
As the annual Black Friday approaches, the digital landscape experiences an unprecedented surge in e-commerce and online shopping activity. Major sales aside, e-commerce is still a huge market. In 2022, global e-commerce retail revenue was estimated to reach $5.7 trillion worldwide, marking nearly a 10% increase compared to the previous year. The annual Black Friday rise in online transactions sets the stage for a cyber-battleground, where malicious actors exploit users’ interest in online shopping.
Against this backdrop, our report delves into the intricate web of cyberthreats relating to e-commerce and the Black Friday season. As consumers flock to online platforms in search of exclusive deals, the threatscape also witnesses increased fraudulent and cybercriminal activity, which necessitates a comprehensive understanding of the cybersecurity challenges faced by individuals during this festive shopping spree.
Methodology
In this research, we examine various types of threats, such as financial malware and phishing pages that imitate the world’s largest retail platforms, banks and payment systems. The threat statistics we reference are sourced from the Kaspersky Security Network (KSN), a system that processes anonymized cyberthreat data voluntarily shared by Kaspersky users. This data spans the period from January through October 2023. Furthermore, we conducted an analysis of Black Friday–related spam and phishing activity in the weeks leading up to Black Friday.
Key findings
- In the first ten months of 2023, Kaspersky identified 30,803,840 phishing attacks that targeted online stores, payment systems, and banks.
- E-commerce platforms bore the brunt, used as a lure in 43.5% of the total attacks (13,390,142 attacks).
- Phishing pages mimicking popular shopping platforms (Amazon, eBay, Walmart, AliExpress, and Mercado Libre) totaled 6,232,882 in the first ten months of 2023.
- Apple consistently stood out as the most popular lure, with phishing attempts using its name reaching 2,844,828 in the first ten months of 2023.
- In the first two weeks of November, Kaspersky detected 92,259 spam emails containing the keywords “Black Friday”.
- From January through October 2023, Kaspersky products detected and prevented nearly 20 million attacks that relied on banking Trojans.
Phishing
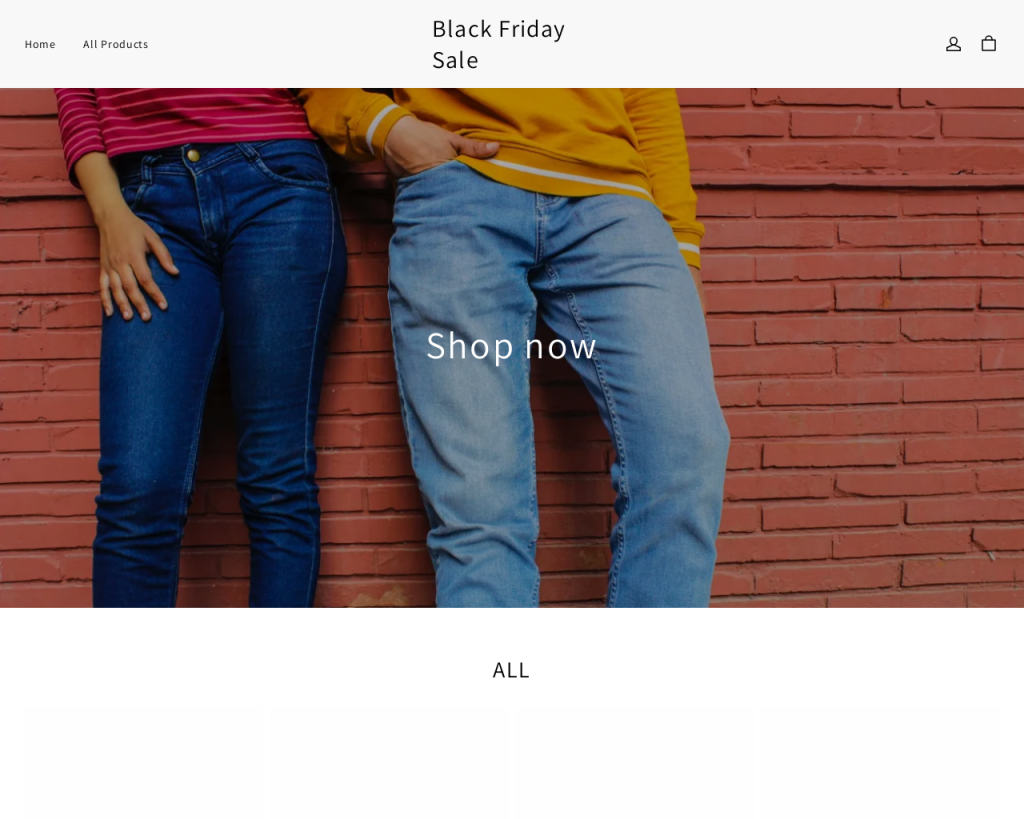
Since the beginning of fall, Kaspersky products have consistently identified a substantial number of scam stores offering clothing, appliances, and gadgets. The prevalent scheme involves the creation of fraudulent stores where individuals pay for products that they never receive. Recognizable patterns include consistent use of similar website templates, often repetitively. These deceptive sites often utilize generic domains, frequently in dubious domain zones like .top.
