
Brazilian cybercriminals are clearly setting their sights on users of mobile banking, with a huge rise in incidents registered in the country over the last two years. In order to carry out these attacks they are using SMiShing (phishing via SMS) and registering new mobile phish domains created especially for this purpose.
In 2015, mobile banking usage in Brazil reached 11.2 billion transactions, an increase of 138% compared to the 4.7 billion transactions registered in 2014. Mobile banking is now the second most popular channel for accessing a bank account in the country – there are more than 33 million active accounts, according to the Brazilian Federation of Banks. Such numbers and the possibility of cheaply sending SMS messages are very attractive to cybercriminals, who are investing their time and effort to create new attacks.
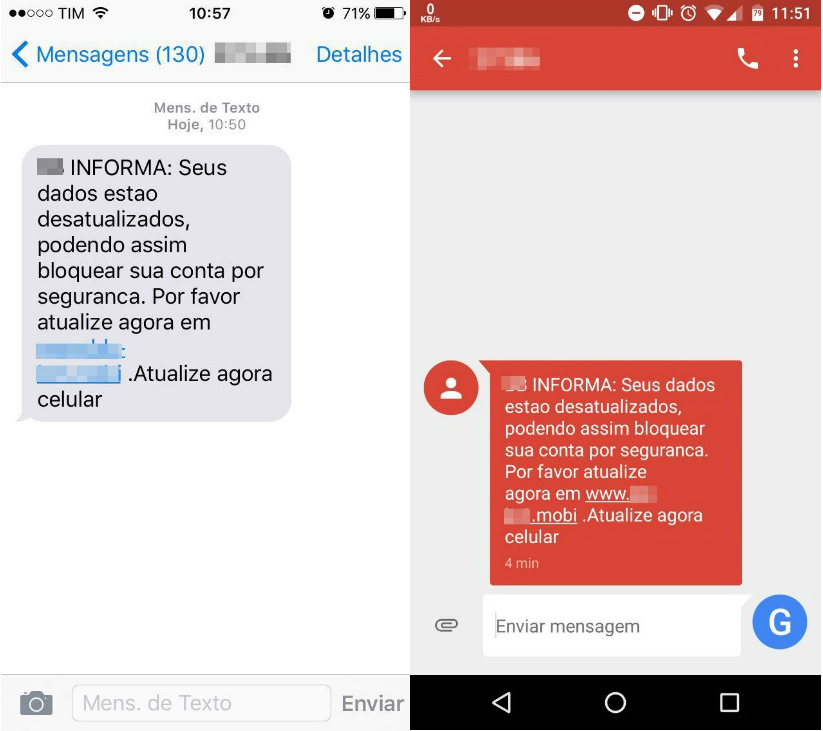
Getting started doesn’t require that much money or preparation: first they need to register a domain (usually a .mobi domain), prepare a phishing page in mobile format, hire a bulk SMS service (as cheap as 2 cents per message sent, and generally paid for with a cloned credit card) and voilá! Getting the telephone numbers of the victims isn’t a problem either: huge databases of mobile numbers can easily be purchased on the Brazilian underground, or can be captured in attacks using WhatsApp as bait. The SMiShing messages inform recipients about a credit card or a bank account that has supposedly been blocked, and always include a link:
“Your data is outdated, your account may be blocked. Please update at <phish URL>” – an SMiShing message sent by phishers
Why target users of mobile banking? Because it’s easier to hack a bank account when accessed from a mobile terminal instead of a desktop. We’ve listed some of the reasons for that below:
- No protection: most smartphone users in Brazil still don’t use a dedicated AV on their phones. A survey performed by B2B International in 2015 showed only 56% of smartphone owners around the world do so.
- No security plugins: unlike desktops, most banks still don’t require the installation of a security plugin on user devices, despite most banks offering dedicated access via their mobile apps. Furthermore, fake mobile banking apps from Brazilian banks have also been found in the Play Store. When a criminal decides to phish a mobile banking user, it’s more effective if the attack is compatible with any mobile browser.
- Simple authentication: most Brazilian banks use very simple authentication on mobile devices, usually just asking for the account number and a six-digit password.
