
Whatever type of game you take as an example – a card game, a board game, or a game of cops and robbers – attempts to cheat will be as old as the game itself. The spirit of competition drives people to break the rules in order to gain unfair advantages and, ultimately, win the game.
Why should computer games be an exception to this rule? So-called “cheats” are used in all types of game to help impatient or less skilled gamers to win a game more quickly or with a greater degree of success. Godmode (which ensures a character’s immortality) or the cheat for first person shooters which offers all weapons together with unlimited ammunition are both legendary examples of cheats.
Since cheap Internet access became widely accessible, online role-playing games (MMORPGS or Massive Multiplayer Online Role-Playing Games) have led the field in terms of the length and depth of gameplay offered. In these games, the gamer creates his/her own characters within a virtual fantasy world; together with other gamers around the world s/he can take on all manner of opponents.
Characters develop, or level up, in accordance with the amount of time spent playing, the quests achieved, and the number and type of opponents killed. It’s not only a character’s level and abilities which determine the character’s strength – equipment plays a very important role. Weapons in the form of swords, axes or bows, as well as armour, also contribute to success on the battlefield. The most powerful items are as coveted by gamers as they are hard to find. It takes a certain amount of luck for a valuable item to be dropped after an opponent has been defeated in combat.
Characters are often perceived as being the gamer’s alter ego. The multiple options available when creating characters offer a generous playground for creative gamers. The creation of appearance as well as the granting of personal capabilities support the process of creating genuine personalization of the new character. Just as many real people have a weakness for expensive watches, glasses, clothing and other luxury goods, virtual characters are rigged out with an equal level of care. Valuable in-game items which are owned or carried by characters can often be identified by fellow gamers, so they are not only important in battle, but also status symbols. In this light, the virtual world doesn’t differ much from the real world – not so surprising, then, that the term alter ego is sometimes used in this way.
Given the above, it’s no surprise that fully-fledged economies have evolved within online games. Trading plays an important role in getting in-game objects. In-game currency (usually virtual gold) is an object in itself. The perceived value and market price of items are quickly established, while game updates and expansion packs which add new objects bring a fresh breeze to the air of gaming’s virtual worlds. New objects, and new ways of acquiring them ensure that the market for in-game objects doesn’t stagnate; the game’s developers also track the market to ensure that balance is maintained within the game.
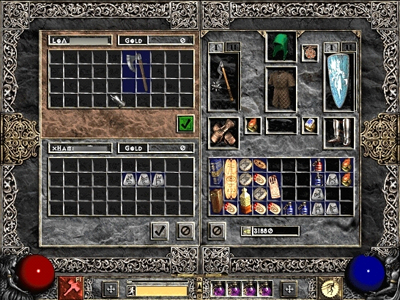
Trading in Diablo II
With World of Warcraft, the most popular MMORPG ever, resourceful players realized right from the start that they could supplement their real-world income by collecting in-game gold. A lot of gold can be “farmed” (i.e. acquired) in a relatively short space of time simply by using certain specific techniques; this can then be sold on via online auctions and other sites for real money. The same goes for rare objects or weapons. While the trading of in-game items for cash had taken place before World of Warcraft existed, it was with WoW that the bar was raised. Business boomed, and there were large profits to be made. Most game developers take pains to ensure that trading will be limited to the virtual world, as does Blizzard, the creator of World of Warcraft. Gaming terms and conditions prohibit trading outside the game, and sanctions usually consist of either the account being closed, or the CD keys which are needed to play being blocked. Nevertheless, this does not entirely put a stop to business.
This rapidly evolving market and its financial potential meant it would only be a matter of time before virus writers started to show interest. While many of the items, accounts and currency available for purchase were being sold by their owners, a large number were the ill-gotten gains of phishing attacks. In 2007, Sergey Golovanov from Kaspersky Lab wrote a detailed article about the methods used by scammers, including those used to steal account data and in-game items.
We’ve now reached a point where it’s worth pausing to take a look at the evolution of online gaming fraud, and specifically, to cast a little light on the economic interdependencies at play. This article focuses particularly on World of Warcraft for two reasons. Firstly, this game remains the most successful MMORPG ever. Secondly, the game has been around for a long time (at least in gaming terms); this is an advantage when considering the subject in terms of economics.
Phishing
Sending phishing emails is an old technique used by cybercriminals to get access to account data. This technique has’n’t altered much over the years. Phishing emails used to be easy to detect due to numerous spelling and grammar errors. However, cybercriminals have now resolved this issue and even security aware recipients could be fooled by today’s phishing emails.