Since October, there has been a notable, threefold increase in the number of domains using the words “Black Friday”. Websites hosted in these domains are either nonexistent stores or convincing replicas of real online stores. Copycat sites using lookalike domains are also actively employed by the fraudsters. To exploit the Black Friday fever, they advertise products at remarkably low prices, leading users to unwittingly lose money by making what they think is a legitimate purchase.
Another scheme involves the victim linking a card, supposedly to pay for goods, with scammers gradually withdrawing money, emptying the victim’s account. For instance, the fake website shown below mimics a well-known shopping platform, enticing users with an offer to acquire an €800 gift card for a mere €1.95. To claim this seemingly irresistible deal, users are prompted to provide their contact information and proceed with the payment. However, falling for this scheme leads to disappointment, as the promised gift card is typically nonexistent, and users end up losing money to the scammers behind this fraudulent setup.
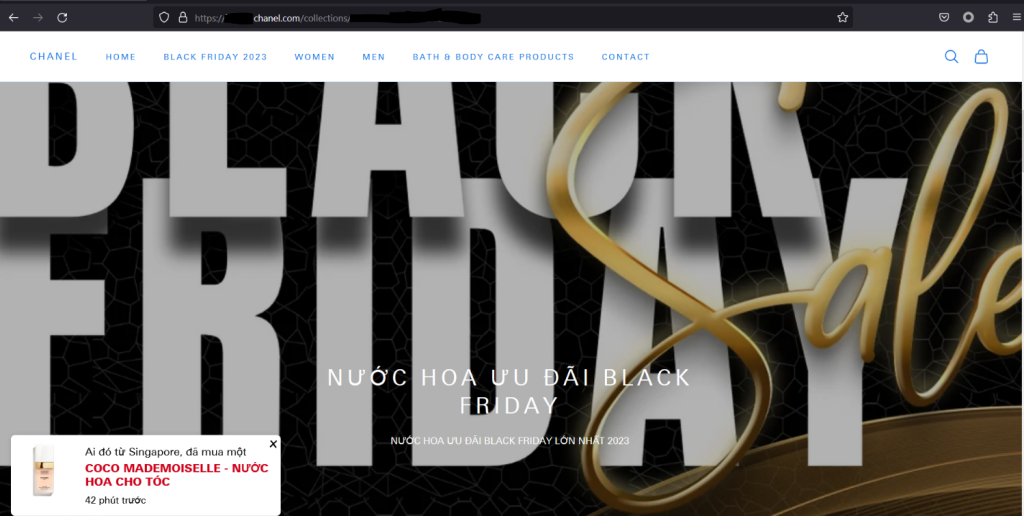
Millions of shopaholics worldwide eagerly anticipate Black Friday for a chance to snag luxury branded items at discounted prices. However, scammers target the luxury segment, too, for the higher potential gain. In the screenshot below, a phishing site mimics Chanel. The website attracts users with the bright sale banner, but a suspicious domain gives away the fraudulent activity.
