
Gruezi (Swiss for “hello”) from the Hashdays conference, together with my colleagues Marta Janus and Marco Preuss, held in beautiful Lucerne in Switzerland . The event is hosted by DEFCON Switzerland, which was founded in 2008. Their mission is to educate in IT security skills and know-how. According to them, the best way to show how to prevent systems from becoming unsecure or getting hacked is to introduce and demosntrate current attack techniques. Additional fact: this is the third edition of the conference and it’s sold out for the first time. This already proves the high quality of the event. Honestly, this is easily one the best conferences I attended so far. The quality of both the content and the delivering has been outstanding so far. I can recommend anyone interested in IT security taking part in it.

The conference is much smaller compared to DEFCON in Las Vegas, making the atmosphere way more personal. However, some ideas from its brother event in Nevada got adopted. For example the badge: it’s a laser engraved acrylic plate with a screwed on arduino UNO R3 board. They are also selling additional modules like base kits, matrix LED sets in different sizes, alcohol breath analysis and temperature/humidity checking modules. For people who never played with Arduino, workshops are offered as well, to get the basics and be able to play with it. It’s a nice way of interacting with both hardware and software, making it great fun. The infamous wall of sheep also made its way to Switzerland. You really don’t want to have your login credentials displayed there. Always use VPN or other encrypted ways when you’re using WiFi here!
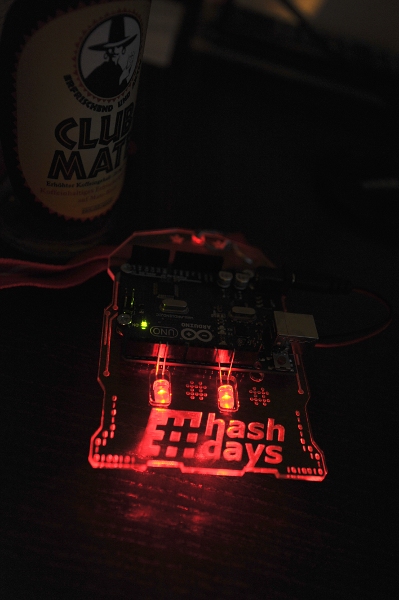
Hashdays’ badge, a beauty! (And yes, they have Club Mate as well!)

This is Marc Hauser giving a talk about his research in IPv6 (in)security
Aside from the talks, there are also contests and side projects. The Arduino badge serves as a platform for two different contests. First it gives a hint for the winning six character password – also a nice tribute to DEFCON in Vegas. Secondly, it’s the core of the badge hacking contest where all participants are called for extending and programming it in a creative and outstanding way.
Now’s the fun part, we’re now off for the party, cheers!






















Hacking in Winter Wonderland