
The storm of phishing and malware attacks using the theme of the World Cup continues – some months ago we registered several malicious campaigns with this theme. To diversify the attacks and attract more victims, Brazilian cybercriminals decided to invest their efforts to spread fake giveaways and fraudulent websites selling tickets for the games at very low prices, tickets that in fact do not exist.
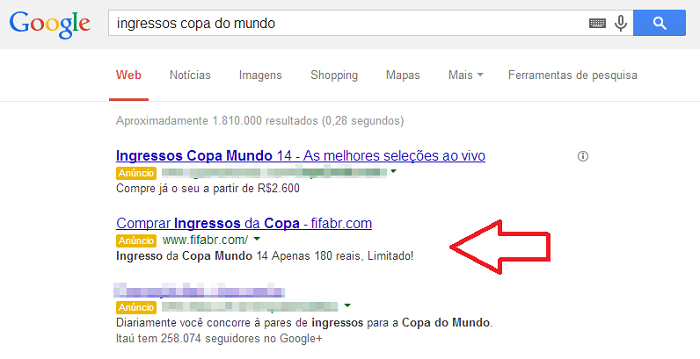
The attacks start when a user does a simple search on Google, looking for websites selling World Cup tickets. Bad guys registered the fraudulent domain fifabr.com that is displayed among the first results as a sponsored link:
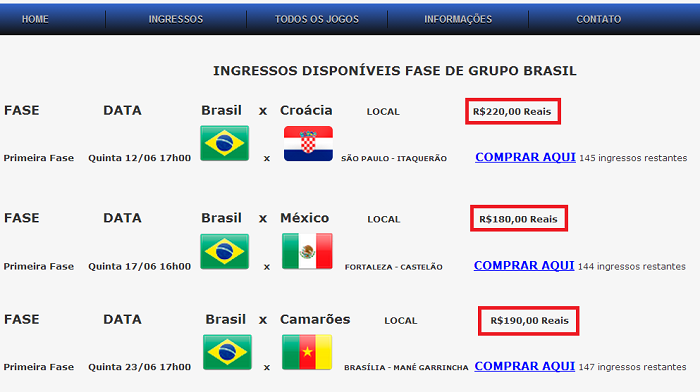
The fraudulent website offers tickets for Brazil’s games at the price $ 70,00:
Kaspersky products are blocking several fraudulent domains daily; all of them are using the theme of the World Cup. Such attacks are focused totally on Brazilian users and the messages generally use the names of local credit card, banks, and big stores, etc.
Phishing messages with fraudulent giveaways are getting common as well – some offering free tickets, cash, or even free travel:
To obtain the free ticket it is necessary to put all your personal data and your credit card number on the fraudulent website:
Some bad guys have also created a fake giveaway that is valid even after the Games:
Up until the beginning of the games many other attacks may appear – but we’re prepared to block them. Do not risk trying to buy tickets for the games at unknown sites – it is safer to buy them on the FIFA website, the online sales will restart on the 12 March 2014.
World Cup: Fake Tickets, Fake Giveaways, Real Attacks























Prince Kevin Ogoo
I will like to voluteer for the World Cup in Russia.