
In almost any company the IT security department faces two priority tasks: ensuring that critical systems operate continuously and reducing the risk of attacks on the corporate network. One of the most effective approaches to both these problems is to restrict the privileges of system users.
In terms of IT security, critical systems have two basic properties – integrity and availability – that affect their operational continuity. To protect a corporate network from attacks it is necessary to reduce the attack surface by reducing the number of devices and network services available from outside the corporate network and by protecting the systems and services that require such access (web services, gateways, routers, workstations, etc.). The main vector of attack on a corporate network is the user computers connected to the Internet on that network.
Theoretically, to protect critical systems from unauthorized changes and reduce the possibility of attacks on the corporate network, you should:
- specify those objects (equipment, systems, business applications, valuable documents, etc.) on the corporate network that require protection;
- describe the company’s business processes and use those to help determine the levels of access to the protected objects;
- ensure that each subject (a user or a corporate application) has a unique account;
- limit subjects’ access to objects, i.e. to restrict the rights of the subjects within the business processes;
- ensure that all operations between the subjects and the objects are logged and the logs are stored in a safe place.
In practice, it works more like this:
- All corporate documents are stored centrally in shared folders on one of the servers of the company (for example, on the Document Controller server)
- access to critical systems is denied to everybody but administrators – any administrator – can log into the system remotely to quickly repair any failure
- Sometimes administrators use a “shared” account
- All employees have limited privileges as a ‘standard user’ but on request anyone can get local administrator rights.
Technically, it is much easier to protect critical systems than workstations: changes in business processes are rare, regulations vary little and can be drawn up to account for even the smallest details. By contrast the users’ work environment is chaotic, their processes change rapidly and the protection requirements change along with them. In addition, many users are suspicious of any restrictions, even when there is no impact on workflow. Therefore, the traditional protection of users is based on the principle ‘it is better to miss malicious software than to block something really important’.
Last year, Avecto conducted a study called “2013 Microsoft Vulnerabilities Study: Mitigating Risk by Removing User Privileges” and concluded that “by removing local administrator rights it is possible to reduce the risk of exploitation of 92% of critical vulnerabilities in Microsoft software”. The conclusion seems logical but it should be noted that Avecto did not test vulnerabilities; it only analyzed data from the Microsoft Vulnerability Bulletin 2013. Nevertheless, it is clear that malicious software running without administrator rights cannot install a driver, create/modify files in protected directories (% systemdrive%,% windir%,% programfiles%, etc.), change system configurations (including writing to the HKLM registry hive) and most importantly – cannot use privileged API functions.
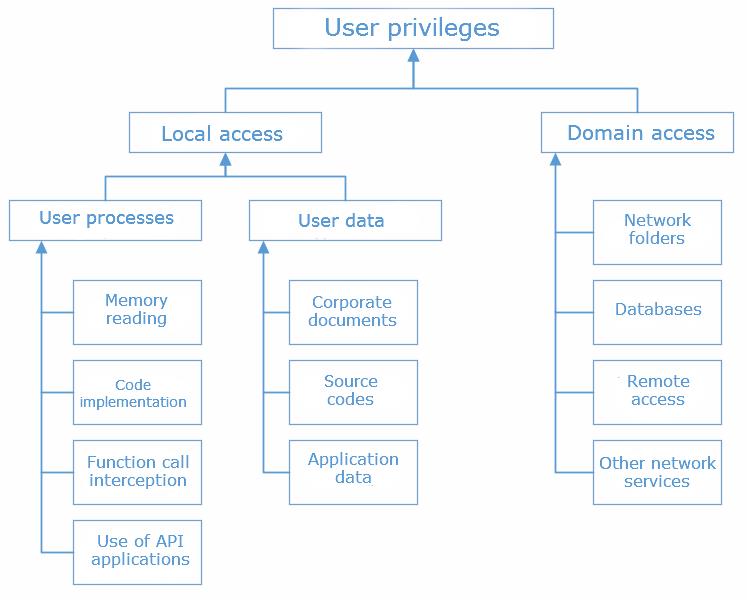
In reality, though, the lack of administrator rights is not a serious obstacle for either malicious software or a hacker penetrating into the corporate network. Firstly, any system has dozens of vulnerabilities that open up the necessary rights up to kernel level privileges. Secondly, there are threats which only require standard user privileges to be implemented. The diagram below shows possible attack vectors that do not require any administrator rights. Let’s have a closer look at them.
Local attacks
With only standard user privileges, the attacker gets full access to the memory of all processes running under the user account. This is enough to integrate malicious code into processes in order to remotely control the system (backdoor), to intercept keystrokes (keylogger), to modify the content in the browser, etc.
Since most antivirus programs can control attempts to implement unknown code in the processes, attackers often use more secretive methods. Thus, an alternative method applied to implement a backdoor or a keylogger in the browser process is to use plugins and extensions. Standard user privileges are enough to download a plugin, and that code can do almost everything a fully-featured Trojan is capable of. That includes remotely controlling the web browser, logging data entries in browser traffic, interacting with web services and modifying page content (phishing).
Fraudsters are also interested in standard office applications (such as email and IM-clients) which can be used to attack other network users (including phishing and social engineering). Scammers can access programs like Outlook, The Bat, Lync, Skype, etc. via API and local services of such applications as well as by injecting code into the relevant processes.
Of course it’s not just applications that are of value to fraudsters; the data stored on the PC is also a potential goldmine. In addition to corporate documents, attackers often look for different application files containing passwords, encrypted data, digital keys (SSH, PGP), etc. If the user’s computer has the source code, attackers could try to implement their code into it.
Domain attacks
Since the accounts of most corporate users are domain accounts, the domain authentication mechanisms (Windows Authentication) provide the user with access to various network services on a corporate network. This access is often provided automatically without any additional verification of the username and password. As a result, if the infected user has access to the corporate database, attackers can easily take advantage of it.
Domain authorization also allows attackers to access all network folders and disks available to the user, share internal resources via the intranet and sometimes evenaccess other workstations on the same network segment.
In addition to network folders and databases, the corporate network often includes various network services such as remote access, FTP, SSH, TFS, GIT, SVN, etc. Even if dedicated non-domain accounts are used to access these services, attackers can easily utilize them while the user is working on his computer (i.e. during an active session).
Protection
It is almost impossible to provide high level of protection for workstations by denying users administrative rights. Installing antivirus software on a workstation will increase its security but won’t solve all problems. To achieve high security levels, Application Control technology should consist of three key elements:
- Default Deny, which only allows the installation and running of software that has been approved by the administrator. In this case, the administrator does not have to put each individual application (hash) on the list of trusted software. There is a wide variety of generic tools available to enable dynamic allowlisting of all software signed by an approved certificate, created by an approved developer, obtained from a trusted source or contained in the Allowlisting database of a security software provider.
- Application Control that can restrict the work of trusted applications according to their functions. For example, for normal operation the browser should be able to create network connections but it does not need to read/write other processes in the memory, connect to online databases or store files on the network.
- Update management that ensures all software on workstations is updated promptly, reducing the risk of infection via update mechanisms.
In addition, specific products which feature Application Control can provide a range of useful functions based on this technology: inventory, control over software installed on the network, event logs (which will be useful in the case of incident investigation), etc.
On the one hand, the combination of technologies can provide users with everything they need for work and even for entertainment and is flexible enough to deal with changing requirements. On the other hand, the chances of an attacker gaining access to the protected system are extremely limited. No doubt, this is the best balance between flexibility and security in protecting a corporate network.




















Breaches in corporate network protection: access control