
According to the United Nations, small and medium-sized businesses (SMBs) constitute 90 percent of all companies and contribute 60 to 70 percent of all jobs in the world. They generate 50 percent of global gross domestic product and form the backbone of most countries’ economies. Hit hardest by the COVID pandemic, geo-political and climate change, they play a critical role in a country’s recovery, requiring greater support from governments to stay afloat.
In the past, the perception was that large corporations were more attractive to cybercriminals. Yet in reality, cybercriminals can target anyone, especially those who are less protected, while small businesses typically have smaller budgets and are not as securely protected as larger companies.
According to a report by the Barracuda cybersecurity company, in 2021, businesses with fewer than 100 employees experienced far more social engineering attacks than larger ones. That same year saw one of the worst ransomware incidents in history, the Kaseya VSA supply-chain attack. By exploiting a vulnerability in the software, the cybergang REvil infiltrated between 1,500 and 2,000 businesses around the world, many of which were SMBs. For example, the attack hit a small managed service provider Progressive Computing, and, by virtue of the domino effect, the company’s 80 clients, which were mainly small businesses. Although the attack was stopped fairly quickly, the SME sector was understandably shaken, alerting businesses to the fact that everyone was vulnerable.
According to the Kaspersky cyber-resilience report, in 2022, four in ten employers admitted that a cybersecurity incident would be a major crisis for their business, superseded only by a slump in sales or a natural disaster. A cybersecurity crisis would also be the second most difficult type of crisis to deal with after a dramatic drop in sales if judged by the results of the survey.
In this report, we have analyzed the key threats to small and medium-sized companies in 2022 and 2023, and provided advice on how to stay safe.
Methodology
The statistics used in this report were collected from January through May 2023 by Kaspersky Security Network (KSN), a system for processing anonymized cyberthreat-related data shared voluntarily by Kaspersky users.
To assess the threat landscape for the SMB sector, Kaspersky experts collected the names of the most popular software products used by its clients who owned small or medium-sized businesses around the world. The final list of the software includes MS Office, MS Teams, Skype and others used by the SMB sector. We then ran these software names against Kaspersky Security Network (KSN)* telemetry to find out how much malware and unwanted software was distributed under the guise of these applications.
Malware attacks
Between January 1 and May 18, 2023, 2,392 SMB employees encountered malware or unwanted software disguised as business applications, with 2,478 unique files distributed this way. The total number of detections of these files was 764,015.
Below is a brief description of the most popular types of threats that SMB employees encountered in January–May 2023:
Exploits
The biggest threat to SMBs in the first five months of 2023 were exploits, which accounted for 483,980 detections. Malicious and/or unwanted software often infiltrates the victim’s computer through exploits, malicious programs designed to take advantage of vulnerabilities in software. They can run other malware on the system, elevate the attackers’ privileges, cause the target application to crash and so on. They are often able to penetrate the victim’s computer without any action by the user.
Trojans
The second-biggest threat were Trojans. Named after the mythical horse that helped the Greeks infiltrate and defeat Troy, this type of threat is the best-known of them all. It enters the system in disguise and then starts its malicious activity. Depending on its purpose, a Trojan can perform various actions, such as deleting, blocking, modifying or copying data, disrupting the performance of a computer or computer network, and so on.
Backdoors
The third most common threat are backdoors. These are among the most dangerous types of malware as, once they penetrate the victim’s device, they give the cybercriminals remote control. They can install, launch and run programs without the consent or knowledge of the user. Once installed, backdoors can be instructed to send, receive, execute and delete files, harvest confidential data from the computer, log activity, and more.
Not-a-virus
Potentially unwanted applications (PUAs) that can be inadvertently installed on your device are labeled “not-a-virus” by our solutions. Although they are listed among the most widespread threats and can be used by cybercriminals to cause harm, they are not malicious per se. Nonetheless, their behavior is annoying, sometimes even dangerous, and the antivirus alerts users because, despite being legal, they often sneak onto the device without the user realizing.
