 2007, ZeuS was only distributed by its creator. In mid-2007, the Trojan’s author stopped selling his creation. You can read more about the history of ZeuS here. However, hackers somehow got hold of the ZeuS constructor.
You can find more detailed information about botnets in the following articles:
Enterprising cybercriminals began to work on modifications to the code and spreading new versions of the Trojan. Starting in October 2007, the number of ZeuS variants began to grow, and by 2008 the Trojan had found a regular client base. Up until September of that year there were no significant fluctuations in activity, just a steady flow of about five hundred new ZeuS variants per month.
A marked increase in the prevalence of ZeuS was noted in late 2008 and was most likely tied to the global economic downturn. Many programmers and experienced users alike ended up losing their jobs in the crisis. Under such conditions, it was hardly surprising that some of them ventured into ‘the dark side’ and decided to try their hand at Internet fraud. So, to whom did they turn? Most likely, they approached the sellers of ZeuS, a program that already had a proven track record.
ZeuS reached record numbers in May 2009 with 5,079 variants. Just imagine — over 5,000 versions of the same Trojan per month! It had essentially earned ‘bestseller’ status among malicious programs. Since the ways that could be used to encrypt the program’s code had, for the most part, become common knowledge, antivirus systems were able to recognize them and automatically include them in antivirus databases.
However, virus writers are always updating encryption algorithms, making it more difficult to analyze programs. For example, in early 2009, virus writers noted the increased demand for ZeuS and decided to make some major changes to the initial version of the Trojan. In particular, this included improving the encryption algorithm, the program code and the configuration file.
ZeuS changes its appearance regularly. Once it has infected a system, it updates itself using a variety of Internet addresses. For users whose computers download new variants of the Trojan, the antidotes aimed at previous variants won’t have much of an effect. Fast response times become critical in this case and antivirus analysts must be on their guard day and night. In the event that a new algorithm emerges that the system is not equipped to tackle, analysts must immediately respond with a means of protection against the variant.
Since the first version of ZeuS appeared, over 40,000 variants of this Trojan have been recorded. Based on the number of versions of the Trojan and the number of different addresses (often called ‘command centers’) hosting the malicious users’ data from which commands are sent to zombie machines, ZeuS is certainly one of the most popular pieces of malware around.
The scale of the infection
In order to get an idea of the extent to which ZeuS has spread, let us review some facts about the number of computers infected by this Trojan that are under the control of malicious users.
In 2009, a report was published in the US about the detection of 3.6 million computers infected by ZeuS within that country. This is an approximate figure, of course — the real number could easily be much higher. It is nearly impossible to estimate the actual number of infected machines, as it is unknown exactly how many computers have been infected since, especially home users who are unaware that their computers are infected.
Something strange happened in early 2009: about 100,000 computers suddenly stopped booting up, and all at around the same time. It later became clear that these computers had been taken over to form a ZeuS botnet and a command had been sent from the command center to destroy the user’s operating system (yes, it’s true — ZeuS is capable of this as well…). Analysts tried to figure out why this had happened, and came up with two possibilities: (1) a hacker had cracked the botnet’s command center and sent the command to infected computers in order to cause trouble for the botnet’s ‘owners’, or (2) the owners of the botnet had sent the command themselves after obtaining the information that they wanted. In the latter case, the malicious user would have been planning to use the extra time gained in order to withdraw funds from the victims’ accounts using the stolen data, whilst the victims tried to restore their decimated systems. However, the first scenario is actually more likely to have happened. Why? Well, around that time, the owner of a ZeuS botnet had shown up on a particular hacker forum asking for advice on how to protect his botnet against unauthorized access. He had lost control of his network of hundreds of thousands of infected machines after another hacker had broken into his botnet’s command center (these types of incidents are actually commonplace in hacker circles). What was surprising was that the cybercriminal did not appear overly concerned about the loss of hundreds of thousands of computers under his control because he had quickly set up two new botnets — one comprising around 30,000 computers, and the second approximately 3,000 infected machines.