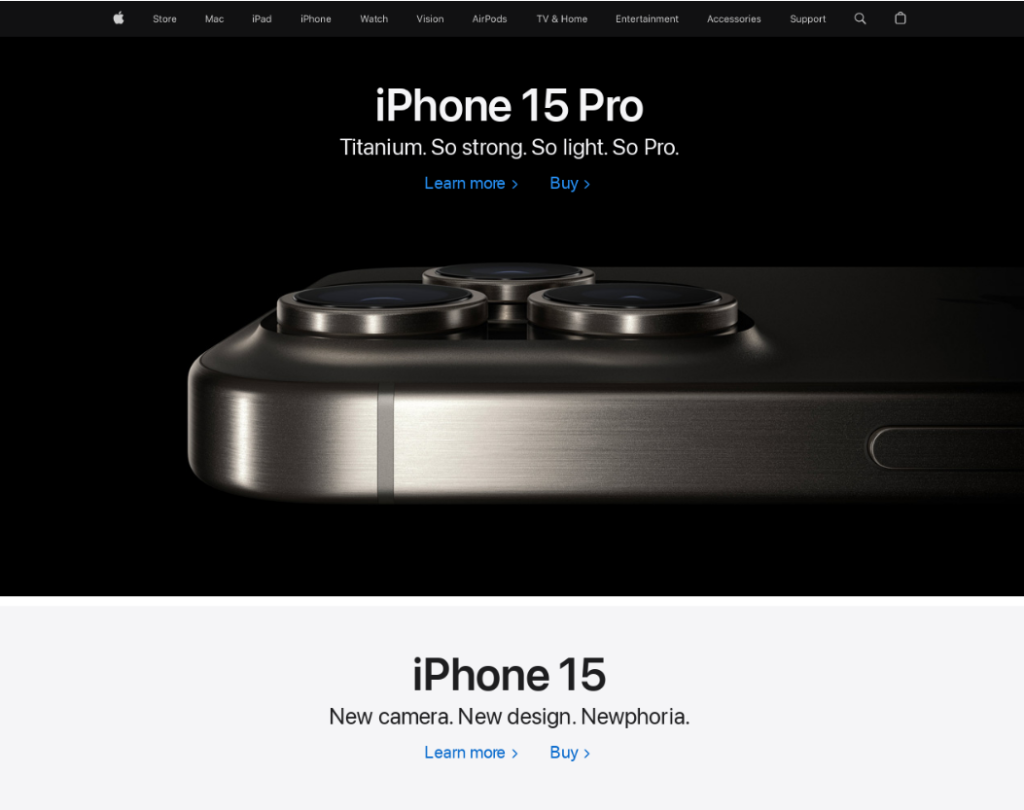
Another highly profitable niche for fraudsters is centered on gadgets and devices, with a notable focus on Apple products observed throughout the year. From January through October 2023, Kaspersky’s anti-phishing systems thwarted more than 2.8 million attempts to visit phishing websites mimicking Apple products and services or enticing users with exclusive bargains and giveaways of Apple products across various marketplaces.
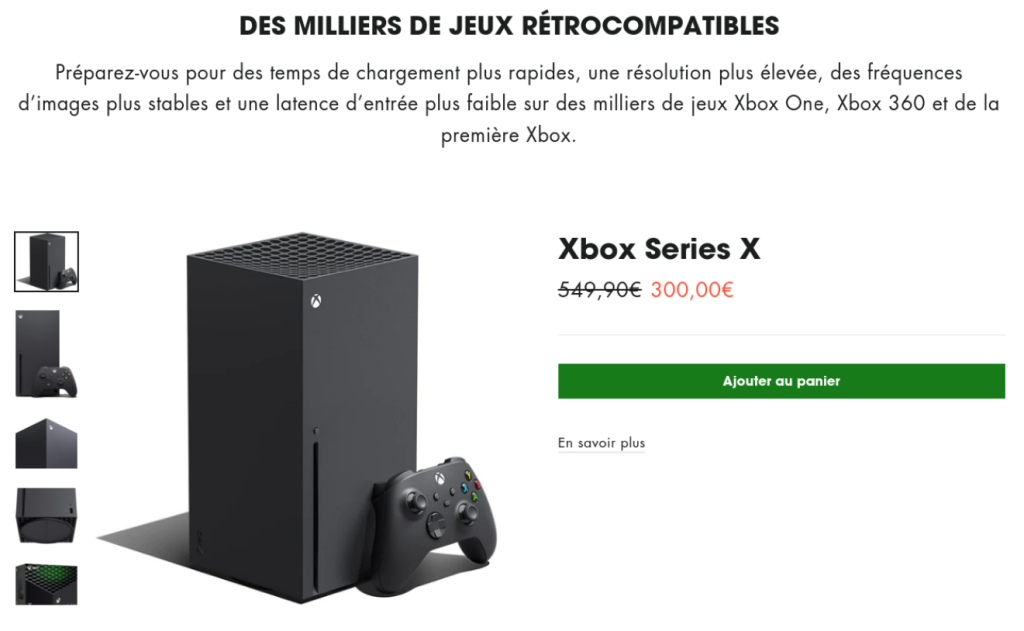
Another substantial portion of scams targets gamers. Console scammers employ various tactics to persuade users to part with their money, only to vanish without delivering the promised console. This leaves victims without their expected purchase and significantly out of pocket.
