
Last July, we published details on Crouching Yeti (aka Energetic Bear), an advanced threat actor involved in several APT campaigns.
A quick summary:
- Campaign status: Active
- Discovery: January 2014
- Targeted platforms: Windows
- First known sample: 2010
- Number of targets: 2,001-3,000
- Top target countries: United States, Spain, Japan, Germany, France, Italy, Turkey, Ireland, Poland, China
- Propagation method: Social engineering, Exploit, Watering hole attack, Trojanized software installers
- Purpose/functions: Data theft
- Special features: Interest in OPC/SCADA. Trojanized software used to administer remote OPC servers as well as modules to scan networks for OPC servers.
- Targets: Industrial/machinery, Manufacturing, Pharmaceutical, Construction, Education, Information technology
- Artifacts: Russian-speaking authors
This post is an update about the operational status of the campaign described in the original “Crouching Yeti” report.
Since the beginning of the research, we’ve been monitoring some of the C2 servers used by the components used in the attack – the Havex Trojan, the Sysmain Trojan and the ClientX backdoor. The following analysis is based on data gathered until March 04, 2015
C2 and victims:
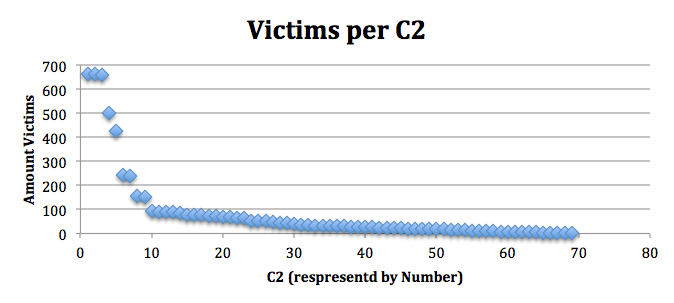
Overall, we successfully monitored 69 C2 server (unique domains), receiving hits from 3699 victims (unique IDs of the Trojan/backdoor) connecting from 57796 different IP addresses. We gathered four additional C2s since the publication of the first report (65 in the last report).
Based on the graph below, the top five C2 servers share most of the unique victims:
Although the trendline shows a decreasing number of hits on the C2, there are still >1.000 unique victim connections per day. These top five C2s with most of the victims coincides with the activity analyzed in the previous research and publication.
Another interesting figure is the number of hits by date which shows a decreasing trend:
The following figure shows the entire picture regarding Crouching Yeti victim country distribution including all the malware (Havex, ClientX,Sysmain) reporting to the C2s on which we have visibility. The graph contains the total dataset (inluding data for the previous report as well as the gathered during this period) and contains all the unique IP addresses observed. Be aware that there are some unique IDs using several IP addresses probably pertaining to infected computers used by travellers.
This shows the big (and updated) picture regarding Crouching Yeti victims by country. Spain, Poland and Greece are in the Top 3. Japan and especially the United States have significantly reduced position (less victims) since the last report, contrary to Poland and Italy that increased position remarkably (more victims reporting to the C2).
 An additional representation of victim country distribution including the full dataset (all countries) :
An additional representation of victim country distribution including the full dataset (all countries) :
Malware:
The most widely used Trojan on these C2 server is Havex with 3375 unqiue victims. Sysmain counts 314 and ClientX 10 (as in the last year’s report). For Havex, version 024 is still the most widespread, followed by version 043. This is consistent with the trend observed in our last publication.
The following two graphs show the distribution of victims per malware type. We decided to divide the identified versions in two groups for purposes of clarity. The series names Report contains the data published in the first Crouching Yeti release (blue) and the Update (red) series contains the data analyzed.
During this period, the first subset shows an increase for almost all the included versions except for Havex-038 and Havex-01D which showed bigger activity in the first Crouching Yeti release . On the other hand, Havex-043 has the most significant increase during this period.
For the second subset, the picture looks pretty similar (global increase) except for Havex-01d which shows a decrease during this period.
Already before and also after the announcements around this actor other researcher digged into. Therefore the datasets are cleaned but may still include few research based non-victim systems.
The following graphs shows the operating system distribution amongst Havex victims during this period:
Apart from the increase of the category “unknown”, there are no substantial differences when comparing the data analyzed in the first report :
In order to complement the data from the C2, we extracted some stats for the most relevant Trojans used by the Crouching Yeti operators. Almost all of them shows a residual impact during 2015. Nevertheless, we notice some very specific peaks during this month, especially for the Trojan.Win32.Ddex verdict. This component is a simple downloader with the functionality similar to the Havex component. All the detections are located within the Russian Federation.
In conclusion, the data analyzed during this period show us that Crouching Yeti’s impact continues to increase in terms of infected victims reporting to the C2s, although internal data from KSN shows a different picture (residual number of infections). In this update, we did not see relevant changes in the infrastructure or in the C2 activity.
Taking into account the nature of this threat actor and the operational status of the infrastructure, it is likely the operators already switched infrastructure, techniques and targets.
We will continue to track this threat actor and providing updates accordingly.





























Yeti still Crouching in the Forest