
Now these worms come as little surprise. Twitter has had a number of security issues recently.
The worm is not particularly complex in the vulnerability it is exploiting.
The original author? A bored 17 year old who had nothing better to do over the Easter weekend.
A story like this is clearly reminiscent of the malware landscape ten years ago – the malware is noisy and annoying rather than a serious threat as no user credentials are currently being stolen.
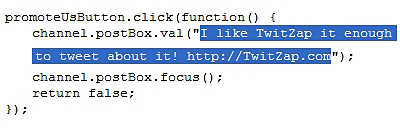
Yesterday, while watching what was going on Twitter I noticed a lot of tweets about twitzap.Suspecting this was a worm I did some digging and found that it wasn’t.It turned out this was a separate service with a nice “promote us” button that made a Twitter user post a status update promoting the service.
What do you have to do to activate it? Click on the button – and it sends a promotional update to your Twitter account!
A quick search on the net revealed that this service only started receiving attention this Monday.
Given the XSS worm, I think the promotion of this service could have been a whole lot better.
Also in response to the new XSS-Worms some web services have been created to supposedly protect the user. But again, these services ask users to just click on a link – while asking their friends to do the same. So your Twitter account gets updated, but if the service happens to be malicious, you could be sending off your account details to who knows where!
It’s actually this part of the social networks that scares me much more than an XSS-worm.
Web sites left and right that integrate with Twitter – and other networks – are asking users to use their services.Many people seem to be making use of them without too many questions, and without any proper means of verifying the integrity of these services.
What does this mean? Users are basically being trained to give up their credentials just like that.
XSS-Worms are not the real problem here, folks. We’re basically growing a new set of (extra) vulnerable users which will be more vulnerable to attack simply because they’re not asking any questions.




















Twitter worms aren’t the only threat