
Latin America has ceased to be a region that simply receives attacks from across the world.
Since late 2009 it has begun to copy fraudulent business models through which American cybercriminals have begun producing their own criminal resources.
Examples include Brazil, with the web application called TELA (to manage the information stolen from zombie computers); or S.A.P.Z. from Peru, used to propagate malicious code designed to steal bank details. But of course, these are not the only ones. Mexico has also joined this list, with different crimeware developments. Tequila and Mariachi crimeware programs started the trend in this region, back in 2009. But the newest is VOlk-Botnet. The following image shows the main page:
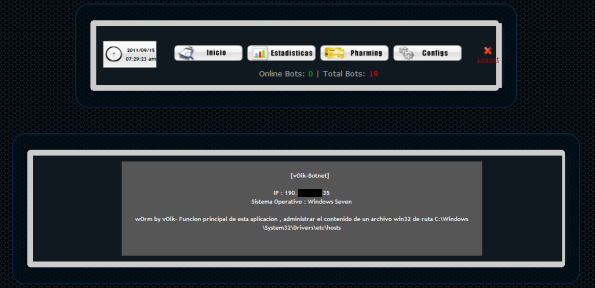
Although the first versions of VOlk-Botnet were released in early 2010, this botnet is now experiencing a level of maturity in the area of crime in Latin America. With similar objectives to the crimeware program S.A.P.Z. from Peru, VOlk-Botnet is designed for local pharming attacks (modifying the hosts file) against banks in Latin America and tries to steal sensitive Internet banking data from unsuspecting users.
In this case, the malicious code,detected by Kaspersky Lab as Backdoor.Win32.VB.oyu, is aimed particularly at users of major banks with branches in Chile and Argentina:
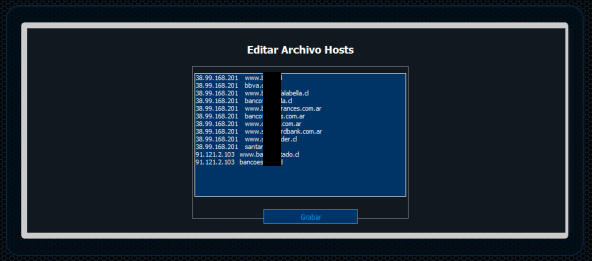
The following picture shows some of the infected computers specifically in Chile:
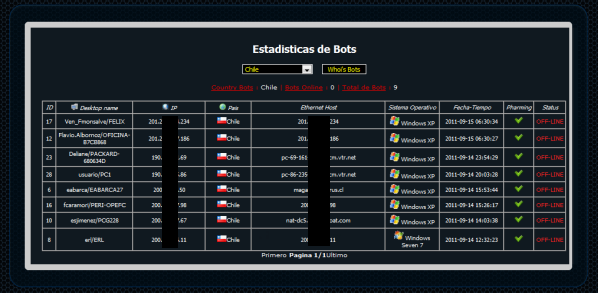
While global strategies of this type share the same fraudulent goals, it is interesting to note that they do not share the same method of attack. On one hand, eastern European crimeware, such as ZeuS (and its derivatives), SpyEye or Carberp, have the ability to inject malicious functions into legitimate operating system processes and browser APIs, to intercept transactions on-the-fly. On the other hand crimeware developers in Latin America have confined themselves to local pharming.
Though less complex, when comparing both methods, local pharming has a very high success rate. This rate is especially high when fused with social engineering. So we recommend keeping your anti-virus security solution active and updated.




















Latin American banks under fire from the Mexican VOlk-Botnet