
The most popular uses of cloud services include: storing image scans of passports and other personal documents; synchronization of password, contact list, and email/message databases; creating sites; storing versions of source codes, etc. When cloud-based data storage service Dropbox announced a patched vulnerability in its link generator, it once again sparked online discussions about how important it is to encrypt confidential data before uploading it to an online storage, even a private one. Well, File encryption (FLE) does indeed protect confidential information stored in the cloud, even if there are vulnerabilities in controlling access to user documents with certain cloud storage services.
It’s tempting to think that you can secure yourself against all possible risks by encrypting your data before you upload it to a cloud storage service, or by foregoing cloud services altogether. But is that really true? As it turns out, no, it isn’t.
The Internet is full of recommendations on how to “effectively use cloud-based storage services” including advice on how to remotely control a PC, monitor your computer while you are away, manage your torrent downloads, and many other things. In other words, users create all types of loopholes all by themselves. These loopholes can then be easily exploited by a Trojan, a worm, not to mention a cybercriminal, especially in targeted attacks.
So we asked ourselves: how likely is it that a corporate network can be infected via a cloud service?
At the Black Hat 2013 conference, Jacob Williams, Chief Scientist at CSRgroup Computer Security Consultants, gave a presentation on using Dropbox to penetrate a corporate network. While conducting a trial penetration test (pen test), Jacob used the Dropbox thin client installed on a laptop located outside of a corporate network to spread malware to devices within that network.
Jacob first used phishing to infect an employee’s computer, then embedded malicious scripts into documents stored in the laptop’s cloud-hosted folder. Dropbox automatically updated (synchronized) the infected documents on all the devices attached to the user’s account. Dropbox is not unique in this respect: all applications providing access to popular cloud file services have an automatic synchronization feature, including Onedrive (aka Skydrive), Google Disk, Yandex Disk, etc.
When the user opened the infected document on a workstation located within the corporate network, the malicious scripts embedded in the document installed the backdoor DropSmack on that workstation – it was specifically crafted by Jacob for this pen test. As its name suggests, DropSmack’s main feature is that it uses the Dropbox cloud file storage service as a channel to manage the backdoor and leak corporate documents through the corporate firewall.
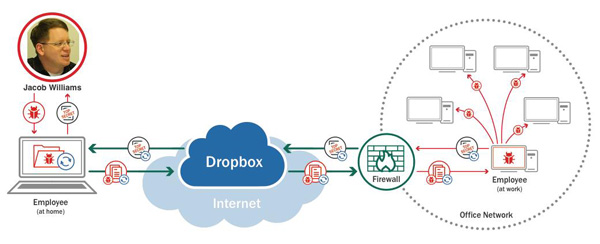
Flow chart of Jacob Williams’s experiment
In the pen test, Jacob used a stunningly simple method to penetrate the corporate network – it is an obvious loophole!
We also decided to check if cybercriminals are using Dropbox, OneDrive, Yandex Disk or Google Disk to spread malware for real. We collected information from KSN about instances of malware detected in cloud-based folders belonging to Kaspersky Lab product users, and found out infections like these were detected for very few users: in May this year, only 8,700 people encountered an infection in their cloud-based folder. Among Kaspersky Lab’s home product users, such instances account for only 0.42% of all malware detection cases, and 0.24% for corporate product users.
We should point out one important detail: if a piece of malware is uploaded from one device, all clients connected to the infected account will download it to their devices, and they will do so via HTTPS. Even if a security solution detects the malware in the synchronization folder and deletes it, the cloud client will keep downloading it from the cloud in an endless loop.
According to the data we collected, some 30% of malware detected in cloud folders on home computers had penetrated to these computers via synchronization mechanisms. For corporate users this number reaches 50%. Thus, the infection mechanism demonstrated by Jacob Williams in his demonstration malware, does cause infections in real life. Fortunately, we have not (yet) detected targeted attacks launched using cloud-based data storage services.
If we look into the malware we detected in the cloud folders on users’ computers, files for Win32, MSIL, VBS, PHP, JS, Excel, Word and Java dominate. It should be noted that there is a small difference between corporate and home users: for corporate users, infected MS Office files occur more often, while home users also face unique threats on their lists in the form of malicious Android applications.
TOP 10 verdicts:
|
|
Consumer | Corporate |
| 1 | Email-Worm.Win32.Runouce.b | Email-Worm.Win32.Brontok.dam.a |
| 2 | Email-Worm.Win32.Brontok.q | Virus.Win32.Sality.gen |
| 3 | not-a-virus:AdWare.Win32.RivalGame.kr | Virus.Win32.Tenga.a |
| 4 | Virus.Win32.Nimnul.a | Trojan-Dropper.VBS.Agent.bp |
| 5 | Trojan-Clicker.HTML.IFrame.aga | Trojan.Win32.Agent.ada |
| 6 | Exploit.Win32.CVE-2010-2568.gen | Trojan.Win32.MicroFake.ba |
| 7 | Virus.Win32.Sality.gen | Exploit.Win32.CVE-2010-2568.gen |
| 8 | Worm.Win32.AutoRun.dtbv | Worm.Win32.AutoRun.dtbv |
| 9 | Trojan-Dropper.VBS.Agent.bp | Trojan.Win32.Qhost.afes |
| 10 | Trojan.Win32.Genome.vqzz | Virus.Win32.Nimnul.a |
More often than not, virus writers use cloud storage as a place to host their malware rather than a platform to spread them. During the research, we did not encounter a single worm or backdoor (except DropSmack) specifically targeting cloud-based file storages. Naturally, these services try to counter malware which takes up storage room in the cloud. In addition hosting malware affects the service’s reputation, although cloud services are not formally responsible for what files their clients upload to the storage. Regular scans of all files contained in the cloud will obviously require a lot of resources that the services would rather use to store data.
As a result of this research, we concluded that there is a relatively low risk of a corporate network being infected via cloud storage: over a period of a year, just 1 out of 1,000 corporate users using cloud services risks infection. It should be remembered, however, that in some cases even a single infected computer in a corporate network can lead to substantial damage.
Here are some measures that can be used to protect corporate networks:
- Tighten up Firewall/IDS security settings, block access to popular online storage services. The big disadvantage this approach has is that it requires constant and close monitoring of new denylist candidates as they emerge online.
- Install a multi-purpose Security Suite. It must incorporate a heuristic and behavior-based antivirus, access restriction features (HIPS), a tool to control the functioning of the operating system (System Watcher or Hypervisor), and a tool to prevent exploitation of vulnerabilities, etc. Once installed, the product must be carefully configured.
- Remember that even the most sophisticated Security Suite can miss an APT attack. Therefore, attention should be paid to Application Control (it should be configured at Default deny). This is perhaps one of the most reliable tools that will block any unknown software, including malware spread during a targeted attack. The most difficult task arising while deploying Application Control is to configure appropriate rules so that all permitted applications can be launched and updated without problems. To this end, the manufacturers of products which include the Application Control feature have developed dedicated tools: software updates via trusted update programs, preset software allowlists including all possible system and user files, access to huge cloud services and information databases about the entire diversity of allowlisted software.
- In special cases, Application control should be used to restrict the use of cloud clients within the corporate network. Only trusted employees should be allowed to launch the applications with which to synchronize cloud folders.
As for networks with the most rigorous security requirements, such as those managing power plant operations and water supplies, which guard state secrets or control defense facilities – for all of these we thoroughly recommend not using cloud-based file storage services at all.




















Cloud Services: Holes in Corporate Network Security