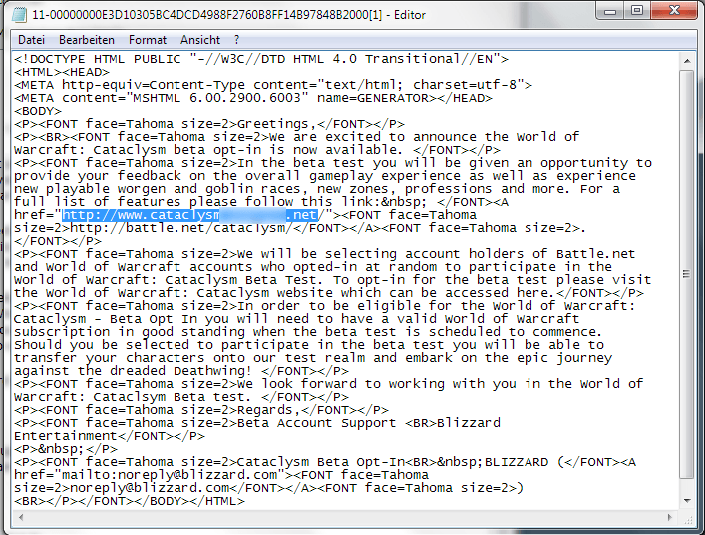
At the moment, cybercriminals are focusing their phishing campaigns on two online games – World of Warcraft and Aion. A hotly awaited add-on for World of Warcraft which is being released in the near future is being used bait for phishing attacks on gamers. The screenshot below shows an email allegedly sent from Blizzard, which states that open beta testing is starting, and that interested gamers should register in order to be gain a chance to participate.
The mail header reveals the true origins of the message. At first glance, the account noreply@blizzard.com seems to be genuine. However, the email has actually been sent from a private email address:
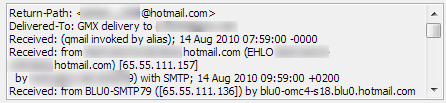
As the screenshot shows, the email asks the recipient to follow the link and then use their Battle.Net accout details to log in. This link appears to lead to the genuine Battle.net site (the online platform of Blizzard); however, as the mail is sent in HTML format, the visible text hides a different destination. In this example, simple HTML code is used; however, Javascript is also often used to lead victims to phishing sites. Once again, this acts as a reminder to view emails in text format; this means that either you will be able to spot the deceptive destination address at once, or the redirect simply won’t work.
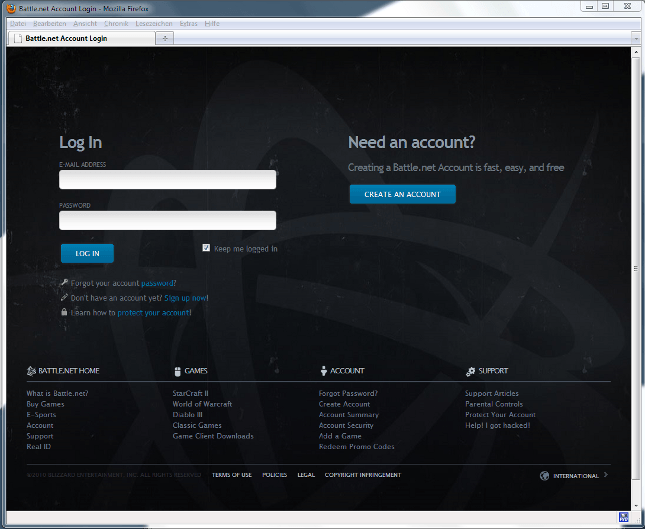
If you click on the link, you end up on a fake log-in page, which looks deceptively similar to the real Blizzard page. Enter your log-in details, and they’ll be saved and subsequently harvested by cybercriminals. Apart from a briefly displayed “Processing…” message, nothing seems to happen once you’ve clicked “Log In”, which could make you think there’s simply a problem with the site’s operation.
All the other links lead to genuine pages on the real Battle.net site.
This is only one example of the many types of standard phishing email. The most commonly used approach is an email warning that the gaming account may have been compromised, and telling the recipient to log in to secure their account. Of course, the log-in site is fake. This method is used to target almost all online games.
In recent years, cybercriminals have focused their efforts on upgrading the quality of their phishing attacks, rather than simply increasing the number of phishing emails sent. As a result both the appearance and content have markedly improved
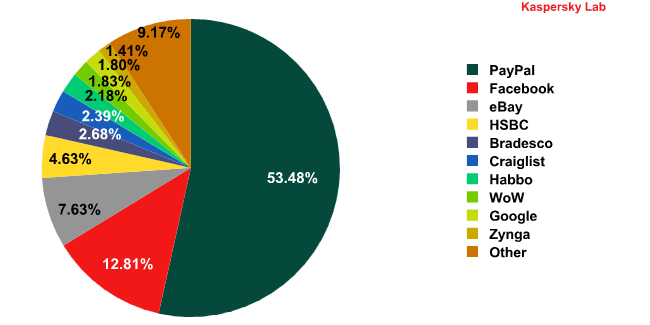
However, as the diagram above shows, phishing emails targeting online games form a very small proportion of all phishing emails. Only World of Warcraft with 1.83% (July 2010) rates a separate category; other MMORPGs do not even rate on the scale.