The most recently detected large ZeuS botnet is the so-called Kneber botnet. In February 2010, the US-based corporate security company NetWitness reported the detection of ZeuS-infected computers in 2,500 organizations in 196 countries worldwide. A total of 76,000 infected computers were detected and all of them were linked to Internet addresses registered under the name of one person: Hilary Kneber, an alias, of course.
This was just the tip of the iceberg. Isolated incidents of botnet detection — bringing together groups of hundreds of thousands of infected computers — have raised the estimated numbers of instances of the so-called Zeusbot infection into the millions.
‘Preferred domains’
Each ZeuS configuration file indicates an Internet address that follows the Trojan on the victim’s computer. As soon as the user visits the webpage noted in the configuration file and enters their data, ZeuS intercepts it and forwards it to the malicious user.
Kaspersky Lab has analyzed nearly three thousand ZeuS configuration files and noticed a pattern to the Internet addresses.
We have divided the addresses by domain in order to identify the most commonly used top-level domain types:
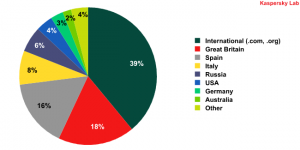
The top-level domains most commonly targeted by ZeuS
The most commonly targeted domains are, of course, the international domains .org and .com, which are predominantly owned by organizations and large companies.
Which kinds of .com websites does ZeuS target in particular? From which sites does the Trojan attempt to intercept personal information entered via infected computers? Fourteen leaders emerged from among the international websites:
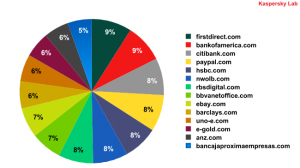
The most prevalent .com domains targeted by ZeuS
Just three of the eleven most common malicious user resources on the .com domain are not directly tied to banks — they are commercial Internet services. Paypal.com links the virtual money used in online transactions with real-world money in the form of credit and debit cards. Like PayPal, E-gold.com allows users to create an account with virtual payment units that can be used on the web to make financial payments and links these with the price of gold and other precious metals. eBay.com is a very popular Internet auction site that also uses online accounts through which users can put their goods up for auction. The remaining are the websites of transcontinental banks that offer Internet banking services (the ability to manage your bank account online) and/or other banking services.
The national domains that are most commonly exploited by malicious users are registered by Spain and Great Britain. These countries attract the attention of the malicious user as they have the most websites offering online financial management services. Each of the two countries has about 20 banking-related websites, with roughly the same amount of visitors to each, whilst other countries tend to have just a handful of these types of websites registered on their national domains.
But that is no reason to believe that Spain and Great Britain are home to more cybercriminals than any other countries. It’s a known fact that Internet scammers prefer to steal money from the citizens and organizations of other countries as the law enforcement agencies of the country in which the theft took place will surely run into legal obstacles when attempting to bring a malicious user resident in a different country to justice.
The trouble spots
In addition to targeted URLs, we also collected statistics about the Internet addresses that are the sources of Trojan infections and the path of stolen information. After analyzing the data, we put together a map of the locations of these malicious servers.
As you can see, malicious addresses can be found all around the world. But more often than not, malicious users place their servers with European, North American, Russian, and Chinese providers. It’s easy to see why — these countries all have one thing in common: well developed hosting services.
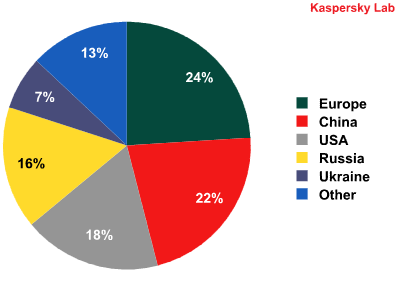
Regions with the heaviest concentrations of ZeuS command centers
It is often impossible to determine where a particular malicious user is located, although that is usually not critical information. The ‘virus writer’ concept does not have any borders or national differences. It could be someone from Sweden, China, or Argentina sitting in a café somewhere in Honolulu registering a website on the .ru domain (such as microsoftwindowsxp.ru, for example) that is actually hosted on a server run by an Italian provider.
Means of protection
What are the simplest ways to protect your computer against the ZeuS Trojan? We will address these below — they are no different than the standard ‘rules of Internet hygiene.’
