
Cloud Computing providers offer gigabytes of storage for free, and the cybercriminals use to maintain and spread malware of all the kind. At the same time, many legitimate services are not free, but are still very attractive to cybercrime gangs. In the case of Amazon, Amazon Simple Storage Service (Amazon S3) does the trick.
Despite being a paid service, the cost is not an obstacle for profitable attackers. In fact, my colleague Dmitry Bestuzhev recently told us about the spread of malware exploiting this service to “the cloud”.
The truth is that these cases are not isolated. According to our research, cybercriminals have been running SpyEye activities and from Amazon for the past couple of weeks.
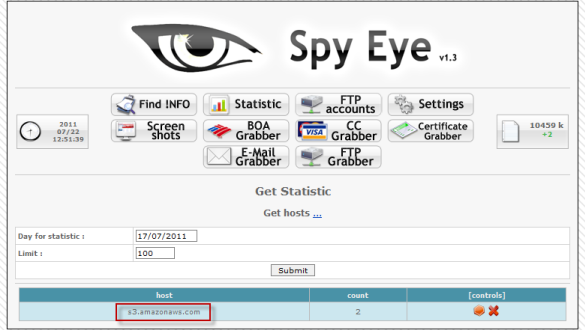
One hurdle for these cybercriminals to abusing Amazon S3 is the creation of an Amazon Web Services (AWS) account. These accounts require a legitimate identity and method of payment, so it is evident that criminals are using stolen data to overcome this challenge.
Data shows that Amazon cloud services were abused heavily this month to spread malware. The following graph shows the domains used for this campaign from the second half of July 2011:
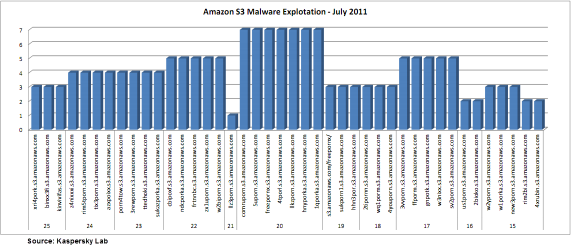
As I mentioned earlier, there are isolated cases, but the tendency to exploit services like cloud storage is in full expansion. This trend clearly represents a critical point for online storage services and requires special treatment.
We have reported these domains to the appropriate security teams. And please note that Amazon provides a contact page for abuse of its services along with an email address.
To solve this critical layer within the storage files model via Cloud Computing, you as a provider can implement our “AllowList Program“, whose participation is voluntary and free. One of the main objectives of this program is to reduce the risk of malware delivered from these services.



















Amazon S3 exploiting through SpyEye