
In partnership with researchers at AlienVault Labs, we ve analysed a series of targeted attacks against Uyghur Mac OS X users which took place during the past months. You can read their analysis here. For our research, please read below.
We previously wrote about targeted attacks against Tibetan activists which used Mac OS X malware. In addition to these, last June we reported about attacks using Mac OS X malware against Uyghur supporters. These later attacks took advantage of social engineering to infect unsuspecting users with Backdoor.OSX.MaControl.b .
During the past months, we ve monitored a series of targeted attacks against Uyghur supporters, most notably against the World Uyghur Congress (WUC).
Several filenames were used in these attacks, including:
|
1 2 3 4 5 6 7 8 9 10 |
Concerns over Uyghur People.doc Hosh Hewer.doc Jenwediki yighingha iltimas qilish Jediwili.doc list.doc Press Release on Commemorat the Day of Mourning.doc The Universal Declaration of Human Rights and the Unrecognized Population Groups.doc Uyghur Political Prisoner.doc 2013-02-04 - Deported Uyghurs.doc Jenwediki yighingha iltimas qilish Jediwili(Behtiyar Omer).doc Kadeer Logistics detail.doc |
Although some of these attacks were observed during 2012, we ve noticed a significant spike in the number of attacks during Jan 2013 and Feb 2013, indicating the attackers are extremely active at the moment.
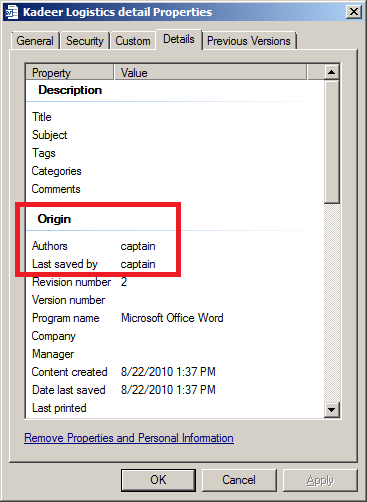
All the attacks use exploits for the CVE-2009-0563 (Microsoft Office) vulnerability — this particular exploit can be easily identified by the author of the underlying document, which is the famous captain that we previously discussed:
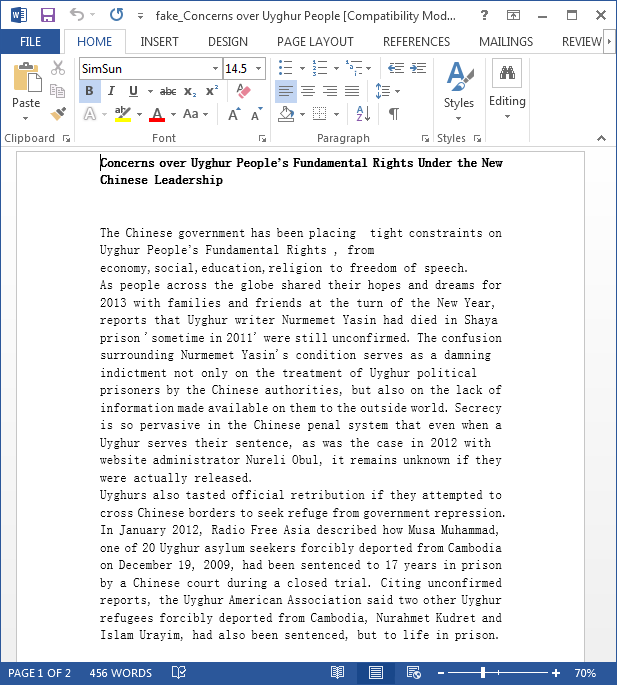
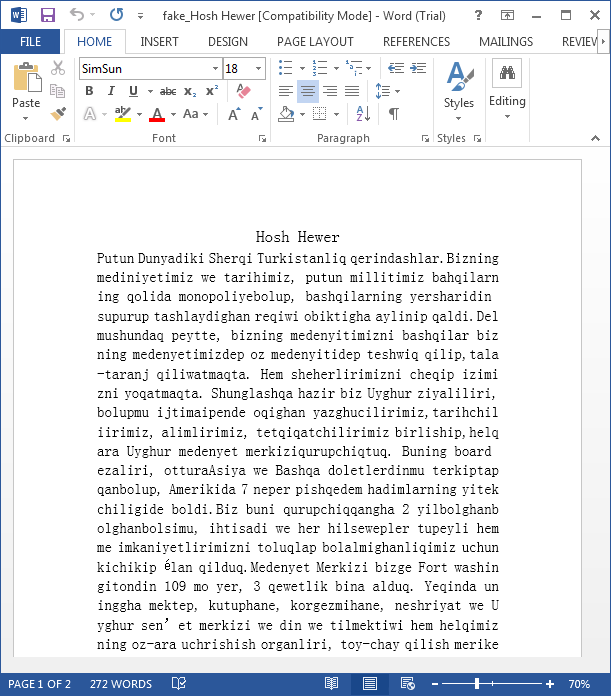
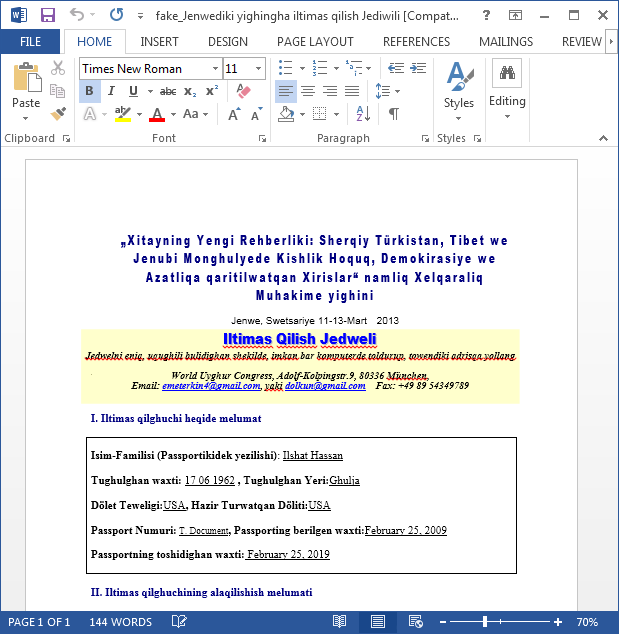
All the documents contain a second, fake document which is shown to the victim when the exploit is run successfully. Some examples include:
Dropped malware
On successful delivery, the exploits drops a backdoor in form of a 101/104 KB Universal Mach-O executable. This small backdoor appears to maintain very little functionality that is unique to this malcode. It sets up a functioning minimal backdoor and a personal contact stealer. The author compiled in an OS X port of the Tiny SHell , an open source UNIX backdoor originally released in 2003, which they setup as a “systm” service on the victim s OS X system. The code includes built-in AES and SHA1 crypto along with hard-coded secret keys and challenge responses. Quite a bit of the original TSH code is simply ripped out to shrink the deliverable, and, in another display of very simple work, the operators decided to go with the secret key “12345678” for its AES secret key. The backdoor also includes hard-coded functionality to pull down an arbitrary executable from the C2s.
