
By now most people have heard of Rogue Anti-Virus. You might have heard it referred to as Scareware, Fraudware, Fake Anti-Virus or rogue anti-virus. No matter what you call it, the threat is the same. It’s a program that imitates legitimate anti-virus programs with the sole purpose of scaring unwitting users into paying to clean viruses on their computers that don’t exist. This isn’t anything new and in the United States it’s a big issue. Fueled by large financial gain, the creators of these programs have made rogue AV into a lucrative business by pumping out programs faster than most in the AV industry can keep up.
Now we are seeing a new breed of Fake Anti-Virus. This is FAKE Fake Anti-Virus! In my research I have seen Fake Anti-Virus programs really develop into professional looking programs. The idea is to look as genuine as possible. This improves the chance that unknowing computer users will fall victim to the scam. Lately we have been seeing script kiddies writing fake viruses and fake Fake Anti-Virus programs. The idea behind the script kiddies creating these programs is essentially to show their skills or attempt to show off their newly found skills. Now these programs are really amateur on most levels. The user interface looks like they have been copied and pasted and there are typos throughout the programs. Not to mention some of the methods they use to achieve their goals are basic.
Take this program for example:
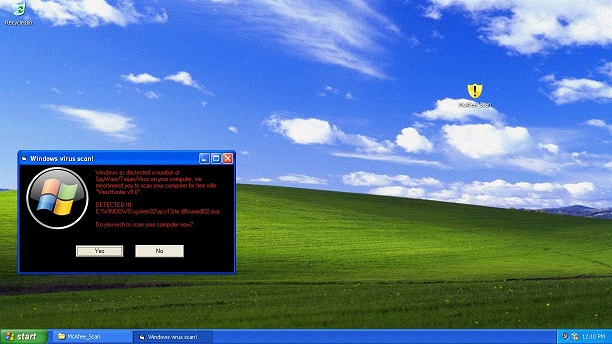
As you can immediately see there is a typo, and after clicking on “No” the next screen shows that the virus has started and your computer will shut down in 1 minute.
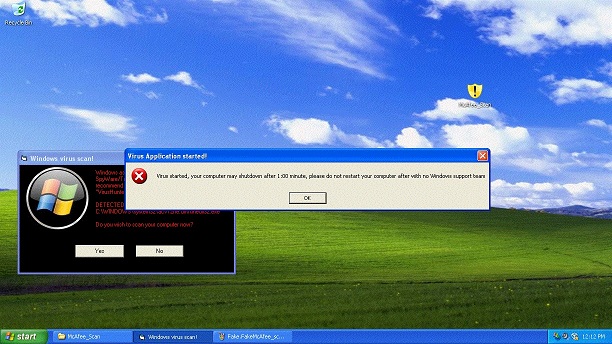
Next, it tells you to contact the virus scan support team and provides a supposed windows email address and an out of service phone number.
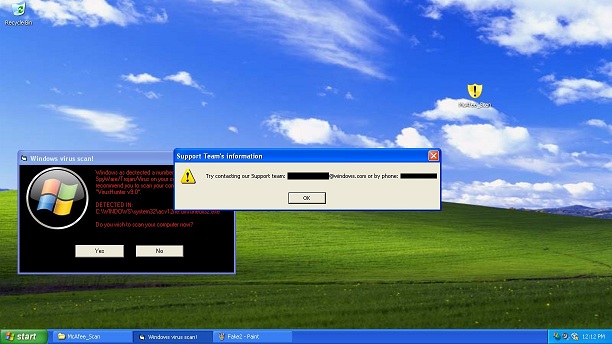
With this specific program if you click “Yes” there won’t be any scan, in fact the window will close and the process will terminate.
As I mentioned the methods are basic. In the above example the method they use to turn off your computer is a basic command line argument.
Now with this specific program there is no real threat, however, that doesn’t mean that one isn’t on the way. This program also wasn’t designed to infect people but rather to trick users and show off their skills. With that said this is only one of many that we have been finding. Grinler, a forum moderator over at bleeping computer, came across one a few weeks ago and wrote a guide for it. Since then, it has had 6000 views. This shows these fake Fake AV programs are increasing in volume, it also means there is one more thing we all need to be conscious about.



















Amateur Rogue