
Part 1 – Phishing and malware
In less than a month 32 national teams and thousands of football fans will descend on Brazil for the 2014 FIFA World Cup. For a month the whole world will be watching arguably the biggest sporting event on the planet. Right now the players and coaches are fine-tuning their tactics, game plans and strategies in order to outwit their opponents. And so are the cybercriminals.
A few months ago we described some attacks that were exploiting the World Cup theme. They includedfraudulent domains selling fake tickets, fake giveaways, and several phishing and malware campaignsthat targeted users’ credit cards. The cyberattacks have continued as the tournament approaches. In this weekly series of four blogposts my colleague Dmitry Bestuzhev and I will provide details of the latest attacks, and offer tips to travelers and users on how to remain secure while visiting Brazil or searching online for match-related videos or results.
In this first part we’ll look at some very professional phishing and malware attacks that use digitally-signed malware, a breached customer database used for online ticket sales, SSL-certified phishing domains and a lot of social engineering. All the attacks had the same goal: to infect your machine and steal your money.
Legit or not?
How can you spot a phishing domain? Well, the phisher will usually compromise a legitimate site and host their page there, e.g., anotherwebsite.com/paypal_phish_page. But what if the phishers are real professionals? They can prepare an attack in such a way that ordinary users will find it very difficult to tell if a page is legit or not, greatly increasing the number of victims.
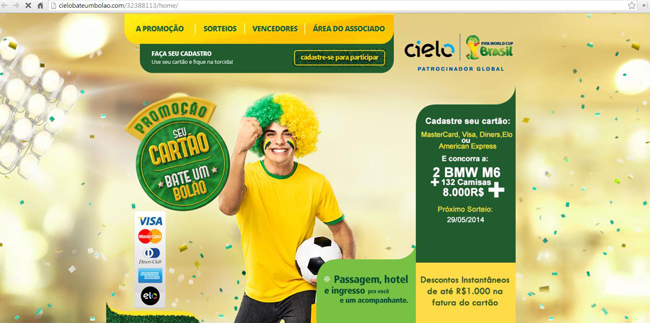
And that’s exactly what Brazilian phishers are now doing – registering domains with names of well-known local brands, usually credit card companies, banks, online stores, etc. All the phishing sites have obviously been designed by a professional, such as this one using the name of Cielo, a representative of Visa in Brazil:
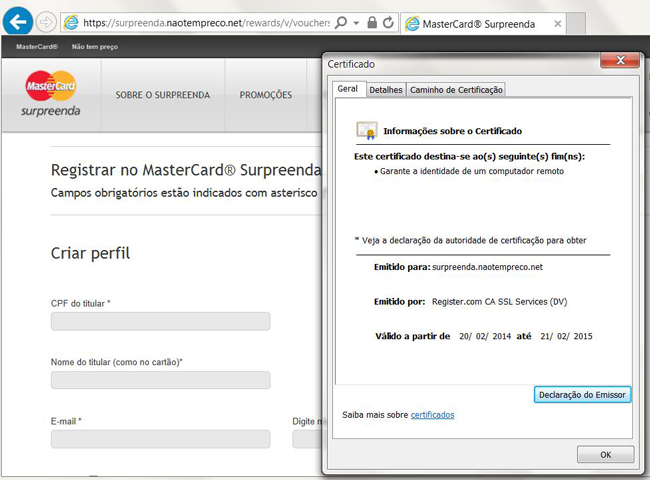
They also used the names of other credit card brands, such as Mastercard:
Here’s another one using the image of Brazilian TV host Rodrigo Faro:
All the phishing domains had a very professional look and feel:
In Brazil alone, we’re detecting and blocking on average about 50-60 domains like this per day.
But the phishers have not stopped there: they have also registered domains and started buying SSL certificates from Certification Authorities such as Comodo, EssentialSSL, Starfield, Register.com and others. This results in phishing domains with a ‘verified’ SSL certificate:
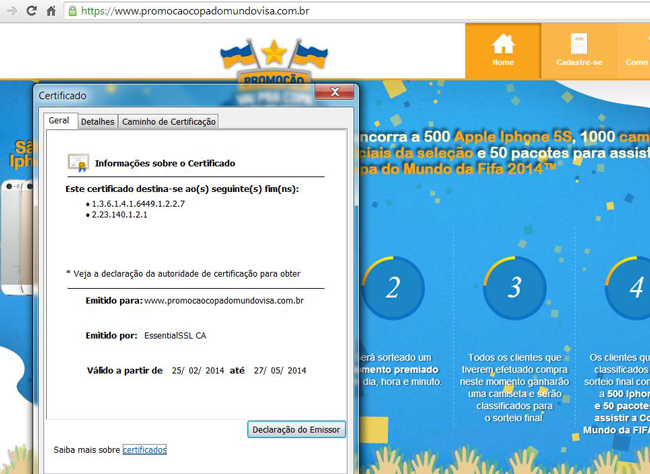
Here’s another site using the Visa name and its SSL certification:
How can an ordinary user recognize such domains? Well, it’s not that easy. That’s why our anti-phishingdetection component is highly proactive, blocking these domains in advance before the bad guys activate the phishing content.
Why are these CAs issuing SSL certificates to phishers? To be honest, we don’t know. What is certain is that they need to implement a better verification process so they stop helping cybercriminals steal money.
The phishers also prepared fraudulent pages in mobile format, so they can steal data from users even if they click the link on their smartphone:
Digitally-signed, but malicious
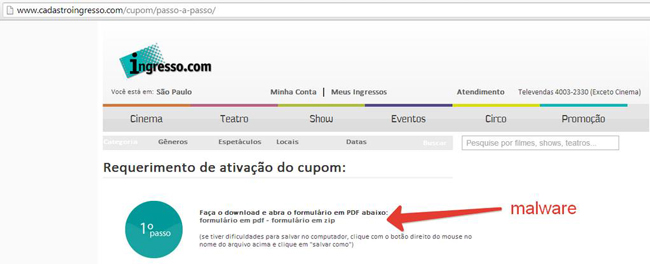
Brazilian cybercriminals are taking advantage of the fact that it so easy to buy SSL certificates – they decided to prepare malware campaigns distributing digitally-signed malware. The files are distributed in messages like the one below:

