
After the recent emergence of the criminal PiceBOT in Latin America, AlbaBotnet has joined the growing ranks of regional IT crime. It revolves around online pharming, with a view to delivering targeted phishing attacks which steal information from the online accounts of two major Chilean banks.
According to the data we have processed, this campaign is part of a trial stage of this botnet: up to now there has been no monetization of AlbaBotnet. We do know that the author of this threat began testing it in early 2012.
The botnet appears to have a similar structure to its Latin American counterparts. As well as the default automated malware builder, it includes a package which automatically sends emails. Thus, the botmaster can customize infection campaigns through the classic mechanisms of visual social engineering:
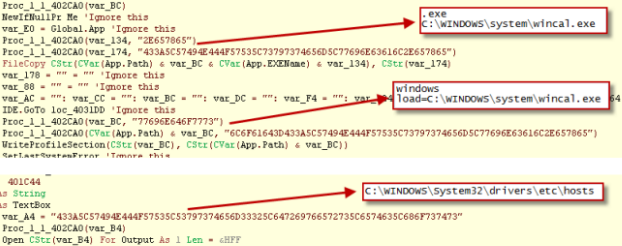
The malware is detected by Kaspersky Lab proactively as Trojan.Win32.VBKrypt.pitu. It uses the same encryption system found in several versions of PiceBOT and vOlk-Botnet. So it-s quite possible that the underlying crypto code is shared between them. The next image is from AlbaBotnet code:
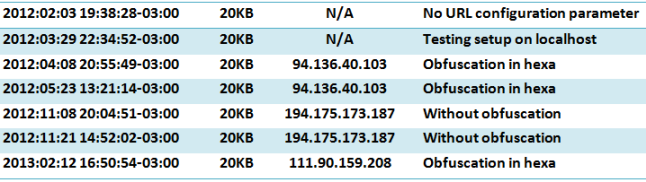
We have so far identified three servers used as C2s operating under the following IP addresses: 111.90.159.208, 94.136.40.103 and 194 175 173 187. The last two servers have probably been violated by the same botmaster. Here you can see some of the versions of the malware used by AlbaBotnet listed in chronological order. The syntax is timestamp + file size + C2 + comment:
We are currently witnessing an increase in the number of home-grown Latin American threats which target users in the region. The situation is evolving and the malware is also developing.
We will continue to investigate the impact of this new threat, noting that the infections are concentrated in South America and currently seem to target only the users of two specific Chilean banking services.
However, it serves as a reminder that all users need to be careful and deploy reliable IT security solutions to minimize the chances of falling victim to malware or online fraud. To enhance the safety of your online financial transactions, Kaspersky Lab has developed the SafeMoney technology, designed to secure access to your online banking services anywhere in the world.



















AlbaBotnet, another new crime wave in Latin American cyberspace