Beyond the financial repercussions, scam victims also unwittingly expose their personal and identifying information. Although fraudsters typically collect user data, such as name, address and contact details, to make their scams appear more convincing, and do not use it afterwards, exposing the information to a dubious third party does not bode well for the user.
Phishing statistics
Kaspersky products detect various forms of financial phishing, such as banking, payment system, and online store phishing. Banking phishing involves the creation of counterfeit bank websites designed to trick victims into submitting their credentials and card details. Payment system phishing involves the replication of well-known payment platforms like PayPal, Visa, MasterCard, and American Express. Online store phishing mimics Amazon, eBay, AliExpress, and smaller retailers.
In the first ten months of 2023, Kaspersky products detected 30,803,840 attempts to follow phishing links that targeted users of online shopping platforms, payment systems, and banks. E-commerce phishing accounted for 43.47% of these attacks, with a hefty share of 13,390,142 detections. Fake bank sites accounted for 35.19% of the phishing onslaught, and phishing that targeted payment system users constituted 21.34% of the total detections.
Financial phishing attacks by category, January–October 2023 (download)
In 2023, fraudsters strategically homed in on the allure of Amazon, with nearly 5 million attempts to follow a phishing link imitating this platform prevented by Kaspersky products. This activity peaked in August, with more than 900,000 Amazon-related detections. This underscores scammers’ astute ability to synchronize with shopping trends by stepping up their activity during peak periods like holidays and back-to-school seasons. Noteworthy global brands like eBay, Walmart, and Alibaba also found themselves in phishers’ crosshairs. Local brand users were targeted as well. For example, users of the Latin American marketplace Mercado Libre tried to open phishing links over 240,000 times.
Number of attempts to visit phishing pages that targeted popular online store users, January–October 2023 (download)
Spam
As Black Friday approaches, the digital landscape witnesses a surge in spam orchestrated by fraudsters who seek to capitalize on heightened online shopping activity and small online stores willing to promote themselves. In the weeks leading up to this retail extravaganza, spam campaigns intensify significantly. Kaspersky telemetry detected a substantial rise in the number of spam emails containing the term “Black Friday”, as the shopping fest approached. This surge reached a peak, soaring to 28.8 times the figures observed in September during the first two weeks of November and totaling 92,259 spam emails.
Banking Trojans
Banking Trojans (bankers) are the go-to tool in the arsenal of cybercriminals looking to capitalize on the sales season. These are malicious computer programs designed to gain access to confidential information stored or processed by online banking and payment systems. Armed with web injection and form-grabbing functionality, bankers aim to pilfer credentials, card details, or any data entered by users on the target website, which can be not only an online bank or payment system website, but also a website of a major online marketplace or gaming store.
In 2023, despite a modest 7% reduction in banking Trojan attacks, cybercriminals continue to employ these techniques with notable persistence. In the wake of a sharp 92% year-on-year increase observed last year, when Kaspersky products detected and prevented almost 20 million attacks, the figure has remained largely unchanged. This underscores the ongoing challenges and evolving strategies that cybercriminals deploy in their attempts to compromise online security.
Overall number of banking Trojan attacks, January–October 2021–2023 (download)
Conclusions
As Black Friday draws on, the number of phishing and spam attacks against online shoppers rises. Although the tricks the fraudsters employ remain largely the same, the sales season makes them look more convincing with their fake deals. Amid a surge in online shopping activity, particularly during peak seasons like Black Friday, individuals must exercise caution, verify the legitimacy of offers, and be wary of unsolicited communications. By fostering a culture of cyber-awareness, staying up to date on emerging threats, and implementing robust security measures, users can effectively fortify themselves against the multifaceted risks lurking in the digital realm.
A good helper in such a hot period of sales can be a comprehensive security solution. They can help users to detect and avoid phishing pages, as well as scan all downloaded files and delete malicious ones. Besides, reliable security service can also ensure safe shopping experience via various browsers, keeping financial data and money safe and protected.























The dark side of Black Friday: decoding cyberthreats around the year’s biggest shopping season