- Common SMS usage: it’s very common for banks in Brazil to send notifications via SMS. When you buy something or withdraw money for your account, you’ll receive an SMS confirming the operation. This approach has allowed Brazilian banks to decrease the number of fraud cases, in particular, this is because customers are aware of any fraud involving their credit cards or bank accounts as soon as it starts. Confusing a SMiShing message with a legit SMS from your bank is very easy.
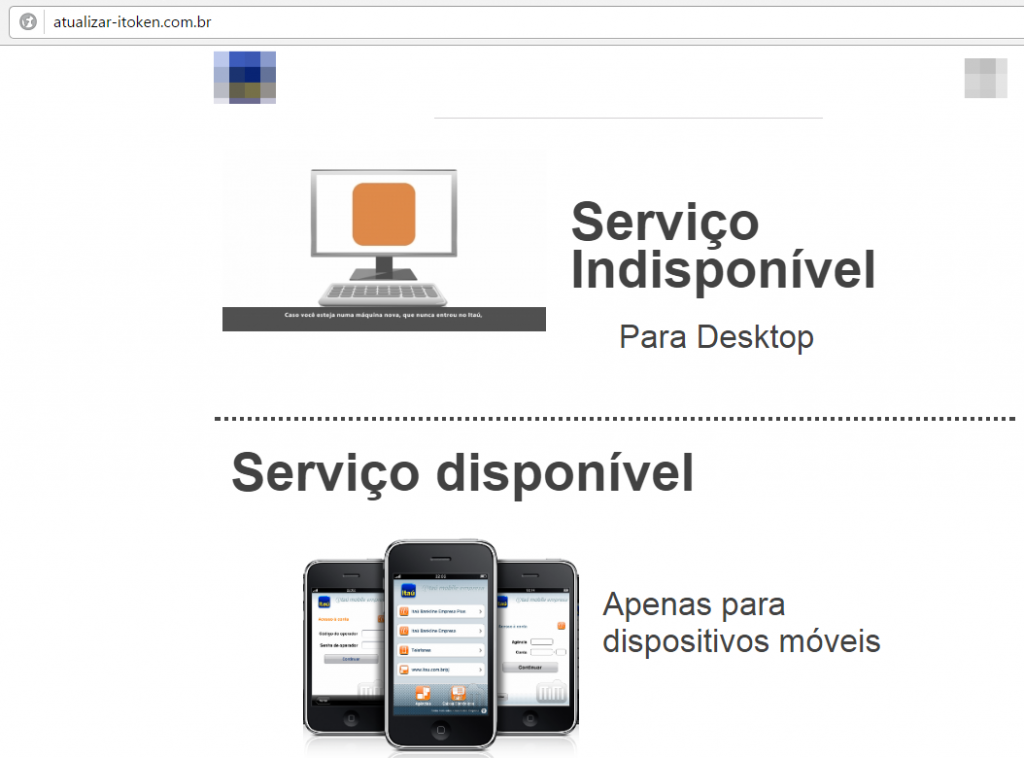
The mobile versions of these phishing banking websites open correctly in the browser, facilitating the theft of user credentials. The phishers’ tactic is to force the user to access the website via their mobile devices, and not from a desktop. If the victim tries to access the phishing domain using their computer, the following message displayed:
“Service unavailable for desktops, only for mobile devices”
