
After rumors about the supposed merger between SpyEye and ZeuS, and the public release of the source of the latter, it was logical that the range of possibilities opened up even more for new cybercriminals into the ecosystem of crimeware.
Consistent with this, it was only a matter of time for the emergence of new packages based on ZeuS crimeware, which is now realized. Ice IX Botnet is the first new generation of web applications developed to manage centralized botnets through the HTTP protocol based on leaked ZeuS source code.
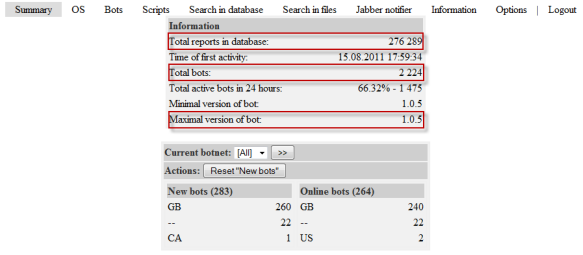
The crimeware of this style is designed to steal banking information. So, it is very clear that we must focus attention on these threats and take into account that this “modified version of ZeuS” has been In-the-Wild since the beginning of year. The following picture is evidence Amazon Elastic Compute Cloud (Amazon EC2) data theft by this browser hooking malware:
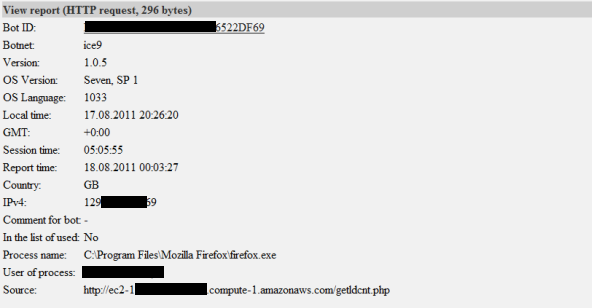
The latest version of Ice IX Botnet is 1.0.5, and it is selling for a very competitive $1800 in the underground markets.
It is clear that from now on, more new crimeware will be based on ZeuS code. New developers, hoping to profit from cybercrime, will attempt to create their own new alternatives based on this source.
At Kaspersky Lab, we investigate the impact of not only this particular threat but also new emerging crimeware. We work to keep you informed!



















Ice IX, the first crimeware based on the leaked ZeuS sources