Malware
Since 2002, when the first Trojan designed to steal account data appeared (Trojan-PsW.Win32.Lmir), a lot of water has flowed under the bridge. Nevertheless, the fundamentals remain essentially the same: as soon as the gamer logs into the online game platform, the gaming Trojan used activates, and logs data entered. Data is usually saved locally on the victim machine and then sent to the malware writers by email or FTP. Nevertheless, gaming malware is evolving in other ways.
Many gaming Trojans are now designed to harvest log-in credentials from different games. As online gaming platforms are installed on only a small proportion of all computers world-wide, targeting more than one game at a time increases the chances of success severalfold. This type of malware is called Trojan-GameThief.Win32.OnLineGames; Kaspersky Lab had 1.2 million records for such malware as of 10th August 2010. However, there are still malicious programs which only target a single gaming platform: for instance, Trojan-GameThief.Win32.WOW, which targets World of Warcraft; Trojan-GameThief.Win32.Perforld, which targets Perfect World, and Trojan-GameThief.Win32.Nilage, which targets Lineage.
The graph below shows the growth in the number of new malicious programs at six month intervals.
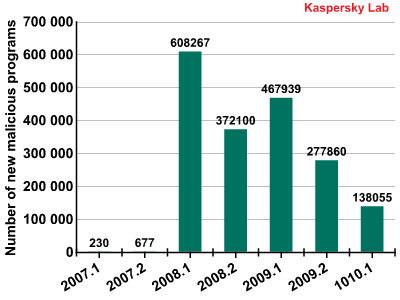
1H 2008 holds the record for the highest number of new malicious programs targeting online games. More than 608,000 new malicious programs were detected, probably due to the three releases listed below:
- “Burning Crusade”, a WoW expansion pack (released in 2007, there may have been a delayed effect)
- Aion
- Perfect World (released in 2008 in Europe and North America)
The figure sank in Q2 2008 to around 370,000, before rising again in 1H 2009. This seems to be linked to the release of another WoW expansion pack, “Wrath of the Lich King”, in November 2008.
Since then the numbers have fallen steadily. Around 138,000 pieces of new gaming malware appeared in 1H 2009, bringing the total number of records for this type of malware in the Kaspersky Lab collection to 1,878,750 (6th August 2010).
A look at the geographical distribution of attempted attacks using gaming malware shows that these programs are particularly widespread in Asia. The data is generated by Kaspersky Lab’s in-the-cloud service, the Kaspersky Security Network (KSN). The figures given below only reflect the attack attempts actually detected, and do not claim to be comprehensive. This means that the total number of attacks could be significantly higher.
| Country | Attack attempts per day |
| China | 872.676 |
| India | 214.848 |
| Russian Federation | 174.155 |
| Turkey | 163.584 |
| Vietnam | 156.262 |
| Mexico | 125.476 |
| Poland | 103.031 |
| Thailand | 99.205 |
| Malaysia | 95.227 |
| Spain | 93.281 |
In total, Kaspersky Lab detects an average of more than 3.44 million gaming malware attacks every day. Although World of Warcraft was, for a long time, the most targeted game, it has now being overtaken by Maple Story, an Asian MMORPG. The table below shows the twenty games most often attacked between January 2009 and March 2010.
- Maple Story
- World of Warcraft
- Perfect World
- Lineage
- Woool
- Cabal Online
- PlayOnline Viewer (Online Gaming Plattform mit mehreren Spielen)
- Mojie online
- Dekaron
- Gamania
- Huaxia II Online
- Tales Weaver
- SilkRoad Online
- Tenio
- Ragnarok Online
- Dungeon & Fighter
- LaTale
- Seal Online
- Reign of Revolution
- Lying West Online II
This list confirms the trends shown in the table giving data on geographical distribution of attacks. Many of the games listed above originate in Asia, and many are unknown in the rest of the world.
An economic analysis
In the last three to four years, cybercriminals have made large profits by selling stolen gaming accounts and in-game items. Cybercriminals quickly realized that what started as aniche activity was actually a significant source of profit.
Given that cybercriminals want to make a profit, it’s essential that they choose the right game to target. The size of the gaming community plays the biggest role here. When sending phishing mails and spreading malware, the target group must be big enough to justify the effort. Attacks on gamers aren’t targeted, but use the law of averages: in order for an attack to be worthwhile, there has to be a chance that a certain percentage of recipients will also be those who play a particular game.