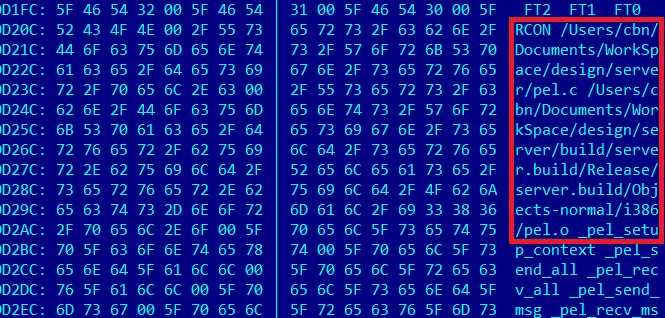
Build path info visible in the 104KB version of the backdoor
Information about the platform where the executable was compiled can be seen inside the larger binary, and it points to /Users/cbn/Documents/WorkSpace/design/server/build/server.build/Release/ . The cbn part is the probably the username of the person who created the backdoor.
In addition to the tshd” code, the attacker included functionality to interact with the victim’s contact lists. Interestingly, the attacker chose to leave a calling card “me” on the victim system.
From one perspective, this makes perfect sense. If the backdoor gets quickly discovered on the victim system, the attacker has a list of trusted contacts to spoof and regain control of the victim system. The attacker may also be attempting to identify connections with higher value targets.
Command and control information
The malware connects to the following C2s:
| Backdoor version | C2 | IP |
|---|---|---|
| 101880 bytes | update.googmail.org | 207.204.245.192 |
| 104140 bytes | apple12.crabdance.com | N/A |
These two are well-known APT domains used for years with a Windows toolset known to spoof MSN and Yahoo! IM communications.
The second domain (apple12.crabdance.com) is currently unavailable, but it previously resolved to 207.204.245.192 and 207.204.231.196. Both servers are hosted at Black Oak Computers Inc. , which is a well known bullet-proof hosting provider that ignores pretty much all shutdown requests.
This Mac OS X backdoor would initiate a connection with the server, and its tshd_put_file function was configured to drop stolen data in the /downloads/ directory located there.
Through passive DNS fingerprinting, we ve observed other domains which pointed to the same IPs or are associated with these campaigns:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
zbing.crabdance.com www.googmail.org bella.googmail.org polat.googmail.org video.googmail.org photo.googmail.org music.googmail.org news.googmail.org kisi.ddns.info mymail.serveuser.com rambler.serveuser.com nicmail.dns04.com webmailactivate.ddns.us www.update.serveusers.com |
Defense recommendations
To summarize our findings, in Jan and Feb 2013 we ve observed a notable increase in the number of targeted attacks against Mac OS X Uyghur users. They all take advantage of the vulnerability known as CVE-2009-0563, which was patched by Microsoft in June 2009.
Here s a number of recommendations on how to protect against such attacks:
| Recommendation | Reason |
|---|---|
| Use a @gmail.com account | Google s Mail (@gmail) service includes additional defense mechanisms against targeted attacks which are not available on other free e-mail providers. These include two factor authentication and warnings against nation state sponsored attacks. |
| Update to the latest version of Microsoft Office | The vulnerability exploited by these attacks was already closed by Microsoft in June 2009. An updated Office will be immune to these attacks. |
| Install an Internet Security Suite | An Internet Security Suite includes an anti-malware, firewall and anti-spam protection. These will protect against most common attacks and make it infinitely harder for the bad guys to break into your computer (PC or Mac OS X). |
| Use Google Chrome to browse the internet | Google s Chrome browser includes a vast array of security enhancements which make it more resilient to malware attacks compared to other browsers. |
| When in doubt, ask a friend | If you notice suspicious looking e-mails, it s always a good idea to ask the sender if he actually sent you that document in the first place. |
With these attacks, we continue to see an expansion of the APT capabilities to attack Mac OS X users. In general, Mac users operate under a false sense of security which comes from the years old mantra that Macs don t get viruses . As previously demonstrated by epidemics such as Flashback, Mac users are definitively not immune against malware. And especially with targeted attacks against Mac users on the increase, we can expect more malware and exploits designed to infect Mac OS X.
* Thanks to my colleagues Kurt Baumgartner and Nicolas Brulez for support with the analysis.





















Cyber Attacks Against Uyghur Mac OS X Users Intensify