TOP 10 threats for SMBs, January-May 2022 (download)
TOP 10 threats for SMBs, January-May 2023 (download)
Cybercriminals attempt to deliver this and other malware and unwanted software to employees’ devices by using any means necessary, such as vulnerability exploitation, phishing e-mails and fake text messages. Even something totally unrelated to business, such as a YouTube link, may be used to target SMBs, as their employees often use the same devices for work and personal matters.
One of the methods often utilized to hack into employees’ smartphones is so-called “smishing” (a combination of SMS and phishing). The victim receives a link via SMS, WhatsApp, Facebook Messenger, WeChat or some other messaging app. If the user clicks the link, malicious code is uploaded into the system.
Examples of scam threats and phishing
Phishing and scam can pose a significant threat to SMBs, as scammers try to mimic payment, loan and other services, as well as cloud service providers like Microsoft, in order to obtain confidential information or company funds. Often, the phishing pages where the employees land if they click a link in a scam e-mail are tailored to look like login pages to the target systems with the corresponding logo on the page. Below, we provide several examples of phishing pages that imitate various services in an attempt to get hold of the target company’s data and money.
-
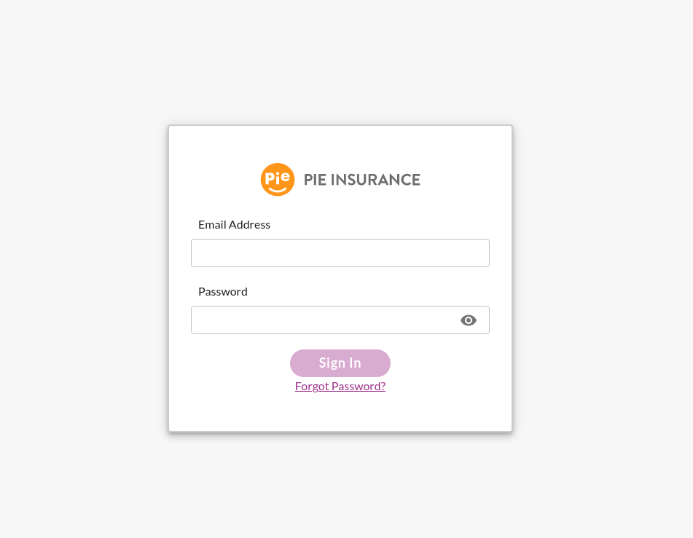
An insurance company
On the screenshot above scammers are trying to hack the insurance company account of its client’s employee.
-
A “personal” banking service
These scammers disguise themselves as a financial institution. On the phishing page that claims to offer personal banking services, they ask users to log in with their corporate banking account credentials. If an employee enters their credentials, the scammers get access to their account.
-
A fake website pretending to be a legitimate delivery service
Here, the cybercriminals imitate the website of a well-known delivery provider in order to fool businesses into giving away their corporate DHL accounts.
Scammers often reach employees by e-mail. Attackers use social engineering techniques to try to trick employees into following a phishing link, revealing the company’s confidential data or transferring money.
For example, in late 2022, scammers posing as top-level executives of a company sent out e-mails to their employees, instructing them to move money from a business account into another account urgently. Fake e-mails were thoroughly crafted, so that the employees would not question their authenticity.