The phishing domain only shows its full content when access is made via a mobile browser:
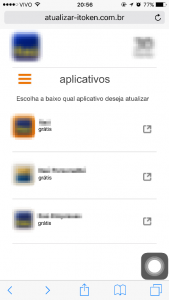
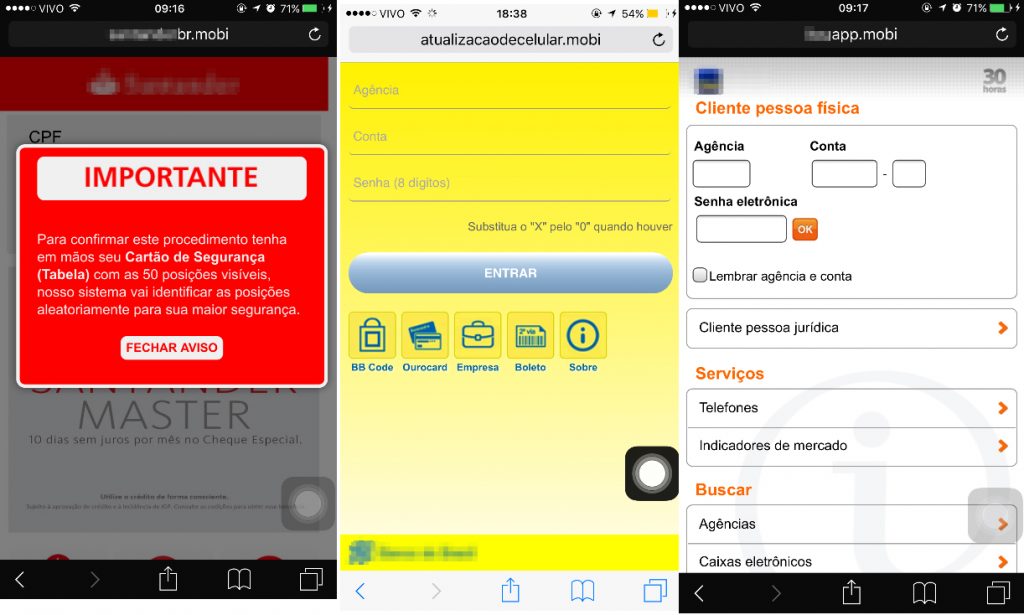
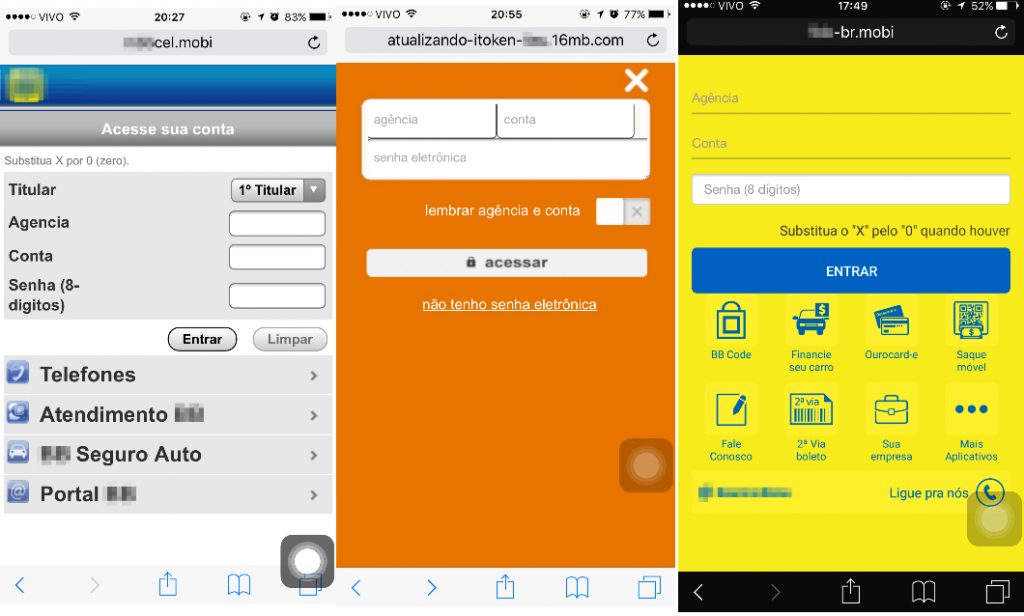
The cybercriminals create phishing pages for several banks, in an array of colors and styles:
Most of the domains used in these attacks are using the .mobi TLD:
We published a list of some of the domains we found here (if you’re an AV guy, block them!).
It’s important to highlight one other thing: if access is made from an IP outside of Brazil, some domains will display nothing. It’s a method used by Brazilian phishers to keep their attacks alive for as long as possible, because if you don’t see it, you won’t block the domain. Users of our products, including the Safe Browser for iOS, Windows Phone, Android and Fraud Prevention solutions are protected against mobile phishing and SMiShing attacks.





















SMiShing and the rise of mobile banking attacks