Never, under any circumstances, click on an unfamiliar link where people you do not know are urging you to do something. As a rule, links to malicious programs are found in IMs and in emails. Malicious users have a solid grasp of basic human psychology and can take advantage of users’ weaknesses or naiveties in order to lure them into visiting their malicious sites. It’s all too common to see URLs disguised as a known, legitimate address simply by swapping a couple of letters around, such as: hxxp://www.vkontkate.ru. This tactic is well known from our recent history, when scammers were offering ‘Abibas’ track suits and ‘Panascanic’ boom boxes. Be attentive and cautious — don’t let them take advantage of you!
Messages might contain a neutral text that looks as though it was sent from an acquaintance, such as “Hi! How was the weekend trip? I have some news for you! Check this out, you won’t believe it: http://rss.lenta-news.ru/subj/vesti.exe”. Pay close attention to the .exe file extension at the end — it indicates a Windows OS executable file. The link won’t take you to a news website, as one might assume at first glance. Instead, it takes you to a malicious website. But executable files aren’t the only files that pose a threat — documents in .pdf format (Adobe Reader) .ppt (Microsoft Power Point), .swf (Adobe Flash) and other formats can also contain a malicious program. These documents have a fairly complex structure and require some sophisticated program computations when launching. What’s more, developers have put a mechanism in place whereby program code can be added (such as javascript, for example). The data selected by a malicious user in these types of documents can cause an error in the program used to open these document formats, which gives malicious code the opportunity to launch on your machine. If you have an antivirus program installed with the latest updates and you regularly update your software, then you are fairly well protected: there is a slight chance that a software program or a document will be identified as malicious, and it will be blocked from launching; or, a vulnerability will be identified by developers, who will develop a patch, which you will receive in time.
In emails, MS Word and other similar types of documents, or on websites, the true address in a link might be hidden from your view. The only thing you will see is a description of the link, which can be anything the author chose in order to attract the attention of potential victims. In these cases, the actual address (although even that can be faked) generally appears in a pop-up bubble that is displayed when the mouse is placed over the link, or displayed in the lower part of the browser window. If the address is not displayed right away in any of these places, try to view the link’s properties. If you aren’t sure where the link goes, the best thing to do is nothing at all — don’t click on it!
Are you comfortable with your operating system? It remembers a lot of things for you, helps you to do things, and provides you with quick access to your data without bombarding you with action confirmation requests or asking for your password every time you want to do something. You feel quite at home with your system and with any programs that runs on it. But if it’s a malicious program, your feeling of security is actually working against you. A cybercriminal is provided with that same quick access to data that you are familiar with, to the detriment of your own security. For example, everything that your browser ‘knows’ can be viewed by the malicious program. Sadly, the more convenient your system is, the more vulnerable it is. Users are strongly advised to refrain from using the ‘remember password?’ feature in web browsers.
We also recommend switching off your browser’s option for running Javascript or launching any programs or files in an iframe/frame window. This, of course, limits your viewing capabilities, but this is where you need to make a choice: convenience and beauty, or security? It’s also a good idea to turn off the Javascript option in Adobe Reader, which opens .pdf files. In any case, you can always turn these options back on for trusted websites and documents.
At present, there are two main methods that provide acceptable security for online payments. The first requires a confirmation of the transaction by telephone, in addition to your login and password, which means there is a link to a telephone number. This complicates nefarious attempts to access your money. In addition to your login and password, a malicious user would also have to get your telephone, which is rather difficult to do over the Internet (or would have to create a copy of your SIM card, which is something straight out of a spy movie). Strange as it may seem, this relatively simple confirmation method is not used by most services. The second method is used primarily by banks and involves the user (i.e. bank client) being issued with a dongle (a USB device) that is plugged into the computer and used to confirm that it is indeed the client attempting to access the bank account. But one should bear in mind that all of these dongles are the same. There was a time when malicious users were able to crack security systems based on USB devices.
We wish you safe surfing! Make the most of the technologies that the Internet has to offer. Be cautious and use common sense, just like you would on the streets. Good luck!





















ZeuS on the Hunt