
Following in the wake of the vOlk (Mexico) and S.A.P.Z. (Peru) botnets comes PiceBOT, a newbie to the Latin American cybercrime scene. The cost on the black market is currently around $140.
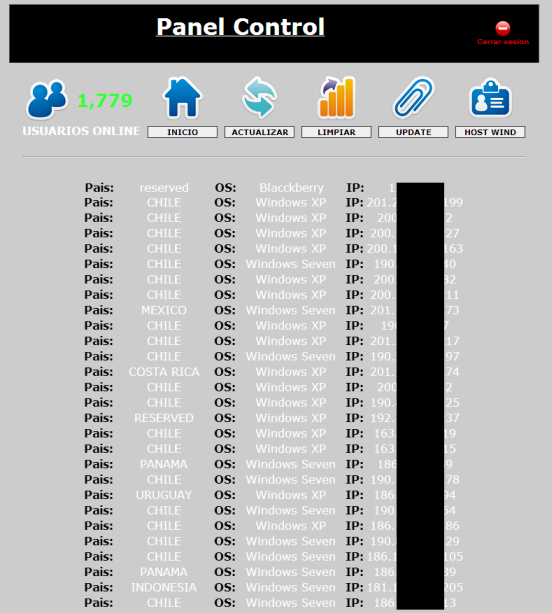
Like other crimeware of its kind, its main purpose is the distribution of malware that steals financial information through local pharming attacks (arbitrary modification of a hosts file). Despite its recent onset (less than a month) it has already been adopted by Latin American cybercriminals to target clients of major banks. So far we have recorded phishing attacks generated and managed through this botnet in Chile, Peru, Panama, Costa Rica, Mexico, Colombia, Uruguay, Venezuela, Ecuador, Nicaragua and Argentina. The following image, obtained from an underground forum, shows some examples:
From a technical point of view, it shares many similarities with the malware propagated by vOlk and S.A.P.Z. We’ll have more details in the coming days. However, it isn’t yet clear which country in Latin America it comes from, though the evidence suggests that the source could be in Guatemala, Mexico or Peru. Another interesting feature that distinguishes it from other LatAm crimeware is its simple authentication process that only needs a single factor: a password to access the administration panel.
In addition, the primary propagation cycle downloads a Trojan dropper that establishes the first clandestine communication with the C2 (Command and Control Panel) botnet sending the parameters of interest to cybercriminal. Another piece of malware is then downloaded from the URL set in “url_des.txt“, and modifies the information in the hosts file via the parameters from “toma.php“.
So far we have detected at least a couple of dozen variants of malware managed through PiceBOT that are detected by Kaspersky Lab generically as Trojan-Dropper.Win32.Injector, and their geographical focus, for now, is in the aforementioned countries.
It’s clear that Latin America has become a very competitive market and very valuable for the region’s cybercriminals as well as those from further afield, due in part to a certain level of naivety among users when it comes to matters of cybercrime as well as a lack of effective legislation.
PiceBOT has, in a short space of time, achieved a significant success rate among the region’s cybercriminal community over crimeware developed in Eastern Europe. Maybe the three most important points that cybercriminals consider when it comes to using local crimeware are: firstly, the low cost compared to European developments (in excess of $ 1,000 in most cases); second, usability limited to phishing as an attack strategy; and thirdly, the return on investment (ROI) is almost immediate, because despite the use of trivial techniques that are enhanced with visual social engineering, the infection rate using these codes is very high, mainly due to a lack of awareness among users.
We’ll keep you up to date on our investigation into this and other similar threats on the Latin American cybercrime scene.




















New crimeware attacks LatAm bank users