
You’ve probably already heard about the ‘Chupa Cabra’, literally a “goat sucker”. It’s a mythical beast rumored to inhabit parts of the Americas. In recent times it has been allegedly spotted in Puerto Rico (where it was first reported), Mexico and the United States, especially in the latter’s Latin American communities. The name Chupa Cabra has also been adopted by Brazilian carders to name skimmer devices, installed on ATMs. They use this name because the Chupa Cabra will “suck” the information from the victim’s credit card.
The Brazilian media regularly shows videos of bad guys installing their Chupa Cabra onto an ATM. Some of them are unlucky, or incompetent, and get picked up on security cameras and caught by the cops.
That’s what makes installing an ATM skimmer a risky business – and that’s why Brazilian carders have joined forces with local coders to develop an easier, more secure way to steal and clone credit card information. From this unholy alliance, the ‘Chupa Cabra’ malware was born.
The idea behind the malware is simple: rather than risk getting caught red-handed with an ATM skimmer, the bad guys are developing and installing their malicious code on Windows PCs. They are looking to intercept communications from PIN Pads. These pads are the kind of things you use at supermarkets, gas stations, anywhere that takes card payments.
This malware was first detected in Brazil late in December 2010 as Trojan-Spy.Win32.SPSniffer and has 4 variants (A, B, C and D) was negotiated between Brazilian cybercriminals for 5 thousand dollars . Generally these Trojans are highly specialized and distributed to specific targets. And these attacks are spreading – we already know of confirmed cases in the US, and probably elsewhere in the world.
Of course, PIN pads are protected. They are equipped with hardware and security features to ensure that security keys are erased if someone tries to tamper with the device. In fact, the PIN is encrypted immediately on entry using a variety of encryption schemes and symmetric keys. Most often this is a triple DES encoder, making it hard to crack the PIN.
But there’s a problem: these devices are always connected to a computer via a USB or serial port which communicates with the EFT (Electronic Funds Transfer) software. Older and outdated PIN pad devices, still used in Brazil, are vulnerable at this point.
The Track 1 data and the public data present in your card’s chip are not encrypted in the hardware of these old devices. That generally includes your card number, expiration date, service code and discretionary data such as the CVV – in short, almost everything a crook needs to start spending your money. As this data isn’t encrypted, it goes to the PC in plain-text mode. Capturing this data is enough to clone your credit card.
The malware installs a simple USB or serial port sniffer driver, generally adapted from commercial software such as Eltima and TVicPort, sniffing all the data transmitted between the PIN pad and the PC. The first versions of the Chupa Cabra malware also installed a DLL that monitors and steals network traffic from all devices connected to any COM port.
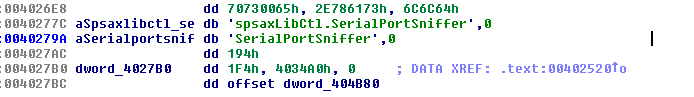
The newest versions use the TVicCommSpy driver to capture USB traffic, with the same purpose.
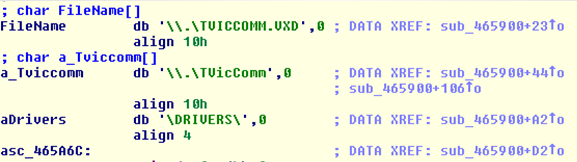
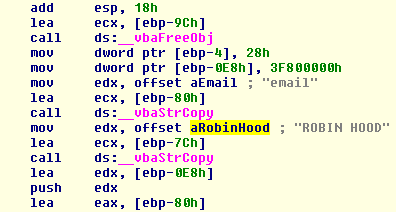
Additionally the malicious DLL intercepts all keystrokes on the keyboard (keylogger). All the Track 1 data stolen is saved to a file that contains all the intercepted data, along with information about the victim’s computer, and sends it to the criminal, generally via e-mail.
To ensure the data is sent to the bad guys in a “secure” way, the malware has a crypto symmetric system with an interesting Unicode key name…
Once the problem became evident, credit card companies in Brazil began updating the firmware of these old PIN pad devices for new ones which are not vulnerable to the threat.
This is the true story behind Trojan-Spy.Win32.SPSniffer, the Chupa Cabra malware developed in a “joint-venture” between Brazilian carders and coders. But a joint effort from Kaspersky Lab and a leading credit card company managed to detect and defeat this malicious beast in Brazil.
We are still working on this, and are keen to cooperate with credit card companies to obtain samples and other data that will help our products to detect and remove these threats.




















The ‘Chupa Cabra’ malware: attacks on payment devices