“Congrats, you have won a ticket to a World Cup match”
To “claim” the ticket the user is asked to print it. The link points to a digitally-signed Brazilian Trojan banker:
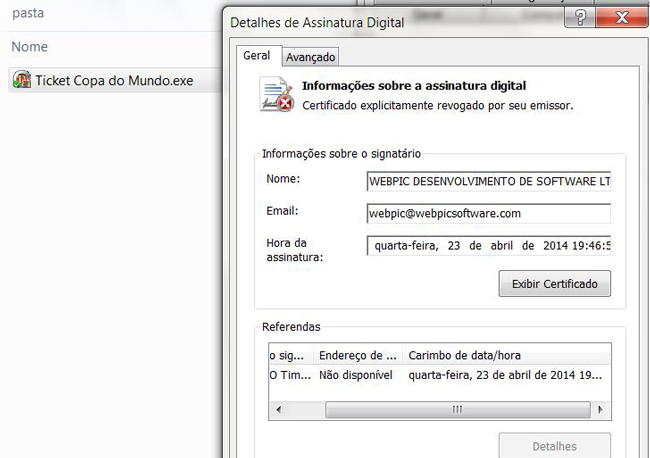
Trojan-Banker.Win32.Banker.bplh
Breached database, personalized attack
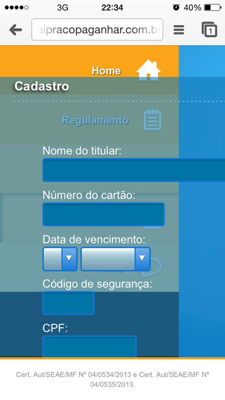
What about a personalized email supposedly sent by a well-known online ticket sales system informing you that you’ve won a ticket to a World Cup match? To make it look legitimate the message includes personal data such as your full name, date of birth, mother’s name and full postal address. Sound’s legit, right? No.
Well that’s exactly what Brazilian cybercriminals have done, apparently using information from a breached customer database of unknown origin:

“We want to inform you won a ticket”
The message pointed to this website. To activate the “gift” the user needs to download a file that turns out to be a Trojan banker:
Brazilian cybercriminals aren’t the only ones exploiting the theme of the World Cup – these attacks are appearing elsewhere in different languages and with different targets.
If you are planning to travel to Brazil for the World Cup or following it online, be secure – don’t trust any messages you receive, and double-check before clicking links.
In our next blogpost we’ll tell you how to protect your credit card when buying things in Brazil, the land of the ChupaCabra malware.
























World Cup Brazil 2014: Don’t score an own goal