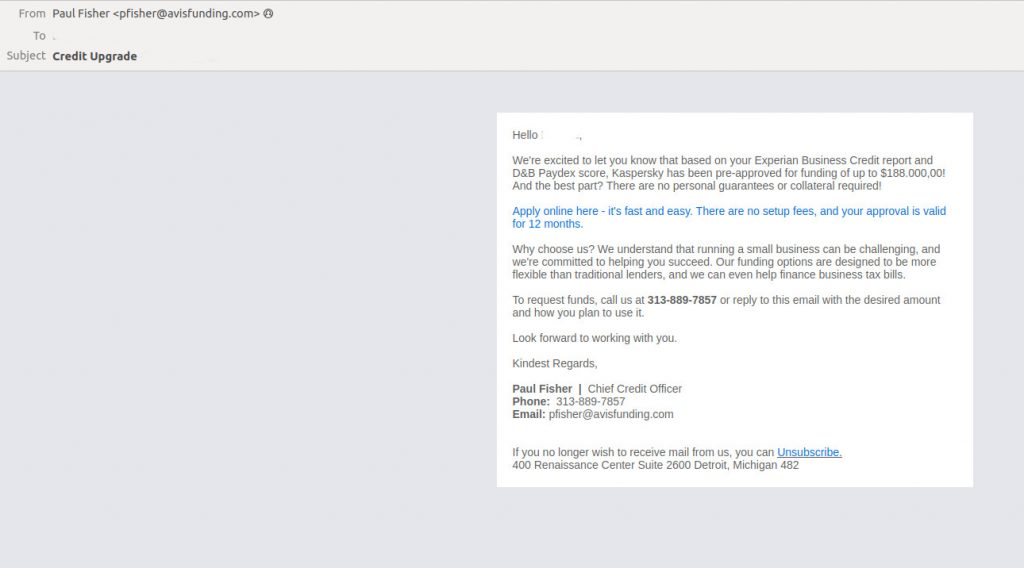
Some spammers pretend to be representatives of financial organizations offering attractive deals to startup businesses. However, by applying for funding thus offered, an employee may give out sensitive data or even lose company money.
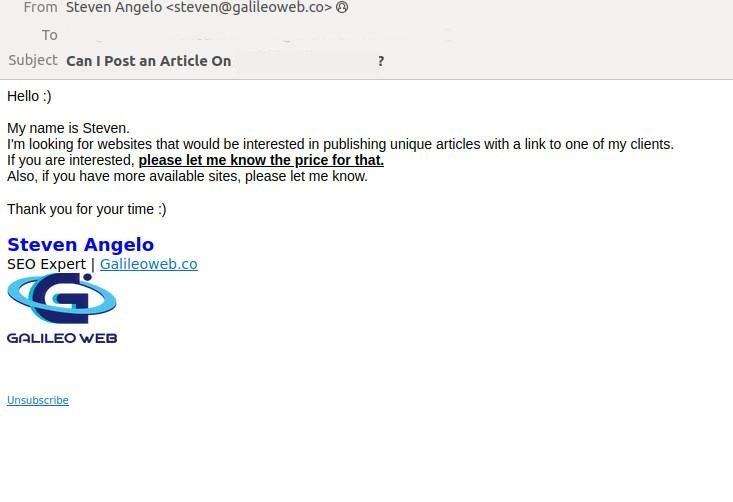
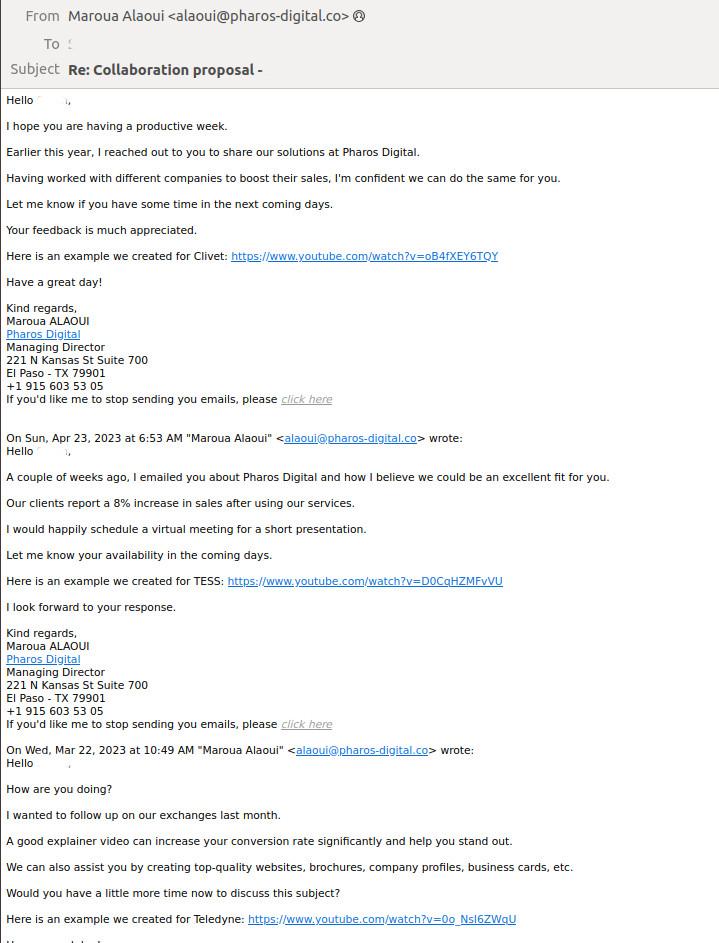
SMB employees and especially managers are often the target of spam campaigns touting collaborations and B2B services, such as SEO, advertising, recruitment assistance and lending. Small and little-known firms with questionable service quality typically promote themselves that way. Often they send their offer repeatedly, even if they never receive an answer.
Qbot Trojan using a conversation hijacking technique
Recently, Kaspersky researchers discovered a new campaign employing the “conversation hijacking” technique. The attackers gained access to the victim’s e-mail and replied to their conversations. Posing as one of the respondents in the e-mail chain, the fraudsters sent a message with a PDF attachment asking the victim to download it. The PDF contained a fake notification from Microsoft Office 365 or Microsoft Azure which unleashed the Qbot Trojan when downloaded. The attackers also sent messages containing a URL that was supposed to lead to an “important business document”.
Qbot (aka QakBot, QuackBot, and Pinkslipbot) has been around since 2007. This malware is classified as a banking Trojan as it enables hackers to mine their victims’ banking credentials. The malware can also collect cookies from victims’ browsers, access their correspondence, spy on their banking activities and record keystrokes. Finally, the Trojan can install other malware, such as ransomware.
Conclusion
As cybercriminals target SMBs with all types of threats — from malware disguised as business software to elaborate phishing and e-mail scams — businesses need to stay on high alert. This is critical, because a single cyberattack can lead to catastrophic financial and reputational losses for a company. To keep your business protected from cyberthreats, we recommend you do as follows:
