
Apple has released MacOS X 10.6.7 with several bugfixes and security-patches. This patch bundle also includes a silent update to Apple‘s built-in Xprotect anti-virus functionality.
Xprotect
With the release of Snow Leopard (Mac OS X 10.6) Apple introduced a basic antivirus protection called „XProtect“. It scans and detect threats when files are downloaded through Safari, Mail, iChat, Firefox and a few more and afterwards executed. The Signature-List is updated via Apples Software Update.
Till now Xprotects database contained signatures for three well-known threats:
– OSX.RSPlug.A: changes local DNS-entries, came through fake video-codecs
– OSX.Iservice: attacks websites (DDoS), came bundled with pirated applications
– OSX.HellRTS: known as HellRaiser, tool which gives the attacker full access ofver the victims system. Version 4.2 public available, version 4.4 sold for 15$ by the creator in underground forums.
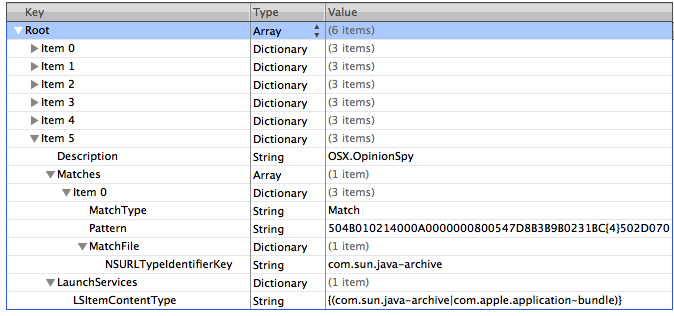
New update
The updated signature now includes definitions for “OSX.OpinionSpy“.
This Trojan came bundled with screensavers and applications hosted on popular download websites for Macs mid of 2010. It is known as Opinion Spy and Premier Opinion. The main aim of the malware is to collect personal data which is sent to various servers. The Trojan runs as root, which means it’s capable of doing „anything“ on your computer.
When an installer (bundled with OpinionSpy) is executed, it asks for the root-password which is quite common for installations. The user grants full system access to the Trojan by this. OpinionSpy also injects code into Safari, Firefox and iChat in order to collect more personal data.
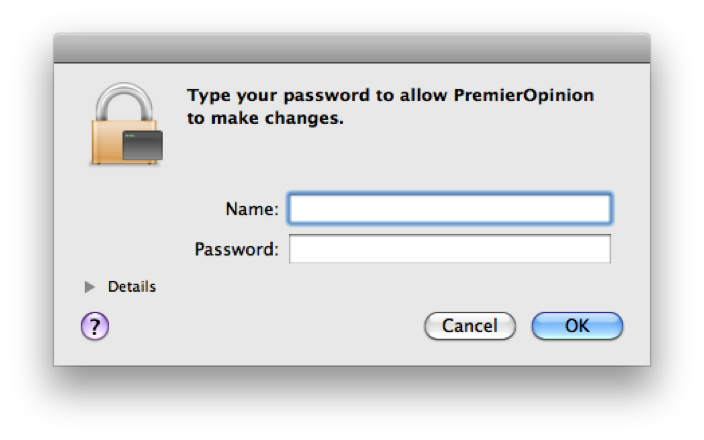
Kaspersky has already been detecting this threat as „Trojan.OSX.Spynion.a“ since 2. June 2010.
We have received 13 user reports through KSN this year, mainly from india.
While Apples signature-list keeps growing, Mac users should pay more and more attention to security and malware.




















Apple’s silent updates