Regional considerations also play a role when choosing which game to attack. Some games – such as Maple Story, for example – are only accessible from certain countries or continents. However, the number of gamers involved can be high enough to make such games a profitable target. Of course, language and culture need to be taken into account when creating phishing mails in order to make them effective, and cybercriminals have made great progress in this area.
The readiness of the gaming community to pay real money in return for virtual items is also a factor which should be taken into account. If the community associated with a particular game does not, in the main, wish to do this, in-game items cannot be used to turn a significant profit. WoW is a case in point here; although the subscription fee for play has been raised, gamers, after initial rumblings, have accepted the need to pay the increased amount. If gamers are willing to pay more to play a game, they are also likely to pay in-game items.
Economic laws govern the trade in virtual items, just as they do the trade in real world items. When World of Warcraft was launched in 2004, there was a shortage of both high value in-gameitems and in-game gold. Newly found treasure could therefore be traded for high prices via the usual channels such as online auctions and online shops. In the years that followed such items became more common. Consequently, the number of items available increased, while at the same time the gaming community was growing. As a result, the price of high value items remained relatively stable, while the potential market grew.
At this point, around 2007, cybercriminals started jumping on the bandwagon. As a result, the market became saturated and the seller’s market became a buyer’s market. Vendors of stolen goods found themselves locked in a price war in order to get rid of their goods, resulting in plummeting prices.
The potential profit per head (and thus the motivation of the cybercriminals) decreased considerably., This left an increasing number of cybercriminals having to divide an ever shrinking turnover. As a result, the number of new malicious programs has dropped in comparison to preceding years. It may be that many cybercriminals have moved away from this lucrative type of business. Neverthless, attacks using gaming malware still number 3.4 million every day, a very high number, which means that gamers remain at risk.
The market today
In order to get an overview of the market, and to estimate how extensively gaming accounts are traded, we examined sales on eBay. As a centralized sales platform, eBay offers certain distinct advantages in comparison to researching decentralized online shops, as it offers worldwide coverage. Additionally, eBay is the sales channel most often used to trade gaming-related items.
For this research, we searched globally for “World of Warcraft account”, with the proviso that only finished deals should be shown. As it can be difficult to distinguish legitimate account sales from illicit ones, we looked at everything on offer, in order to gain a clear picture of the size of the market.
From 27th July to 11th August 2010, there were exactly 900 offers: he average price was 126.80 euros. The lowest asking price was 1 euro, and the highest 999 euros.
The total turnover for the period under consideration was 114,118 Euros, which would give a monthly turnover of approximately 228.000 Euros. If we assume a stable stream of offer and prices at the same level, this results in an annual turnover of 2.74 million euros – a huge amount of money when you consider that this is money being paid simply for the right to use virtual items and characters.
It’s safe to say that in 2008, when trading of gaming items reach a high point, the turnover was much higher, particularly if all possible sales channels are taken into consideration.
The future
A look at the future brings up the question of how the market – and the associated spread of new malware and phishing mails – will evolve. Experience shows that the aspects listed below will play a role:
- Game and expansion pack releases
- Size of the community associated with a particular game
- Willingness of the gaming community to pay for virtual assets
Currently, gaming threats are trending downwards. However, the underground economy is likely to revive in the near future due to two events:
- Blizzard has announced an expansion pack, called “Cataclysm” for World of Warcraft; however, a release date has not yet been announced. Although the game may have already passed its peak of popularity, an expansion pack with its associated change of rules, new items and characters, is likely to give the game a new lease of life.
- Diablo 3 will likely give rise to the next big surge in cybercriminal activity. This game’s predecessor was released in 2000, and is still hugely popular, with players around the world waiting eagerly for the third installment. Incidentally, Diablo II was one of the first online role-playing games for which virtual assets were sold online in return for real money.
How can you ensure that your gaming account (the one you’ve spent so much time and energy on building up) dones’t get stolen? An effective, up-to-date security solution will provide reliable protection against malware which harvests account data and then transmits it to cybercriminals. However, many gamers decide not to use a security solution. Why? Because they believe that such programs hog system resources and – particularly relevant in the case of online gaming – bandwidth.
Kaspersky Anti-Virus and Kaspersky Internet Security 2010 and 2011 offer a dedicated gaming mode; updates and scheduled on-demand scans can be deferred, but on-access protection remains active. This ensures that the gaming experience isn’t affected and the computer remains protected against malware.
In addition to antivirus technologies, Kaspersky Internet Security offersa spam filter which flags phishing emails. Phishing sites are also detected and are blocked by the browser.
However, common sense is still the best protection. Game developers never ask for account data, so you should never click on links sent via email. If an email really seems as though it might be genuine, you should enter the URL manually into your browser or use a bookmark. A healthy dose of scepticism can do wonders and prevent your gaming experience from being spoilt.





















Online gaming fraud: the evolution of the underground economy