- Provide your staff with basic cybersecurity hygiene training. Conduct a simulated phishing attack to ensure that they know how to recognize phishing e-mails.
- Use a security solution for endpoints, such as Kaspersky Endpoint Security for Business or Cloud-Based Endpoint Security, to minimize the chances of infection.
- If you are a Microsoft 365 user, remember to protect that too. Kaspersky Security for Microsoft Office 365 includes dedicated apps that target spam and phishing, and protect SharePoint, Teams and OneDrive for secure business communications.
- Set up a policy to control access to corporate assets, such as e-mail boxes, shared folders and online documents. Keep it up to date and remove access if the employee has left the company or no longer needs the data. Use cloud access security broker software that can help manage and monitor employees’ cloud activity and enforce security policies.
- Make regular backups of essential data to ensure that corporate information stays safe in an emergency.
- Provide clear guidelines on the use of external services and resources. Employees should know which tools they should or should not use and why. Any new work software should go through a clearly outlined approval process by IT and other responsible roles.
- Encourage employees to create strong passwords for all digital services they use and to protect accounts with multi-factor authentication wherever applicable.
- Use professional services to help you get the most out of your cybersecurity resources. The new Kaspersky Professional Services Packages for SMB provides access to Kaspersky’s expertise on assessment, deployment and configuration: all you need to do is add the package to the contract, and our experts will do the rest.
How cybercrime is impacting SMBs in 2023

























Santi Opperman
Feel much saver with Kaspersky on all devises